If you have download for free the ArcSight Logger L750MB version, follow the installation guideline under Centos and install Windows Snare with ArcSight Syslog SmartConnector, you have now an operational lab or production environment. In this post we will describe you some SmartConnector commands and features. These commands and features are not documented in the provided ArcSight Logger L750MB documentation.
Starting the SmartConnector
If you don’t have specify, during the setup, to run the SmartConnector as a service, you will ne to start it manually. To start the SmartConnector you need to go in the “$ARCSIGHT_HOME/current/bin” directory and execute the “arcsight” script for Linux, or “arcsight.bat” script under Windows, with the following argument.
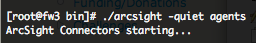
Once started, to confirm that the SmartConnector is working properly, you will have to check these outputs.
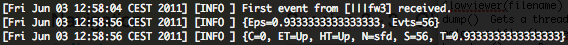
“Eps” will give you the actual EPS throughput, and “Evts” the total number of events how have been processed by the SmartConnector. “ET” and “HT” should have twice the “Up” value in order to validate the the SmartConnector connexion with the Logger is working properly. If they are any communication troubles between the SmartConnector and the Logger you will have these kind of outputs.
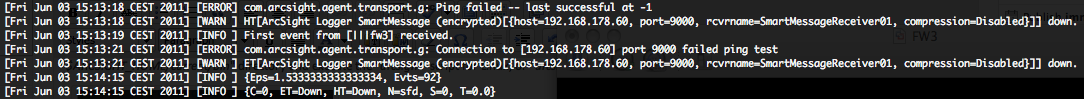
Checking SmartConnector availability
To valide that the SmartConnector is up and running, you can use the following command.
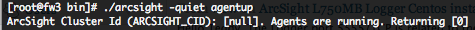
If the SmartConnector is down, you will have this result.
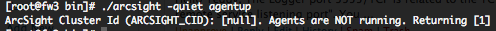
This command will not validate that the communication between the SmartConnector and the Logger is up and running.
Restarting the SmartConnector
To restart the SmartConnector you will have to use the following command.
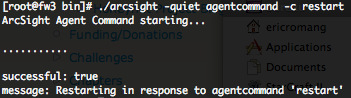
Stopping the SmartConnector
If you have start the SmartConnector in the standalone mode, a simple CTRL+C will terminate the activities. But you can also stop the activities with the following command :
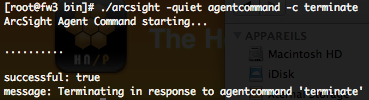
Checking SmartConnector status
To check the complete SmartConnector status use the following command.
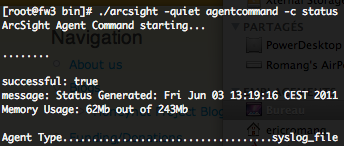
The output will provide you some useful informations about the SmartConnector activities (memory usage, agent type, agent version, processed events, EPS, last event processed date, etc.)
Checking SmartConnector DNS resolution
To verify that the SmartConnector is able to do DNS resolution you can execute the following command.
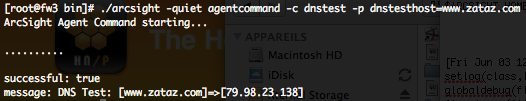
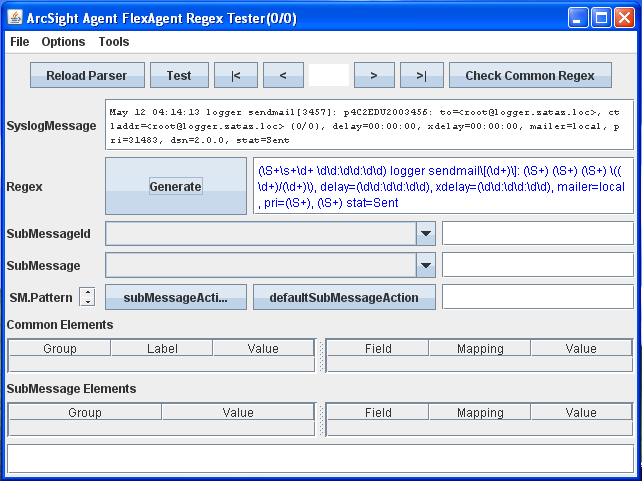
ArcSight Agent FlexAgent Regex Tester
ArcSight provide, with the SmartConnector, a tool how will permit you to create and test regex for your logs. SmartConnectors delivered for ArcSight Logger L750MB will not allow you to add FlexConnectors (custom agents), but you can still use this regex GUI for personal purposes. To start the regex GUI execute the following command.
For example, I have test the regex tool, with the following postfix log entry.
May 12 04:14:13 logger sendmail[3457]: p4C2EDU2003456: to=<[email protected]>, ctladdr=<[email protected]> (0/0), delay=00:00:00, xdelay=00:00:00, mailer=local, pri=31483, dsn=2.0.0, stat=Sent
The regex tester will provide you a solution on how to parse this log.