The 7 February, Adobe has issue security bulletin APSB13-04 for Adobe Flash Player, in order address two vulnerabilities, CVE-2013-0633 and CVE-2013-0634, exploited in the wild.
CVE-2013-0633 (CVSS base score of 9.3) is exploited by tricking a Windows user to open a Microsoft Word document containing a malicious Flash content. CVE-2013-0634 (CVSS base score of 9.3) is exploited by tricking an Apple OS X user to open a web page, containing a malicious Flash content, through Firefox or Safari. But this vulnerability is also exploited by tricking a Windows user to open a Microsoft Word document containing a malicious Flash content.
Affected products are :
- Adobe Flash Player 11.5.502.146 and earlier versions for Windows and Macintosh
- Adobe Flash Player 11.2.202.261 and earlier versions for Linux
- Adobe Flash Player 11.1.115.36 and earlier versions for Android 4.x
- Adobe Flash Player 11.1.111.31 and earlier versions for Android 3.x and 2.x
These vulnerabilities were discovered exploited in the wild:
- For CVE-2013-0633, by Sergey Golovanov and Alexander Polyakov of Kaspersky Labs
- For CVE-2013-0634, by Shadowserver Foundation, MITRE and Lockheed Martin CIRT
As described by Alienvault Labs and by FireEye, the vulnerabilities were exploited through spear phishing email messages targeting several industries including the aerospace one. One of the e-email attached file was using the 2013 IEEE Aerospace Conference schedule, and another reported sample was related to online payroll system of ADP US company.
Detailed analysis have been provided by Alienvault Labs, FireEye and Malware Must Die. All the analysis reported the following domain name ieee[.]boeing-job[.]com as C&C server.
boeing-job[.]com domain name was registered the 22 January 2013, through GoDaddy, with fake registration information’s.
The 5 February http://ieee[.]boeing-job[.]com sub domain was pointing to IP 108.62.10.13, AS15003 in US.
The 6 February http://boeing-job[.]com was pointing to IP 184.168.221.37, AS26496 in US, parking web page of GoDaddy.
But, they’re is always a but, if you take a look in Google you can find the IP address who was used for www.boeing-job[.]com.
This sub domain was pointing to a legit website http://www[.]grupo-gestion[.]com[.]ar, IP 200.123.160.138, AS16814 in Argentina.
By searching on urlQuery, you can find a submission, the 5 February, with this IP. And suprise this submission is regarding a “record.doc” document located in a “/adp/” directory. So we have the ADP word document. Also urlQuery is reporting an alert “FILE-OFFICE Microsoft Office Word with embedded Flash file transfer” regarding the “record.doc” document.
Now let analyze further this server used in the spear phishing campaign. By doing some researches on Google, you will quickly find that weak tools are present on the server and that these tools are freely accessible from Internet…. After some further analysis, we can find that an old default XAMPP installation is present on this server, and that bad guys have use this weakness in order to install PHP backdoor. The PHP backdoor were also not protected giving full access to the server.
The related “/adp/” directory is empty of the “record.doc” file and most of the server seem to have been cleaned.
But, I discovered an interesting “/jobs/” directory containing a well-known tool, JSbug statistics backend, used in previous drive-by attacks campaign. The contents of the backend allow us to see that a campaign was started since the 22 January by using www.boeing-job[.]com domain name.
Also, what is interesting, is that the XAMPP Apache log files were accessible from Internet, without restrictions.
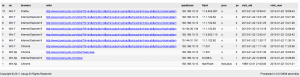
By doing some log analysis we can find the following information’s:
- “record.doc” file size was 563200 bytes.
- First, 200 Apache return code, access to “/adp/record.doc” file was recorded the 05/Feb/2013:07:12:24 -0300.
- “/adp/record.doc” file was removed from the server around the 08/Feb/2013 09:23:24 -0300.
- Around 300 accesses on the “record.doc” files were done during this timeframe. 42 the 5 February, 7 the 6 February, 89 the 7 February and 161 the 8 February.
- A PHP backdoor was present on the server since the 05/Nov/2012 and used multiple times.
- A second PHP backdoor was uploaded on the server the 8 February, at 08/Feb/2013 02:25:25 -0300 (surely used to remove the record.doc file). Why not using the first PHP backdoor ? Surely cause you are not the guy who has deposit the “record.doc” file and you don’t know the existence of the first PHP backdoor.
- The server was scanned during two days with Acunetix, starting the 02/Feb/2013 18:25:45 -0300
Additional analysis of the discovered “/jobs/” and JSbug backend directory provide the following interesting information’s:
- The “/jobs/” directory was first seen the 22/Jan/2013 06:12:44 -0300
- Installation of JSBug backend was done the 22/Jan/2013 06:13:16 -0300
- Additional files were installed in the “/jobs/” directory like “img/jquery-1.8.3.min.js“, “img/logo.gif“, “check.php”, “download.htm“, “download.php“, “img/download.css“, “img/ff_step1.png“, “img/ie_step3.png“, “img/ff_step2.png” and “NProtect.exe“. “check.php“, “download.htm“, “NProtect.exe” and “download.php” are no more present on the server.
By analysing the file remaining on the server, and used in a previous attack, who has start the 22 January, we can see the following files who reveal that a spear phishing campaign was done against Boeing employees, in order to trick them to install the “NProtect.exe” malware.

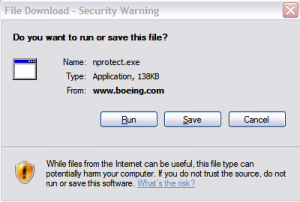
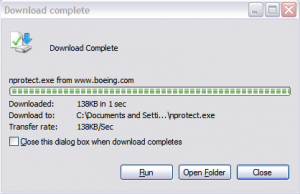


RT @eromang: http://t.co/FB3nqaJ8 Campaign and #Adobe #Flash #0days Additional Informations http://t.co/FDe22t5E #infosec
RT @eromang: http://t.co/FB3nqaJ8 Campaign and #Adobe #Flash #0days Additional Informations http://t.co/FDe22t5E #infosec