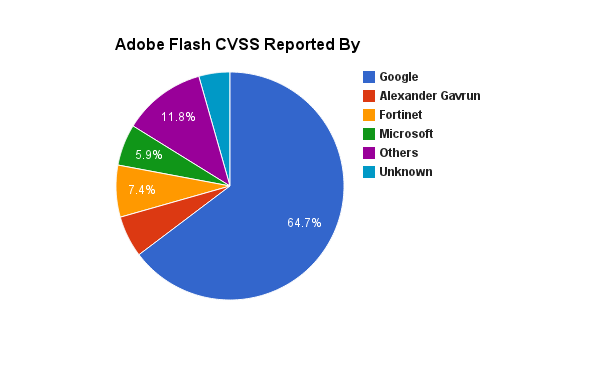
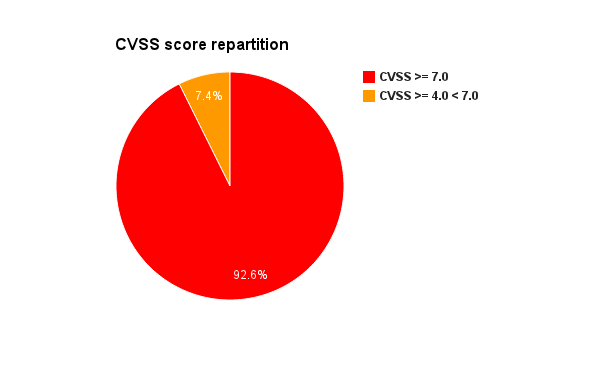
Microsoft has release, the 11 December 2012, during his December Patch Tuesday, two updated security advisories and seven security bulletins. On the seven security bulletins five of them has a Critical security rating.
Microsoft Security Advisory 2755801
MSA-2755801,released during September 2012, has been updated. The security advisory is regarding updates for vulnerabilities in Adobe Flash Player in Internet Explorer 10. Update KB2785605 has been released for supported editions of Windows 8, Windows Server 2012, and Windows RT. The update addresses the vulnerabilities described in Adobe Security bulletin APSB12-27.
Microsoft Security Advisory 2749655
MSA-2749655, release during October 2012, has been updated. The security advisory is regarding “Compatibility Issues Affecting Signed Microsoft Binaries” and the update added the KB2687627 and KB2687497 updates described in MS12-043, the KB2687501 and KB2687510 updates described in MS12-057, the KB2687508 update described in MS12-059, and the KB2726929 update described in MS12-060 to the list of available rereleases.
MS12-077 – Cumulative Security Update for Internet Explorer
MS12-077 security update, classified as Critical, allowing remote code execution, is the fix for three privately reported vulnerabilities. CVE-2012-4781 has a 0.0 CVSS base score (surely an error) and was discovered and privately reported by Rosario Valotta. CVE-2012-4782 has a 10.0 CVSS base score and was discovered and privately reported by Rosario Valotta. CVE-2012-4787 has a 10.0 CVSS base score and was discovered and privately reported by Fermin J. Serna of Google Inc.
Affected software are:
- Internet Explorer 6
- Internet Explorer 7
- Internet Explorer 8
- Internet Explorer 9
- Internet Explorer 10
MS12-078 – Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Remote Code Execution
MS12-078 security update, classified as Critical, allowing remote code execution, is fixing two vulnerabilities. CVE-2012-2556 has a 9.3 CVSS base score and was publicly disclosed. CVE-2012-4786 has a 10.0 CVSS base score and was discovered and privately reported by Eetu Luodemaa and Joni Vähämäki of Documill, working with the Chromium Security Rewards Program.
Affected softwares are:
- Windows XP Service Pack 3
- Windows XP Professional x64 Edition Service Pack 2
- Windows Server 2003 Service Pack 2
- Windows Server 2003 x64 Edition Service Pack 2
- Windows Vista Service Pack 2
- Windows Vista x64 Edition Service Pack 2
- Windows Server 2008 for 32-bit Systems Service Pack 2
- Windows Server 2008 for x64-based Systems Service Pack 2
- Windows 7 for 32-bit Systems
- Windows 7 for 32-bit Systems Service Pack 1
- Windows 7 for x64-based Systems
- Windows 7 for x64-based Systems Service Pack 1
- Windows Server 2008 R2 for x64-based Systems
- Windows Server 2008 R2 for x64-based Systems Service Pack 1
- Windows 8 for 32-bit Systems
- Windows 8 for 64-bit Systems
- Windows Server 2012
- Windows RT
MS12-079 – Vulnerability in Microsoft Word Could Allow Remote Code Execution
MS12-079 security update, classified as Critical, allowing remote code execution, is fixing one privately vulnerability. CVE-2012-2539 has a 9.3 CVSS base score and was discovered and privately reported by an anonymous contributor, working with Beyond Security’s SecuriTeam Secure Disclosure program.
Affected softwares are:
- Microsoft Office 2003 Service Pack 3
- Microsoft Office 2007 Service Pack 2
- Microsoft Office 2007 Service Pack 3
- Microsoft Office 2010 Service Pack 1 (32-bit editions)
- Microsoft Office 2010 Service Pack 1 (64-bit editions)
- Microsoft Word Viewer
- Microsoft Office Compatibility Pack Service Pack 2
- Microsoft Office Compatibility Pack Service Pack 3
MS12-080 – Vulnerabilities in Microsoft Exchange Server Could Allow Remote Code Execution
MS12-080 security update, classified as Critical, allowing remote code execution, is fixing three vulnerabilities. CVE-2012-3214 has a 2.1 CVSS base score and is associated with Oracle Outside In Technology component fixed in Oracle October 2012 CPU. CVE-2012-3217 has a 2.1 CVSS base score and is associated with Oracle Outside In Technology component fixed in Oracle October 2012 CPU. CVE-2012-4791 has a 3.5 CVSS base score and was discovered and privately reported by unknown security researcher.
Affected softwares are:
- Microsoft Exchange Server 2007 Service Pack 3
- Microsoft Exchange Server 2010 Service Pack 1
- Microsoft Exchange Server 2010 Service Pack 2
MS12-081 – Vulnerability in Windows File Handling Component Could Allow Remote Code Execution
MS12-081 security update, classified as Critical, allowing remote code execution, is fixing one privately reported vulnerability. CVE-2012-4774 has a 10.0 CVSS base score and was discovered and privately reported by Lucas Apa of IOActive.
Affected softwares are:
- Windows XP Service Pack 3
- Windows XP Professional x64 Edition Service Pack 2
- Windows Server 2003 Service Pack 2
- Windows Server 2003 x64 Edition Service Pack 2
- Windows Vista Service Pack 2
- Windows Vista x64 Edition Service Pack 2
- Windows Server 2008 for 32-bit Systems Service Pack 2
- Windows Server 2008 for x64-based Systems Service Pack 2
- Windows 7 for 32-bit Systems
- Windows 7 for 32-bit Systems Service Pack 1
- Windows 7 for x64-based Systems
- Windows 7 for x64-based Systems Service Pack 1
- Windows Server 2008 R2 for x64-based Systems
- Windows Server 2008 R2 for x64-based Systems Service Pack 1
MS12-082- Vulnerability in DirectPlay Could Allow Remote Code Execution
MS12-082 security update, classified as Important, allowing remote code execution, is fixing one privately reported vulnerability. CVE-2012-1537 has a 9.3 CVSS base score and was discovered and privately reported by Aniway, working with VeriSign iDefense Labs.
Affected softwares are:
- Windows XP Service Pack 3
- Windows XP Professional x64 Edition Service Pack 2
- Windows Server 2003 Service Pack 2
- Windows Server 2003 x64 Edition Service Pack 2
- Windows Vista Service Pack 2
- Windows Vista x64 Edition Service Pack 2
- Windows Server 2008 for 32-bit Systems Service Pack 2
- Windows Server 2008 for x64-based Systems Service Pack 2
- Windows 7 for 32-bit Systems
- Windows 7 for 32-bit Systems Service Pack 1
- Windows 7 for x64-based Systems
- Windows 7 for x64-based Systems Service Pack 1
- Windows Server 2008 R2 for x64-based Systems
- Windows Server 2008 R2 for x64-based Systems Service Pack 1
- Windows 8 for 32-bit Systems
- Windows 8 for 64-bit Systems
- Windows Server 2012
MS12-083- Vulnerability in IP-HTTPS Component Could Allow Security Feature Bypass
MS12-083 security update, classified as Important, allowing security feature bypass, is fixing one vulnerability. CVE-2012-2549 has a 6.8 CVSS base score and was discovered and privately reported by an anonymous security researcher.
Affected softwares are:
- Windows Server 2008 for 32-bit Systems Service Pack 2
- Windows Server 2008 for x64-based Systems Service Pack 2
- Windows Server 2012