Every one of you know Remote File Inclusion vulnerability, how permit to include a remote file usually through a PHP script on the Web application. This remote file contain some code how will be executed in the context of the server and permit for example to gather informations, execute code and compromise the Web server.
An typical RFI attack is to target Web applications how are vulnerable to an RFI. For example the actual most targeted RFI vulnerability is “MODx CMS snippet.reflect.php reflect_base CVE-2008-5938“.
Same as Metalica, bad guys are seeking and then destroying. But before destroying, bad guys seeking potential targets with search engines (Google, Yahoo, Live, Ask, etc.) and if some results are matching, they then try to see if the Web application URL is vulnerable or not. Same as a submarine active sonar, the remotely included code will ping the potential vulnerable URL, and if this URL is vulnerable the Web application will do an code echo reply. PS : Special dedicated to :
echo("FeeL"."CoMz");
Now the bad guys knowing that the Web application URL is vulnerable, they will gather more informations about the Web application and server environment. Following the responses to the informations gathering, the bad guys will decide which kind of infections they could apply and how depth the infections would be. The critical informations that the bad guys will look are for example :
- Is PHP safe mode set to “on” ?
- What is the OS hosting the vulnerable application ?
- Version of the kernel, if applicable ?
- What is the user running the web application, most of time httpd or apache.
- What are the permissions of the Web application directories, read only, writable ?
If PHP safe mode is set to “on”, the bad guys will only use the vulnerable Web application and server as repository for some scripts, most of time the “ping code” and the “informations gathering code“.
If PHP safe mode is set to “off”, then the bad guys will begin to remote upload, on the server, more scripts. Mainly RFI viral packs containing these capabilities :
- IRC Command & Control bot module
- Search engines targets seeker module
- RFI code ping scan script
- RFI code echo reply listener module
- Informations gathering script
- IRC channels & words spying module
- DOS & DDOS module
- Portscanner module
- Fake speaking & answering IRC bots module
- Google bypasser module
- PHP shells script
What is really important to understand is that every parts of these RFI viral packs could be decentralized on other compromised servers, and controlled by different IRC Command & Control servers . And now, longer the first initial Web application and server is compromised, longer this infected host will participate to increase the size of the RFI botnet.
We will use a example, a very old friend of our HoneyNet, lunched in February 2009. We will call our old friend “RFI n°4” (Nooo, I’m not an number….) and provide you his ID card.
- RFI ID : 4
- RFI IP : 213.158.72.68
- RFI FQDN : virtual.interfree.it
- RFI Country : Italy
- RFI Vhost : brej.interfree.it
- RFI URL : http://brej.interfree.it/id.jpg??
- Number of events generated by n°4 : 1935
- Number of source IPs how are calling the RFI URL : 112
- RFI first seen : 2009-02-15 20:54:58
- RFI last seen : 2010-05-26 21:48:09
- RFI life time : 465 day’s
Hu, 465 days old … my n°4 friend is very old and has a lot of friends how are visiting him (112 source IPs). The number of events is quiet relative, cause 465 day’s for only generating 1935 events, my n°4 friend you could do better, maybe your master is a lazy guy. All you friends are trying different attacks, with your help, against our HoneyNet.
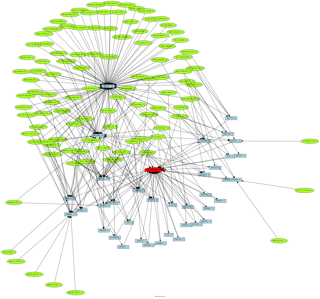
What is interesting n°4, is that some of your friends are also RFI infected, and all together you create a big family linked together (RFI botnet).
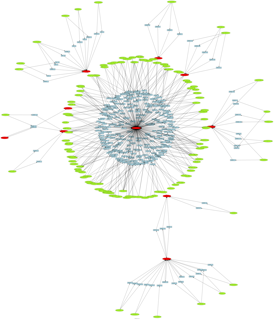
Another possible visualization is to see month by month the activities turning around our n°4 RFI friend. RFI n°4 is indicated in green colors, source IPs how are not also RFI are indicated in orange colors and source IPs how are also RFI are indicated in red flame colors.
[nggallery id=4]