Oracle has provide his Java Critical Patch Update (CPU) for April 2013 who has been released on Tuesday, April 16. On the 42 security vulnerabilities fixed in this CPU, 39 of them may be remotely exploitable. The highest CVSS Base Score for vulnerabilities in this CPU is 10.0.
This update fix the vulnerabilities exploited by James Forshaw (tyranid), Joshua J. Drake and VUPEN Security during Pwn20wn 2013. But this update is also fixing vulnerabilities reported by Adam Gowdiak of Security Explorations and other security researchers.
As you may know Oracle is using CVSS 2.0 (Common Vulnerability Scoring System) in order to score the reported vulnerabilities. But as you also may know security researchers disagree with the usage of CVSS by Oracle. Oracle play with CVSS score by creating a “Partial+” impact rating how don’t exist in CVSS 2.0, and by interpreting the “Complete” rating in a different way than defined in CVSS 2.0.
Affected products are:
- JDK and JRE 7 Update 17 and earlier
- JDK and JRE 6 Update 43 and earlier
- JDK and JRE 5.0 Update 41 and earlier
- JavaFX 2.2.7 and earlier
Proposed updates are:
- JDK and JRE 7 Update 21
- JDK and JRE 6 Update 45
- JDK and JRE 5.0 Update 43
- JavaFX 2.2.21
19 (45,24%) of the vulnerabilities have a CVSS base score of 10.0, 28 (66,67%) of the vulnerabilities have a high CVSS base score (CVSS => 7.0), 13 (30,95%) of the vulnerabilities have a medium CVSS base score (CVSS >= 4.0 < 7.0) and 1 (2,38%) of the vulnerabilities has a low CVSS base score (CVSS < 4.0). Also 25 (59,52%) of the vulnerabilities affects Java SE 6 and 42 (100%) of the vulnerabilities are affecting Java SE 7.
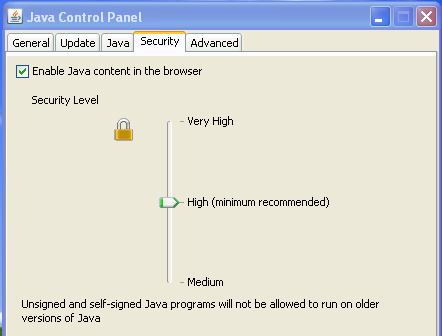
Also some modifications have been done in the Security Levels provided by Oracle. Previously five levels were existing (Very-High, High, Medium, Low and Custom), in the new provided version only three levels are still existing (Very-High, High and Medium).
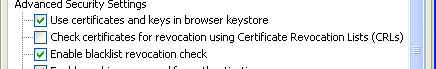
But, there is always a but with Oracle, they don’t seem to have enable, by default, the check for revocation using Certificate Revocation Lists (CRLs) despite that some bad guys are using valid stollen and revoked certificates to sign malware’s.
So we advise you to update asap, enable the CRL check, if you still have Oracle Java plug-in installed !
RT @eromang: Oracle Java Critical Patch Update April 2013 Review http://t.co/p07E95QR8I
Oracle Java Critical Patch Update April 2013 Review: http://t.co/CPYUjdb7zI #infosec
RT @eromang Oracle Java Critical Patch Update April 2013 Review http://t.co/hGaXiUZAjz
RT @eromang: Oracle Java Critical Patch Update April 2013 Review http://t.co/p07E95QR8I
RT @eromang: Oracle Java Critical Patch Update April 2013 Review http://t.co/p07E95QR8I
GREAT
@eromang @Oracle @java Critical Patch Update April 2013 Review
http://t.co/5RQHEwNEVI