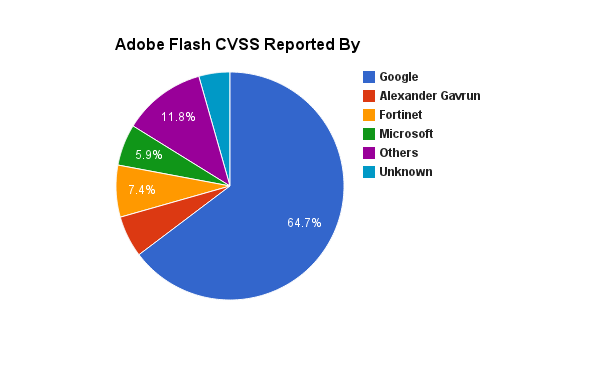
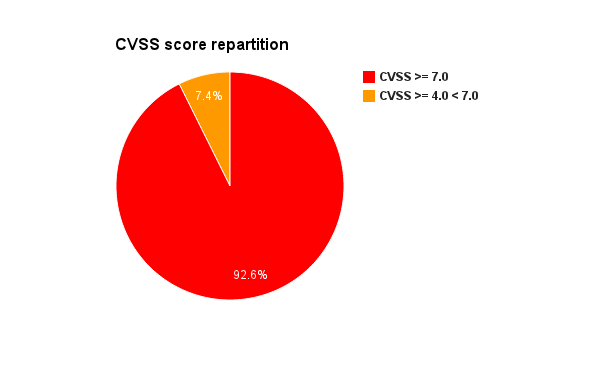
Microsoft has release, the 8 January 2013, during his January Patch Tuesday, two updated security advisories and seven security bulletins. On the seven security bulletins two of them has a Critical security rating.
Microsoft Security Advisory 973811
MSA-973811,released during August 2009, has been updated. The security advisory is regarding updates for Extended Protection for Authentication. Update v1.14 will provide more informations in the FAQ and Suggested Actions with information about attacks against NTLMv1 and LAN Manager network authentication. Applying Microsoft “Fix it“, for Windows XP or Windows Server 2003, enables NTLMv2 settings in order to take advantage of Extended Protection for Authentication.
Microsoft Security Advisory 2755801
MSA-2755801,released during September 2012, has been updated. The security advisory is regarding updates for vulnerabilities in Adobe Flash Player in Internet Explorer 10. Update KB2796096 has been released for supported editions of Windows 8, Windows Server 2012, and Windows RT. The update addresses the vulnerabilities described in Adobe Security bulletin APSB13-01.
MS13-001 – Vulnerability in Windows Print Spooler Components Could Allow Remote Code Execution
MS13-001 security update, classified as Critical, allowing remote code execution, is the fix for one privately reported vulnerability. CVE-2013-0011 has a 10.0 CVSS base score and was discovered and privately reported by un unknown security researcher.
Affected software are:
- Windows XP Service Pack 3
- Windows XP Professional x64 Edition Service Pack 2
- Windows Server 2003 Service Pack 2
- Windows Server 2003 x64 Edition Service Pack 2
- Windows Vista Service Pack 2
- Windows Vista x64 Edition Service Pack 2
- Windows Server 2008 for 32-bit Systems Service Pack 2
- Windows Server 2008 for x64-based Systems Service Pack 2
- Windows 8 for 32-bit Systems
- Windows 8 for 64-bit Systems
- Windows Server 2012
- Windows RT
MS13-002 – Vulnerabilities in Microsoft XML Core Services Could Allow Remote Code Execution
MS13-002 security update, classified as Critical, allowing remote code execution, is fixing two privately reported vulnerabilities. CVE-2013-0006 has a 9.3 CVSS base score and was discovered and privately reported by an unknown security researcher. CVE-2013-0007 has a 9.3 CVSS base score and was discovered and privately reported by Nicolas Gregoire of Agarri, working with VeriSign iDefense Labs.
Affected softwares are:
- Windows XP Service Pack 3
- Windows XP Professional x64 Edition Service Pack 2
- Windows Server 2003 Service Pack 2
- Windows Server 2003 x64 Edition Service Pack 2
- Windows Vista Service Pack 2
- Windows Vista x64 Edition Service Pack 2
- Windows Server 2008 for 32-bit Systems Service Pack 2
- Windows Server 2008 for x64-based Systems Service Pack 2
- Windows 7 for 32-bit Systems
- Windows 7 for 32-bit Systems Service Pack 1
- Windows 7 for x64-based Systems
- Windows 7 for x64-based Systems Service Pack 1
- Windows Server 2008 R2 for x64-based Systems
- Windows Server 2008 R2 for x64-based Systems Service Pack 1
- Windows 8 for 32-bit Systems
- Windows 8 for 64-bit Systems
- Windows Server 2012
- Windows RT
MS13-003 – Vulnerabilities in System Center Operations Manager Could Allow Elevation of Privilege
MS13-003 security update, classified as Important, allowing elevation of privilege, is fixing two privately reported vulnerabilities. CVE-2013-0009 has a 4.3 CVSS base score and was discovered and privately reported by an anonymous security researcher. CVE-2013-0010 has a 4.3 CVSS base score and was discovered and privately reported by Andy Yang of Stratsec.
Affected softwares are:
- Microsoft System Center Operations Manager 2007 Service Pack 1
- Microsoft System Center Operations Manager 2007 R2
MS13-004 – Vulnerabilities in .NET Framework Could Allow Elevation of Privilege
MS13-004 security update, classified as Important, allowing elevation of privilege, is fixing four privately reported vulnerabilities. CVE-2013-0001 has a 7.1 CVSS base score and was discovered and privately reported by Jon Erickson of iSIGHT Partners Global Vulnerability Partnership. CVE-2013-0002 has a 9.3 CVSS base score and was discovered and privately reported by Vitaliy Toropov, working with Tipping Point’s Zero Day Initiative. CVE-2013-0003 has a 9.3 CVSS base score and was discovered and privately reported by Vitaliy Toropov, working with Tipping Point’s Zero Day Initiative. CVE-2013-0004 has a 9.3 CVSS base score and was discovered and privately reported by James Forshaw of Context Information Security.
Affected softwares are:
- Windows XP Service Pack 3
- Windows XP Professional x64 Edition Service Pack 2
- Windows Server 2003 Service Pack 2
- Windows Server 2003 x64 Edition Service Pack 2
- Windows Vista Service Pack 2
- Windows Vista x64 Edition Service Pack 2
- Windows Server 2008 for 32-bit Systems Service Pack 2
- Windows Server 2008 for x64-based Systems Service Pack 2
- Windows 7 for 32-bit Systems
- Windows 7 for 32-bit Systems Service Pack 1
- Windows 7 for x64-based Systems
- Windows 7 for x64-based Systems Service Pack 1
- Windows Server 2008 R2 for x64-based Systems
- Windows Server 2008 R2 for x64-based Systems Service Pack 1
- Windows 8 for 32-bit Systems
- Windows 8 for 64-bit Systems
- Windows Server 2012
- Windows RT
MS13-005 – Vulnerability in Windows Kernel-Mode Driver Could Allow Elevation of Privilege
MS13-005 security update, classified as Important, allowing elevation of privilege, is fixing one privately reported vulnerability. CVE-2013-0008 has a 6.9 CVSS base score and was discovered and privately reported by an unknown security researcher.
Affected softwares are:
- Windows Vista Service Pack 2
- Windows Vista x64 Edition Service Pack 2
- Windows Server 2008 for 32-bit Systems Service Pack 2
- Windows Server 2008 for x64-based Systems Service Pack 2
- Windows 7 for 32-bit Systems
- Windows 7 for 32-bit Systems Service Pack 1
- Windows 7 for x64-based Systems
- Windows 7 for x64-based Systems Service Pack 1
- Windows Server 2008 R2 for x64-based Systems
- Windows Server 2008 R2 for x64-based Systems Service Pack 1
- Windows 8 for 32-bit Systems
- Windows 8 for 64-bit Systems
- Windows Server 2012
- Windows RT
MS13-006 – Vulnerability in Microsoft Windows Could Allow Security Feature Bypass
MS13-006 security update, classified as Important, allowing security feature bypass, is fixing one privately reported vulnerability. CVE-2013-0013 has a 5.8 CVSS base score and was discovered and privately reported by Kenichiro Katayama.
Affected softwares are:
- Windows Vista Service Pack 2
- Windows Vista x64 Edition Service Pack 2
- Windows Server 2008 for 32-bit Systems Service Pack 2
- Windows Server 2008 for x64-based Systems Service Pack 2
- Windows 7 for 32-bit Systems
- Windows 7 for 32-bit Systems Service Pack 1
- Windows 7 for x64-based Systems
- Windows 7 for x64-based Systems Service Pack 1
- Windows Server 2008 R2 for x64-based Systems
- Windows Server 2008 R2 for x64-based Systems Service Pack 1
- Windows 8 for 32-bit Systems
- Windows 8 for 64-bit Systems
- Windows Server 2012
- Windows RT
MS13-007- Vulnerability in Open Data Protocol Could Allow Denial of Service
MS13-007 security update, classified as Important, allowing denial of service, is fixing one privately reported vulnerability. CVE-2013-0005 has a 7.8 CVSS base score and was discovered and privately reported by an anonymous security researcher.
Affected softwares are:
- Windows XP Service Pack 3
- Windows XP Professional x64 Edition Service Pack 2
- Windows Server 2003 Service Pack 2
- Windows Server 2003 x64 Edition Service Pack 2
- Windows Vista Service Pack 2
- Windows Vista x64 Edition Service Pack 2
- Windows Server 2008 for 32-bit Systems Service Pack 2
- Windows Server 2008 for x64-based Systems Service Pack 2
- Windows 7 for 32-bit Systems
- Windows 7 for 32-bit Systems Service Pack 1
- Windows 7 for x64-based Systems
- Windows 7 for x64-based Systems Service Pack 1
- Windows Server 2008 R2 for x64-based Systems
- Windows Server 2008 R2 for x64-based Systems Service Pack 1
- Windows 8 for 32-bit Systems
- Windows 8 for 64-bit Systems
- Windows Server 2012