MS13-051 Microsoft Office bulletin was release Tuesday 11th 2013 during the traditional Patch Tuesday. This bulletin fix one vulnerability, CVE-2013-1331, with a base CVSS score of 9.3 and targeting Microsoft Office 2003 and Office for Mac (2011). This vulnerability allow remote code execution and was reported by Andrew Lyons and Neel Mehta of Google Inc.
Microsoft has also release additional information’s and it appears that some “bad guys” were using this vulnerability as a zero-day in targeted attacks. The vulnerability is related on how Microsoft Office render malformed PNG files leading to a classic stack based buffer overflow.
Malicious Office documents were referencing a malicious PNG file loaded from Internet and hosted on a remote servers. Remote servers were using scripts in order to avoid multiple times exploitation from the same source. Microsoft believe that attacks were limited to Indonesia and Malaysia.
Microsoft provided some examples of URLs invoked by the malicious Office document, and some hashes of the malicious Office binary format documents.
- hXXp://intent.nofrillspace.com/users/web11_focus/4307/space.gif
- hXXp://intent.nofrillspace.com/users/web11_focus/3807/space.gif
- hXXp://mister.nofrillspace.com/users/web8_dice/3791/space.gif
- hXXp://mister.nofrillspace.com/users/web8_dice/4226/space.gif
- hXXp://www.bridginglinks.com/somebody/4698/space.gif
- hXXp://www.police28122011.0fees.net/pages/013/space.gif
- hXXp://zhongguoren.hostoi.com/news/space.gif
Information Gathering on “intent.nofrillspace.com“
By doing some researches we can find a Google cached Excel document mentioning this domain name the 2011-12-29. Domain name is mentioned as a gateway for malicious activities. Actually the web site is down, but associated IP was 80.93.50.73, hosted in the Russian Federation.
“No Frill Space” is a hosting company offering free web spaces. The company web site was still up, regarding WayBack Machine, the May 28th 2013. No additional information’s are available.

Information Gathering on “mister.nofrillspace.com“
By doing some researches we can find a Google cached web page as it appeared on 27 May 2013. Since, like the previous domain, the web site is no more available. No additional information’s are available.
Information Gathering on “www.bridginglinks.com“
Like “No Frill Space“, “BRIDGING LINKS” is a hosting company offering free web spaces. The company web site was still up, regarding WayBack Machine, the May 21th 2013. “www.bridginglinks.com” was hosted on 85.17.143.51 located in Netherlands.
If we take a look on urlQuery, we can see a submission dating of April 4th 2013, mentioning an interesting URL “hXXp://www.bridginglinks.com/somebody/4698/vw.php“. As you can see the path is the same as the path mentioned by Microsoft. “vw.php” could be one of the file used to avoid multiple times exploitation.
Joe Sandbox is also referencing Report 1482, no more available, that refer a URL “hXXp://www.bridginglinks.com/somebody/4688/vw.php?i=b95146-8a76c6cb7d84148d95ab5a4921b3839c” and a name of a Word document “virus_suspected.doc“. Associated MD5 of the document is “714876fdce62371da08c139377f23d76“, was submitted March 3th 2013, with a file size of 113.0 KB.

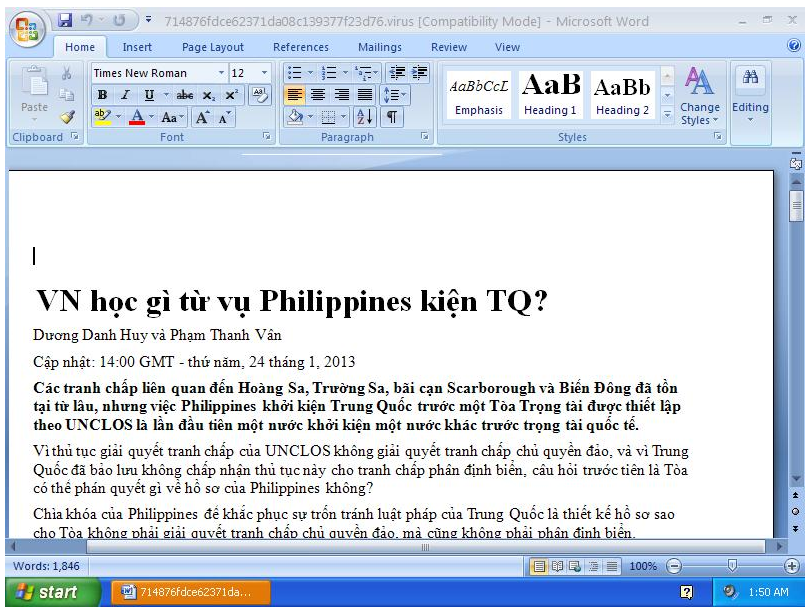
With the MD5 we can found a VirusTotal sample. Creation date of this document was February 25th 2013. Title of the document is “VN h?c gì t? v? Philippines ki?n TQ” that seem to be Vietnamese and could be translated to “VN learn from China’s conditions for Philippines“.
Document title seem to be related to the events of beginning of this year between China and Philippines regarding territory conflicts.
Here under a screenshot of the sample
@mwtracker also submitted a sample on Cryptam June 13th 2013.
Update of June 16th 2013
After doing some further investigations we noticed another Word sample (f85eaad502e51eafeae0430e56899d9b) submitted to VirusTotal October 28th 2009 and that has a creation date of October 26th 2009. A re-submission of this sample clearly detect CVE-2013-1331 !
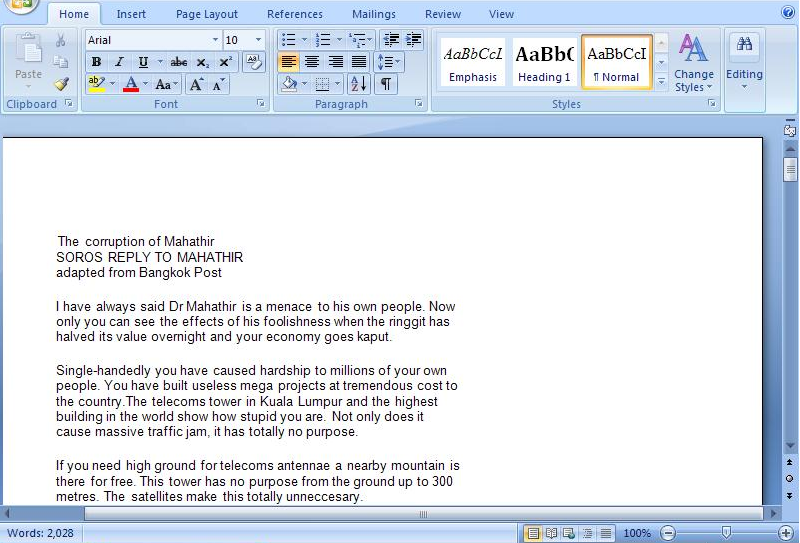
By analyzing this sample title of the document is “The corruption of Mahathir” from autor “585“. “The corruption of Mahathir” document is a reference to Mahathir Mohamad a Malaysian politician who was the fourth Prime Minister of Malaysia, and the document is an adaptation of a Bangkok Post article to remind people how the country has been damaged by Dr M, UMNO and his cronies.
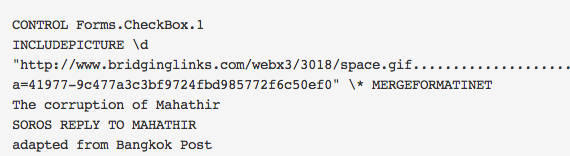
Like the previous sample, this sample is referencing “www.bridginglinks.com” and has exactly the same patterns.
Update of June 17th 2013
Microsoft has reference some hashes of the malicious Office documents. Here under more detailled information’s on these documents. All these malicious documents are actually only detected by Avast and Symantec.
35a6bbc6dda6a1b3a1679f166be11154 Office document
Document theme is related to telecommunications and has “Telco – XX??2013??????????” as title, that could be translated to “Telco – XX company in 2013 described the core network building program“. The document was created Wednesday March 6th 2013 and last saved by “abc“. The document initiate connexions to “hXXp://zhongguoren.hostoi.com/news/space.gif“.
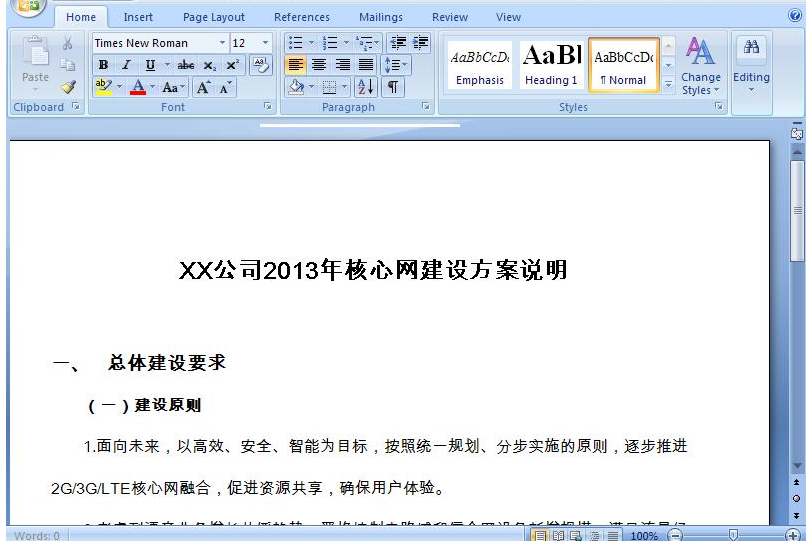
fde37e60cc4be73dada0fb1ad3d5f273 Office document
Document theme is related to Susilo Bambang Yudhoyono an Indonesian politician and retired Army general officer who has been President of Indonesia since 2004. Document title is “Macam-macam critis terhadap SBY dan gerakan kabinet di situs Gerakan Anti SBY II” that could be translated to “Various critis against SBY cabinet and movement at the site of the anti SBY II“. The document was created Monday October 31th 2011 and last saved by “xmuser“. The document initiate connexions to “hXXp://mister.nofrillspace.com/users/web8_dice/4226/space.gif“.
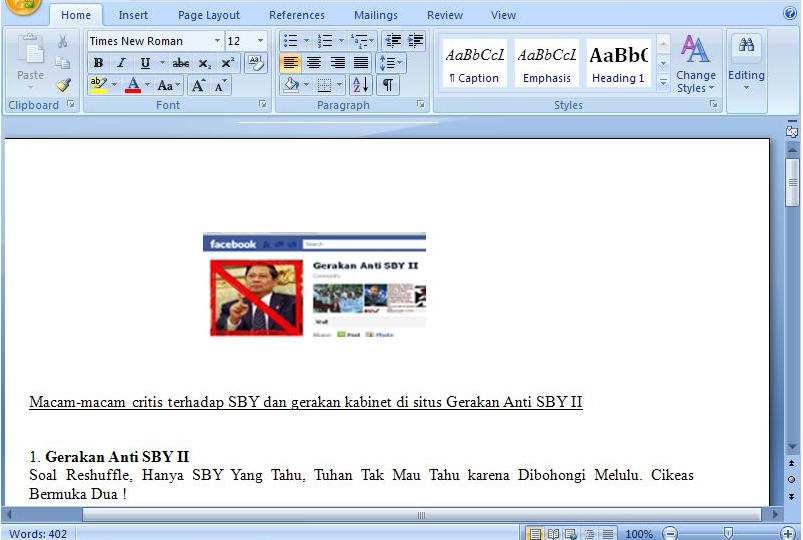
2f1ab543b38a7ad61d5dbd72eb0524c4 Office document
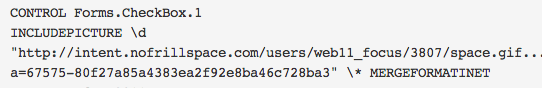
Document theme is related to Chinese zodiac previsions for 2011, and document title is “Forecast for 2011“. The document was created Monday February 7th 2011 and last saved by “xmuser“. The document initiate connexions to “hXXp://intent.nofrillspace.com/users/web11_focus/3807/space.gif“.

28e81ca00146165385c8916bf0a61046 Office document
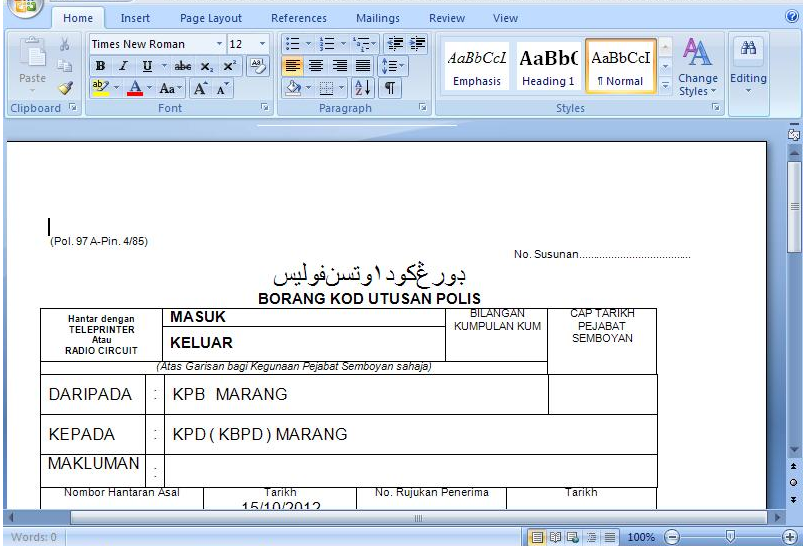
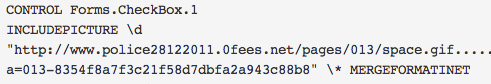
Document theme is Malaysian Telco. The document was created by “PDRM” and last saved by “abc“, also creation date of the document is Sunday October 14th 2012. The document initiate connexions to “hXXp://www.police28122011.0fees.net/pages/013/space.gif“.
7eb17991ed13960d57ed75c01f6f7fd5 Office document
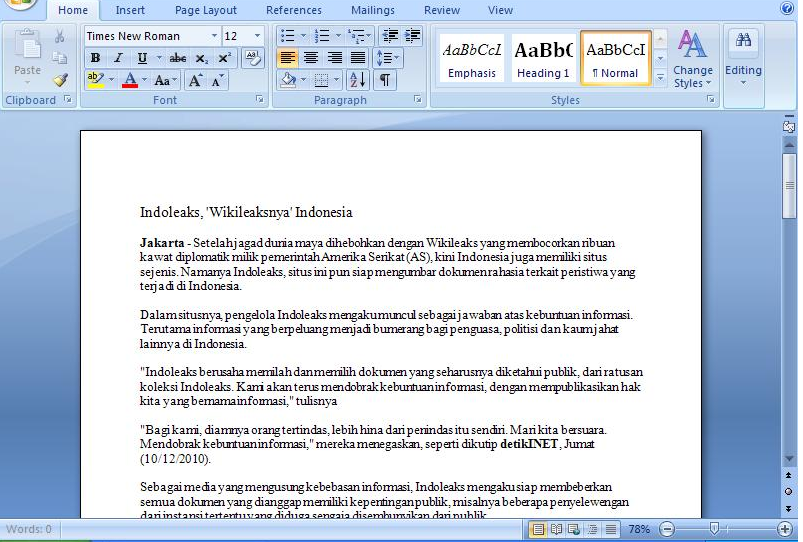
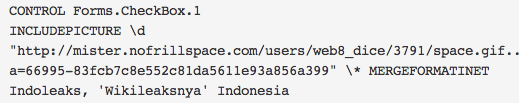
Document theme is Indoleaks, an Indonesian equivalent of Wikileak, and document title is “Indoleaks, ‘Wikileaksnya’ Indonesia“. The document was created by “3565“, last saved by “xmuser” and created Sunday January 23th 2011. The document initiate connexions to “hXXp://mister.nofrillspace.com/users/web8_dice/3791/space.gif“.
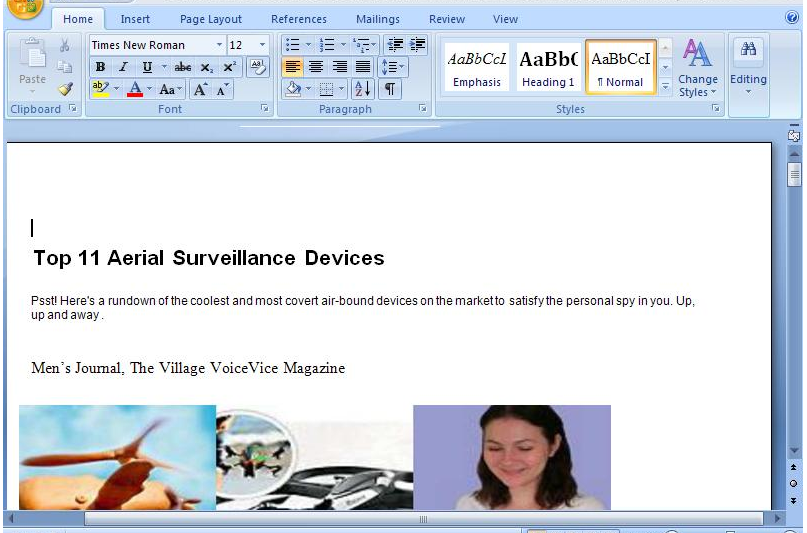
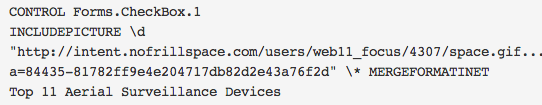
70511e6e75aa38a4d92cd134caba16ef Office document
Document theme is surveillance devices with document title “Top 11 Aerial Surveillance Devices“. The document was last saved by “xmuser” and created Tuesday January 3th 2012. The document initiate connexions to “hXXp://intent.nofrillspace.com/users/web11_focus/4307/space.gif”
Conclusions
Here under a recap table of all behaviors
| MD5 | Author | Last Saved By | Creation Date | Last Saved Date | Domain | Params |
| 714876fdce62371da08c139377f23d76 | SYSTEM | SYSTEM | 2013-02-24 | 2013-02-24 | www.bridginglinks.com | 95146-555210c567278074917c1d11f25a6221 |
| f85eaad502e51eafeae0430e56899d9b | 585 | - | 2009-11-26 | 2009-11-26 | www.bridginglinks.com | 41977-9c477a3c3bf9724fbd985772f6c50ef0 |
| 35a6bbc6dda6a1b3a1679f166be11154 | User | abc | 2013-03-06 | 2013-03-06 | zhongguoren.hostoi.com | 2064-ccca749e1a0e6806503c83048bb643d3 |
| fde37e60cc4be73dada0fb1ad3d5f273 | - | xmuser | 2011-10-31 | 2011-10-31 | mister.nofrillspace.com | 81425-3b068ea3d53786a94aaa715c7692a0a1 |
| 2f1ab543b38a7ad61d5dbd72eb0524c4 | - | xmuser | 2011-02-07 | 2011-02-07 | intent.nofrillspace.com | 67575-80f27a85a4383ea2f92e8ba46c728ba3 |
| 28e81ca00146165385c8916bf0a61046 | PDRM | abc | 2012-10-14 | 2012-10-14 | www.police28122011.0fees.net | 013-8354f8a7f3c21f58d7dbfa2a943c88b8 |
| 7eb17991ed13960d57ed75c01f6f7fd5 | 3565 | xmuser | 2011-01-23 | 2011-01-23 | mister.nofrillspace.com | 66995-83fcb7c8e552c81da5611e93a856a399 |
| 70511e6e75aa38a4d92cd134caba16ef | - | xmuser | 2012-01-03 | 2012-01-03 | intent.nofrillspace.com | 84435-81782ff9e4e204717db82d2e43a76f2d |
My personal opinion is that:
- I can clearly confirm that the zero-day was exploited in the wild since minimum
February 2013 October 2009
- the campaign was active since a while and has surely target other victims than previously thought.
I will keep you in touch with additional information’s.















