Twitt Metasploit plugin was developed, in ruby, by Carlos Perez, aka Dark Operator. This plugin permit you to send a Twitter direct message to a configured account when a Metasploit session is created or shutdown. Each message will contain informations about the related session.
Installation :
To install the Twitt Metasploit plugin on Ubuntu 10.04.1 LTS, you first need to update your Ruby Gem with the following commands (Thanks to Carlos, helping me to update gem).
sudo gem install rubygems-update cd /var/lib/gems/1.8/bin sudo ./update_rubygems
Then you will be install the needed Ruby Gem needed by the plugin.
sudo gem install twitter
After this, just download the twitt.rb script from Github and install the script in the Metasploit plugin directory, by default “/opt/metasploit3/msf3/plugins/“. Don’t forget to give the right user access to the script and launch Metasploit.
sudo msfconsole
Twitt plugin setup :
To setup the OAuth 1.0a plugin settings you first need a Twitter account, if you don’t have one. After you need to register the Twitt application in the Twitter Developers.
Don’t forget when you fill the form, to determine that the “Application Type” is “Client” and that the “Client” should have a “Read & Write” “Default Access Type“.
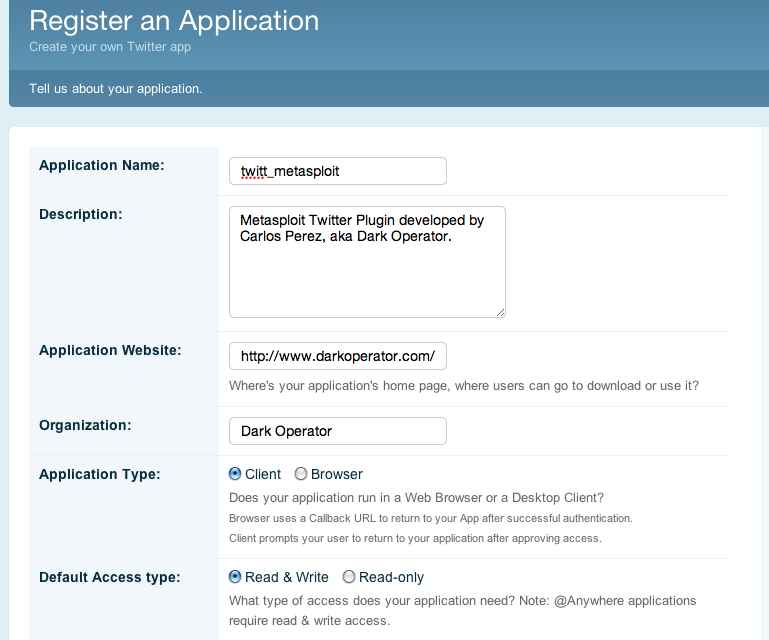
After the plugin registration on Twitter, you will need different configuration settings :
- Consumer key for the Metasploit Twitt plugin “twitt_set_consumer_key” command.
- Consumer secret for the Metasploit Twitt plugin “twitt_set_consumer_secret” command.
- Access Token (oauth_token) for the Metasploit Twitt plugin “twitt_set_oauth_token” command.
- Access Token Secret (oauth_token_secret) for the Metasploit Twitt plugin “twitt_set_oauth_token_secret” command.
- Your Twitter username account for the Metasploit Twitt plugin “twitt_set_user” command.
In Metasploit load the plugin and configure it by the following commands :
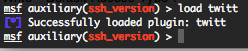
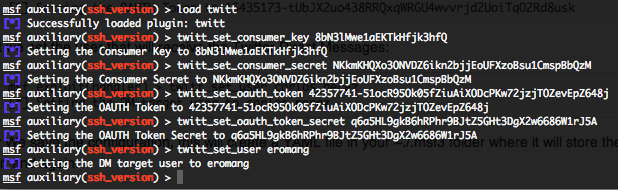
Just replace all the screenshot configuration settings with your settings 🙂
Then save the configuration with the “twitt_save” command :
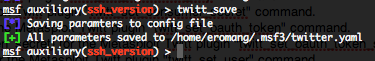
As you can see all the configuration settings are save into a “.yaml” file.
If you want to see all the configuration settings from the “.yaml” file just type the “twitt_show_parms” command.
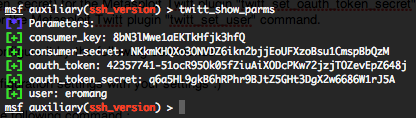
Then to start the twit plugin, run “twitt_start” command.
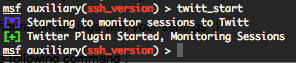
Now each time you will have a new Metasploit session, or if a session is shutdown, a direct message will be send to the configured twitter account. Here under a demonstration video.