Conclusion: It seem that AV vendors did a big mistake and blocked thousands of legit emails and by consequence also disclosed the content of certain of these emails on Internet, like DRP plan of banks…
All detected samples have now reduced they’re detection rate to only marginal anti-viruses. But clearly F-Secure and BitDefender were detecting and blocking thousands of emails during the last days. For the moment, we have no explanation from the anti-virus vendors.
I would like to thanks @_clem1, @Kafeine and @PhysicalDrive0 for they’re support in these clarifications.
On December 8th 2015, Microsoft released, during his regular Patch Tuesday, two updated security advisory, one new security advisory and twelve security bulletins. On the twelve security bulletins, MS15-131 concerned Microsoft Office and fixed 6 privately reported vulnerabilities.
One of the 6 vulnerabilities fixed in MS15-131, CVE-2015-6172 vulnerability raised particular attention of the security community. This vulnerability, named Outlook “letterbomb” or “BadWinMail“, would allow an attacker to sneak past Outlook’s security features. The vulnerability affects Office 2010 and later, as well as Microsoft Word 2007 with Service Pack 3.
This vulnerability has been discovered and privately reported to Microsoft by Haifei Li of Intel Security IPS Research Team. The security researcher published a paper describing the vulnerability accompanied by a demonstration video.
Unfortunately it seem that this vulnerability is actually exploited and was exploited before the release of Microsoft security patch.
Two files “FW Joseph J. Durczynski.rtf” (957a8d9d6bf7a0e54ad7eb350c930232) and “FW Philip Services Corp. et al..rtf” (20e184a415cd71eee1cea83df262f814) were submitted to VirusTotal the 27 December and detected as exploit of CVE-2015-6172.
“FW Philip Services Corp. et al..rtf” file seems to be related to PSC Industrial Services. PSC claim to be the leading provider of specialty maintenance services and technology solutions to the critical energy infrastructure in the United States.
“FW Joseph J. Durczynski.rtf” file seems to be related to Systech Environmental Corp and to particularly a certain Joe Durczynski working for Systech Environmental Corp.
By doing additional researches I found a third sample “_WRF_0CE7DC0E-AB99-4196-8DC2-F818ABF7C29A_.tmp” (52c4096e99126851736715c34b1f50a5) submitted on malwr the 23 December. This sample was also submitted on VirusTotal the 23 December and also recognised as exploit of CVE-2015-6172.
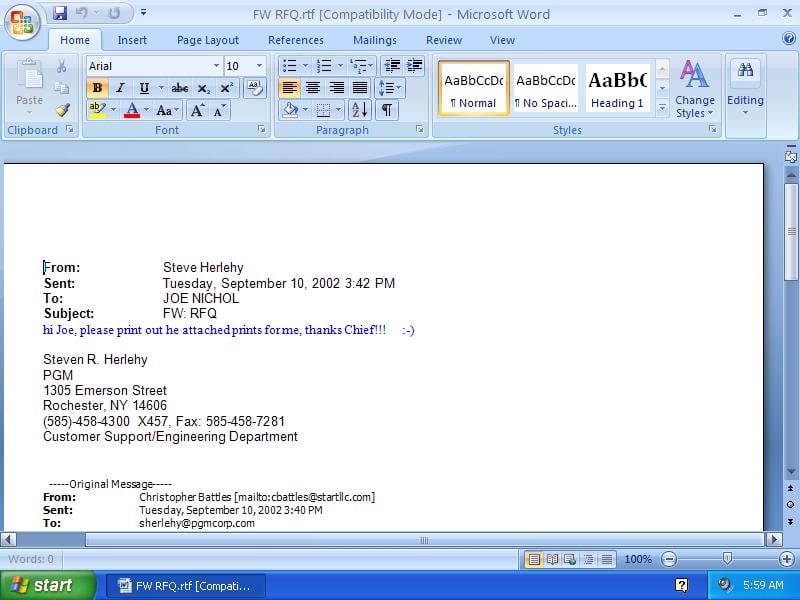
One additional file “FW RFQ.rtf” (fab9cfbc629fb3c3eb541fdaf8169ee1), reported to me by @PhysicalDrive0, targeting PGM Corp. PGM is a full service precision manufacturing corporation specialising in precision CNC machining, turning, grinding and assembly.
Interesting informations are the strings in the static analysis of the 23th December malwr sample.
Subject of the email was “FW: Disaster Recovery – home binder” and this email is an internal mail exchange of Safe Credit Union organisation. Also the mail containing the malware was sent the Tuesday, 8th September 2015.
It seem to be quiet urgent to patch if you didn’t already did it, but that seem to be more and more sure is that CVE-2015-6172 was used in the wild before the release of the Microsoft December patch.
Additional samples are actually submitted:
- “KOMPETANCEUDVIKLING mail til området.rtf” (151ef7c2c675b925e67e34a10fcd6f4a)
- “060320 Varsel om krav fra K401 SF-HJ.rtf” (5f350c6f062c7c2117d3da6b108566e7)