Afterglow is a collection of scripts which facilitate the process of generating “linked graphs” or “network graphs”. The software is written in Perl, must be used on the command line, but quiet easy to use.
AfterGlow expects a CSV file as input and generates either an attributed graph langugage file that can be processed by the Graphviz libraries.
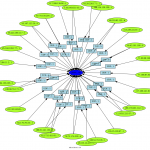
We will exercise us to use Afterglow with my previous post “Strange activities on 28081 and 47919 TCP/UDP destination ports” case.
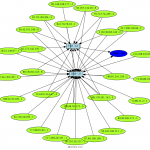
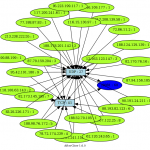
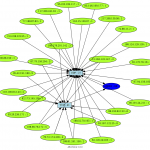
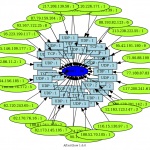
To run afterglow, we need a CSV file, our first example has 3 rows : sources IP, protocol and destination port (how is 28081). The source IP will be the source data, the protocol the event, and the destination port the target.
We need also a configuration file named “color.properties” to configure the color output. Our will be very simple.
color.source=”greenyellow”
color.event=”lightblue”
color.target=”red”
To create your first afterglow visualization just lunch the following command.
cat 28081.csv | afterglow.pl -c color.properties -a -d -p 2 -e 3 | neato -Tpng -o 28081.png
Here under a gallery containing some afterglow results.