As mentioned by Symantec & Seculert, a spear phishing campaign has involved a fake Mandiant APT1 PDF report, a report published by Mandiant earlier this week (APT1: Exposing One of China’s Cyber Espionage Units). This fake PDF was used in targeted attacks against Japanese entities and exploiting code for Adobe Acrobat and Reader Remote Code Execution Vulnerability (CVE-2013-0641).
Despite the analysis of Symantec, I can confirm you that the PDF is dropping malware onto the computer.
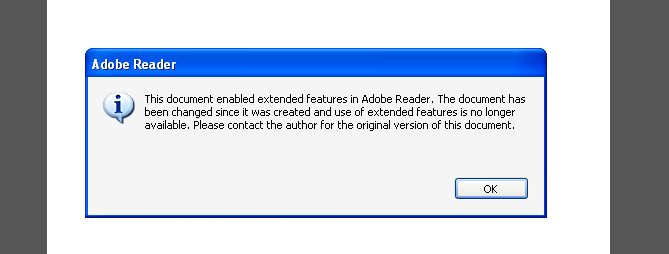
PDF file name is “Mandiant.pdf” with 2a42bf17393c3caaa663a6d1dade9c93 hash (23 / 46 on VirusTotal). Once opened an error message is displayed.
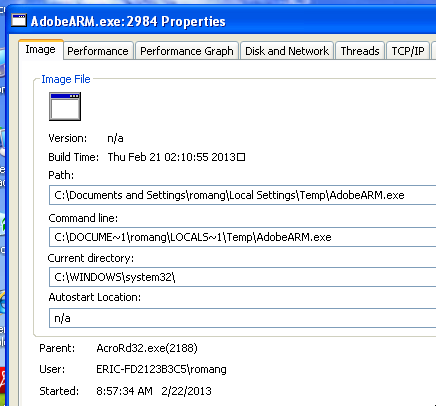
After ignoring this error message the vulnerability is exploited and drop “AdobeARM.exe” (41915b34fc50ffdd2a6a0969e3f55ff1) in “C:\Documents and Settings\<USER>\Local Settings\Temp” Windows folder. Chinese simplified ressource language is used for this executable.
“AdobeARM.exe” is connecting to domain name “www.shounkaku.co.jp“, a legit website, and to folder “/space/fsjd-ge3234c4d61033.gif“. The file is actually no more existing.
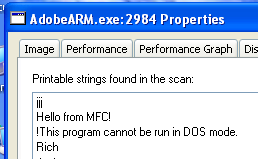
Interesting strings in “AdobeARM.exe” are “Hello from MFC!” (Military Force of China ?).
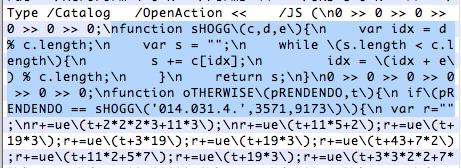
Regarding the PDF, the embedded JavaScript seem to be the same as in the original version of 0day (sHOGG, oTHERWISE, and others functions and variables names). So it seem that some guys have successfully weaponize the original version of 0day.
Here under a demonstration video of the exploitation.