I received an unusual private message “Bad blog going around about you, heard or seen it yet?” from one of my followers. Unfortunately my follower fell into a traditional Twitter phishing and his account is surely now compromised.
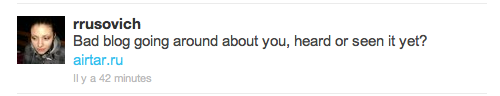 As you can see in the screenshot the link point to “http://airtar.ru“, a domain name registered since the 2011-10-13 by “[email protected]“. The web site is hosted on 111.123.180.39 in AS4134 ChinaNet GuiZhou Province and the hosting web server redirect you directly on “http://www.twittelr.com/r/“.
As you can see in the screenshot the link point to “http://airtar.ru“, a domain name registered since the 2011-10-13 by “[email protected]“. The web site is hosted on 111.123.180.39 in AS4134 ChinaNet GuiZhou Province and the hosting web server redirect you directly on “http://www.twittelr.com/r/“.
HTTP/1.1 301 Moved Permanently Server: nginx/1.0.6 Date: Sun, 16 Oct 2011 18:48:24 GMT Content-Type: text/html Content-Length: 184 Connection: keep-alive Location: http://www.twittelr.com/r/ P3P: CP="CAO COR CURa ADMa DEVa OUR IND ONL COM DEM PRE"
“twittelr.com” domain name is registered since the 2011-09-23 by “yu zhang [email protected]“. The web site is hosted on 220.164.140.252 in AS4134 China Telecom Yunnan Province. Some funny host name are hosted on the same name server than “twittelr.com“, like “xn--fiqs8s13n4ywnyd.net“.
Accessing “http://www.twittelr.com/r/” will redirect you to “http://www.twittelr.com/timed_out_session-/“.
<meta http-equiv="refresh" content="0; URL=/timed_out_session-/">
You will see this phishing page how is quiet good in term of design.
 If you provide your login and password the form will post all your informations on “http://www.twittelr.com/app/login2.php” and then redirect you to “http://www.twittelr.com/status/error/” page, but it is to late.
If you provide your login and password the form will post all your informations on “http://www.twittelr.com/app/login2.php” and then redirect you to “http://www.twittelr.com/status/error/” page, but it is to late.
If you access directly on the root directory of “twittelr.com” you will observe an chinese under-construction page 🙂
