As you may known Oracle Java SE 6 major release will be end-of-life (EOL), or more precisely Oracle will no more release public updates, after February 2013. But Oracle customers could buy a commercial support for Oracle Java SE 6 in order to have support until December 2016 and more. Also Oracle will force update to JSE 7 through an auto-update process who will start in December 2012 (wasn’t I forced to update in July ?).
Oracle has release his new Java SE 7 major release since July 2011 and push users to update to JSE 7 since the release of JSE 6U33 minor release.
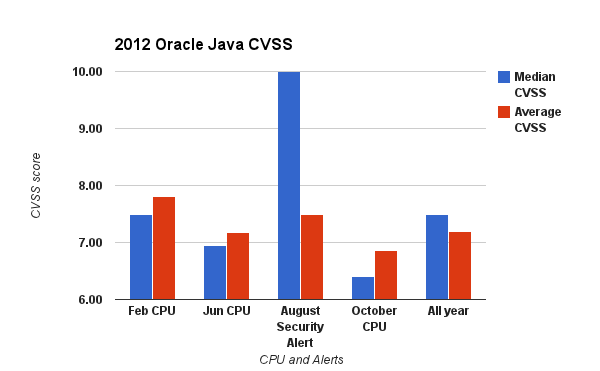
2012 is surely the year of Java vulnerabilities. On 58 vulnerabilities reported for year 2012 (February CPU, June CPU, CVE-2012-4681 Security Alert and October CPU), 2 (3.45%) of them were discovered exploited in the wild and 3 (5,17%) others were developed by white hat security researchers.
The median CVSS score for the 58 vulnerabilities was 7.5, 31 (53,45%) of them had a CVSS score upper than 7.0, 21 (36,21%) of them had a CVSS score upper to 4.0 to 6.9, and 6 (10,34%) of them had a CVSS score from 0.0 to 3.9.
CVE-2012-4681 was discovered exploited in the wild at end of August, targeting JSE 7 and JSE 6, and has force Oracle to push an out-of-band patch. CVE-2012-5076 was discovered exploited in the wild in November, targeting JSE 7, but was already patched during October CPU.
CVE-2012-0500, targeting JSE 7 and JSE 6, was fixed during February CPU, the 14th, and the vulnerability was integrated into Metasploit the 23 February after details disclosure by a white hat security researcher. CVE-2012-0507, JSE 7 and JSE 6, was also fixed during February CPU, the 14th, and the vulnerability was integrated into Metasploit the 29 March after details disclosure by a white hat security researcher. CVE-2012-1723, JSE 7 and JSE 6, was fixed during June CPU, the 12th, and the vulnerability was integrated into Metasploit the 9 July after details disclosure by a white hat security researcher.
On the 58 vulnerabilities patched in 2012 CPU’s and alerts, 100% of them were targeting JSE 7 and 84,48% (49) were targeting JSE 6. On the total 5 public exploits, 4 of them are targeting JSE 7 and 6, and the last one is targeting only JSE 7.
All the datas are available by clicking on the following link.
All the exploited, or disclosed, JSE vulnerabilities have been integrated into Exploit Kits like BlackHole, Gong Da, Kaixin, Cool, etc. If you take a look at the DeepEnd Research Common Exploit Kits 2012 Poster, contagio Exploit Pack tables and to my recent studies regarding Gong Da, Kaixin and Cool Exploit Kits, you can see the integration repartition. I also recommend you to read @kafeine blog in order to monitor EK evolutions.
| Black Hole EK | Cool EK | Gong Da EK | KaiXin EK | Phoenix EK | ProPack EK | |
| CVE-2012-0500 | X | |||||
| CVE-2012-0507 | X | X | X | X | ||
| CVE-2012-1723 | X | X | X | X | X | |
| CVE-2012-4681 | X | X | X | X | X | |
| CVE-2012-5076 | X | X | X | X | X |
JSE 7U10 has been released one week ago and has introduce some security enhancements. These security enhancements are probably an Oracle response to the uninstallation of all Oracle Java browser plug-ins by Apple in October, and includes:
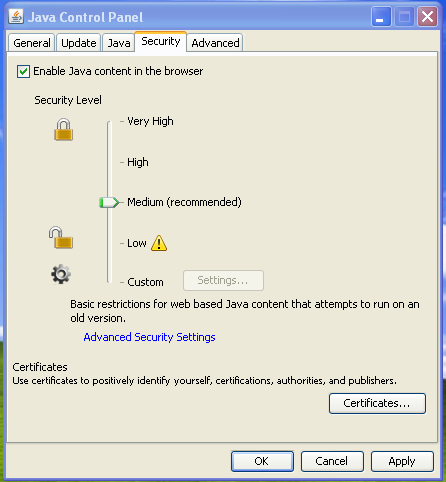
- The ability to disable any Java application from running in the browser. This mode can be set in the Java Control Panel or (on Microsoft Windows platform only) using a command-line install argument.
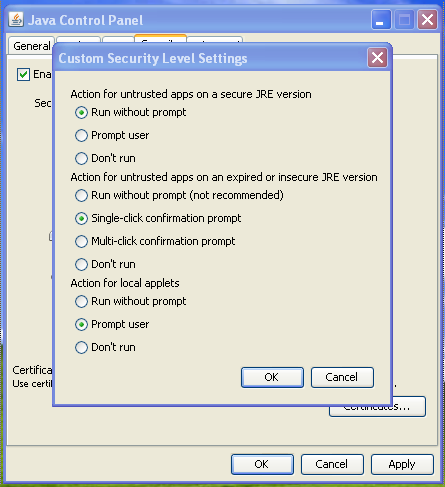
- The ability to select the desired level of security for unsigned applets, Java Web Start applications, and embedded JavaFX applications that run in a browser. Five levels of security are supported, plus a custom security level settings. This feature can be set in the Java Control Panel or (on Microsoft Windows platform only) using a command-line install argument.
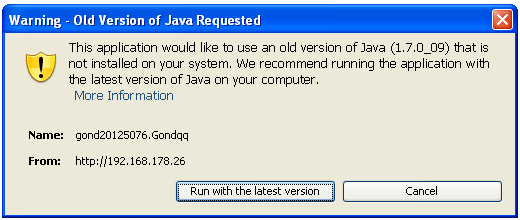
- New dialogs to warn you when the JRE is insecure (either expired or below the security baseline) and needs to be updated.
Take care in some upgrade cases from JSE 6 to JSE 7, the Java Control Panel has disappear from the Windows Control Panel. If it is the case, you have to explore C:\Program Files\Java\jre7\bin Windows folder and execute javacpl.exe binary.
Regarding the security levels, the five levels are:
- Custom: You can customize all the security settings based on you’re needs.
- Low: Most unsigned Java apps in the browser will run without prompting unless they request access to a specific old version or to protected resources on the system.
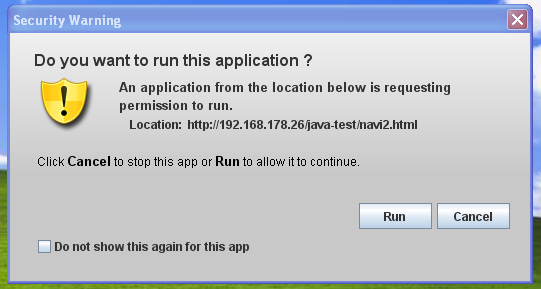
- Medium: Default security level. Unsigned Java apps in the browser will run without prompting only if the Java version is considered secure (screenshot bellow). You will be prompted if an unsigned app requests to run on an old version of Java.
- High: You will be prompted before any unsigned Java app runs in the browser (screenshot bellow).
- Very High: You will be prompted before any Java app runs in the browser. If your version of Java is insecure, unsigned apps will not run.
Java SE 7 is really immature, regarding the number of vulnerabilities and existing bugs, but Oracle don’t give user the choice. You have to migrate to JSE 7. So bye bye JSE 6.


Nice article comparing security of Java 6 and Java 7.
Two things you did not take into account:
1) Every Java CPU since Java 7 was released has fixed at least one CVE 10 vulnerability in Java 6 that can be exploited with pure Java without any memory corruptions. Therefore, there was no Java CPU that posed a greater risk to Java 7 than to Java 6. The fact that the badguys chose to exploit a Java 7 flaw in the latest CPU and not one of the Java 6 flaws may be caused either by this flaw being especially easy to exploit, or by the fact that most users have either upgraded or are on an old enough Java 6 version anyway so that old exploits like CVE-2012-1723 (affecting *every* Java 1.4/1.5 ever released as well!) could have been used against these targets.
2) The Java 6 plugin uses an old VC runtime DLL which is not ASLR enabled and has therefore “useful” properties for exploiting memory corruption based browser vulnerabilities outside of Java on Windows Vista or later when the plugin is loaded in the browser (JRE6 ROP Chain). While not a vulnerability on its own, you can mitigate this by upgrading to the Java 7 plugin which uses a more recent VC runtime DLL (or by uninstalling Java of course).
Hi mihi,
First at all thank you for your comment and complementary informations.
1) I completely agree with you on your points 🙂
2) Thanks for the advise !
RT @eromang: Bye Bye #Oracle #Java SE 6, #Security Enhancements in Java SE 7U10 http://t.co/WDW5keu6 #infosec