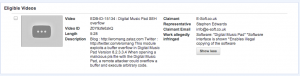
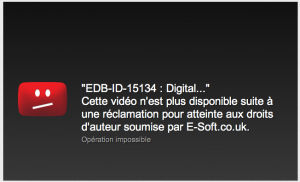
Yesterday I received an email from YouTube notifying me that the Metasploit video demonstration of Digital Music Pad SEH overflow (EDB-ID-15134) has been removed for copyright infringement.
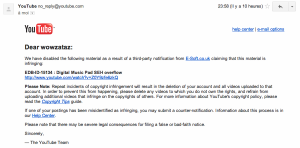
YouTube has disable the video as a result of a third-party notification from E-Soft.co.uk, the vendor of Digital Music Pad.
The video, I recorded in February 2011, was a demonstration of “exploit/windows/fileformat/digital_music_pad_pls” Metasploit exploitation module. This module was developed by Abhishek Lyall in October 2010.
When I recorded the vulnerability exploitation demonstration the affected software was freely downloadable from the vendor web site and no sound or other materials submitted to copyrights were supporting the video.
My videos, available on my YouTube channel, are made for educational purposes, helping security researchers to understand on how to use Metasploit modules or other exploits and warning consumers on products vulnerabilities. If you search “Digital Music Pad” on Google, you can find an uncensored copy of my video demonstration and this video is also available on SecurityTube.
Many legal cases exists regarding vulnerabilities disclosures, all of them are reported on Attrition.org legal threats against security researchers.
I really don’t understand why the Metasploit Digital Music Pad SEH overflow demo was removed and for what reason, and why E-Soft.co.uk asked YouTube to remove my video. So I will contact Attrition and submit them this case cause it is really seemed to be an abuse of copyright usage.
Also this case could be a dangerous precedent for other security researchers how are publishing demonstration videos on YouTube.
Actually I’m no more able to submit new videos on YouTube or modify any parameters of my channel, cause I’m considered as a criminal and I’m forced to watch a stupid “YouTube Copyright School” and forced to fill full a form with stupid questions regarding copyrights.
Update 1 : 18/05 at 12:47. First contact with Attrition.org in order to submit them a new case of legal threat.
Update 2 : 18/05 at 14:38. I have finally recover my YouTube account after responding to the YouTube Copyright School questions. Funny stuff the form submission wasn’t compatible with Google Chrome, so I had to switch to Safari in order to submit my answers and recover my YouTube account #fail
Update 3 : 18/05 at 15:23. Seem that I can no more select Creative Commons license for my new videos on YouTube, forced to use YouTube standard license. #fail
Update 4 : 27/05 at 11:07. After some days in Hamburg Germany, I send an email to E-Soft.co.uk in order to know the reason of the “copyright infringement”.
Update 5 : 28/05 at 11:01. After some discussions with Attrition. We have discover the reason submitted from E-Soft.co.uk to YouTube. “Software: “Digital Music Pad” *Software interface is shown *Enables illegal copying of the software“.