If you are working in computer security and still don’t have heard about the latest Adobe Flash 0days, aka CVE-2013-0633 and CVE-2013-0634, then you should change of job ! These vulnerabilities were found exploited in targeted attacks through spear phishing email messages targeting several industries including the aerospace one.
One of the e-email attached Word document was using the 2013 IEEE Aerospace Conference schedule, and another reported sample was related to online payroll system of ADP US company, to exploit CVE-2013-0633. I wrote a complete blog post regarding this campaign 2 weeks ago.
Adobe fixed the vulnerabilities in APSB13-04 the 7 February, but the vulnerabilities were not found massively exploited in Exploit Kits. Also there was a confusion, by anti-virus vendors and security researchers, regarding CVE-2013-0633 and CVE-2013-0634 detection. But as mentioned in Adobe APSB13-04 CVE-2013-0633 was only exploited by been embedded in Word documents and CVE-2013-0634 was exploited through HTML web pages and by been embedded in Word documents.
So as nobody as seen CVE-2013-0633 working outside a Word document, I will suppose that the vulnerability I discovered exploited in Gong Da exploit kit is potentially a fork of CVE-2013-0633 or could be CVE-2013-0634. Colleagues, you are welcome for comments 🙂
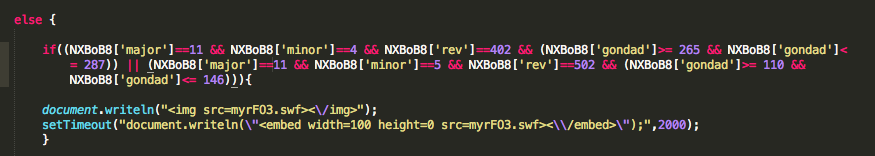
Here is the new code in Gong Da exploit kit.
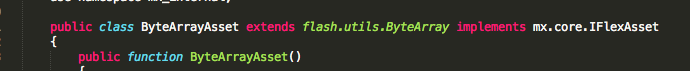
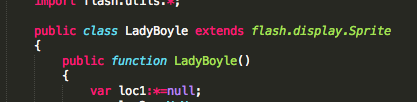
If you take a look at the ActionScript of “myrF03.swf” (506fe8f82ea151959c5160bc40da25b5) you will see some similarities with CVE-2013-0633, like the “ByteArrayAsset” mentioned by MalwareMustDie, or the well-known “LadyBoyle” function.
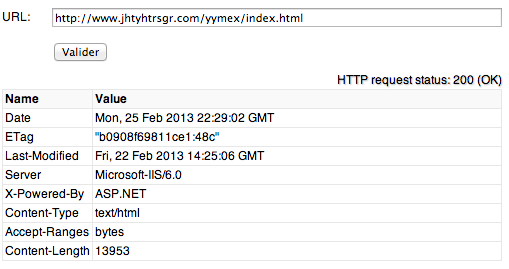
This new version was discovered on “hxxp://www.jhtyhtrsgr.com/yymex/index.html” a web site how is actually still online.
“jhtyhtrsgr.com” is hosted on 69.197.61.29, in US and this domain name was created the 22 Feb 2013 with registration informations located in China and the following contact “jing yan ([email protected]) – GuangMing yanjing“.
The “index.html” file containing JavaScript code obfuscated by “JSXX VIP JS Obfuscator“, but traditional traces if this obfuscator are no more available.
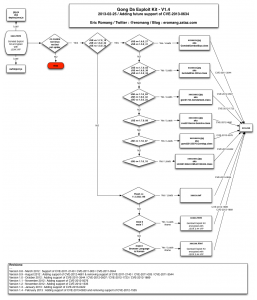
After de-obfuscation of the “index.html” file you can see that Gong Da Pack has involve to the following diagram.
Here under some information s regarding the different files:
- vQSopE2.jpg (aka CVE-2011-3544) : 10/46 on VirusTotal.com
- ulxzBc7.jpg (aka CVE-2012-0507) : 11/45 on VirusTotal.com
- MQnA3.jpg (aka CVE-2012-1723) : 18/46 on VirusTotal.com
- eATBNfg1.jpg (aka CVE-2012-4681) : 29/46 on VirusTotal.com
- tkPfaMz7.jpg (aka CVE-2012-5076) : 14/46 on VirusTotal.com
- iOiezo6.jpg (aka CVE-2013-0422): 19/46 on VirusTotal.com
- YPVTz8.html (aka CVE-2012-1889): 14/46 on VirusTotal.com
- vQSopE2.html (aka CVE-2012-1889): 12/46 on VirusTotal.com
- myrFO3.swf (aka a fork of
CVE-2013-0633CVE-2013-0634): 8/46 on VirusTotal.com
Here under a demonstration video of CVE-2013-0633 CVE-2013-0634 without been embeded in a Word document.
Updates:
After investigation from @unixfreaxjp, it seem that the exploited vulnerability is CVE-2013-0634 and not CVE-2013-0633.
Gong Da / Gondad Exploit Pack Add Flash CVE-2013-0634 Support http://t.co/w2t8VYt9oR
Gong Da / Gondad Exploit Pack Add Flash CVE-2013-0633 Support http://t.co/zZyPTVZkUY
Top story: Gong Da / Gondad Exploit Pack Add Flash CVE-2013-0633 Support http://t.co/iVdNo9a56y, see more http://t.co/SCq9wQNWf1
Top story: Gong Da / Gondad Exploit Pack Add Flash CVE-2013-0633 Support http://t.co/TqTh2tS6CL, see more http://t.co/MaI7ERX4GV
Gong Da / Gondad Exploit Pack Add Flash CVE-2013-0633 Support – http://t.co/rFsD3Fu54w
The mentioned sample myrFO3.swf is CVE-2013-0634 by definition indeed. It has the code exploitation of CVE-2013-0633 and found as stand alone SWF in the wild as direct web driven infector.
The sample hash: 506fe8f82ea151959c5160bc40da25b5
The image snapshot of the code: HERE
I thank you for Eric Romang’s big heart to share this sample to the public to let all understand why we must patch the Adobe advisory APSB13-04, Salute!
#MalwareMustDie! @unixfreaxjp
The Gong Da exploit has added “support” for two recent flash vulnerabilities. @eromang has the details http://t.co/FrWW28DSEn
Gong Da / Gondad Exploit Pack Add Flash CVE-2013-0633 Support
B! http://t.co/j3r4XsBA7R
#twihateb
#Malware Infector – Gong Da / Gondad Exploit Pack Add Flash #CVE-2013-0633 Support – http://t.co/tG5WLDkOgS by @eromang
Gong Da / Gondad Exploit Pack Add Flash CVE-2013-0633 Support http://t.co/93hv2xrCSW via @eromang
[EricRomang] Gong Da / Gondad Exploit Pack Add Flash CVE-2013-0633 Support http://t.co/g01MpfjQ5V
Gondad Exploit Pack Add Flash CVE-2013-0633: http://t.co/zwiFvtDRql