By analyzing one of the Dark South Korea dropper, I discovered interesting behaviours associated with the PuTTY binaries installed in “%TMP%” Windows folder. These behaviours could be considered as expected, but they could be used more efficiently in the future.
The two installed binaries are “alg.exe“ and “conime.exe“ used to upload “~pr1.tmp” bash file to *NIX targets discovered in configuration files of mRemote and SecureCRT.
“alg.exe“ is “plink.exe“ a PuTTY tool acting as a command-line interface to the PuTTY back ends, and “conime.exe” is “pscp.exe” PuTTY tool acting as a SCP client, i.e. command-line secure file copy. These two binaries are legit and don’t contain any associated malwares, they are only used by a malware as support tools.
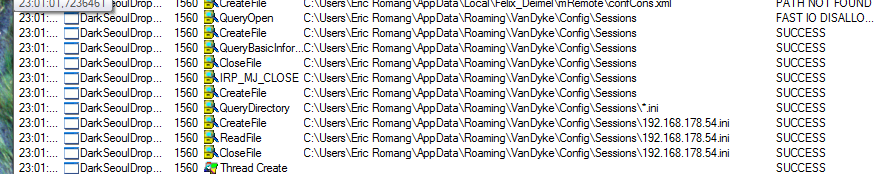
If mRemote is installed, the dropper extract all required information’s (credentials, ports, ip/domain) from “confCons.xml” configuration file, and use an encryption method vulnerability in mRemote to decrypt it the stored password. After exploitation of the vulnerability, “conime.exe” is used to drop the bash file on the targeted servers.
If the latest version of SecureCRT is installed, the dropper extract all required information’s (credentials, ports, ip/domain) present in “*.ini” configuration files. Each saved connection in SecureCRT use it ones “*.ini”. It seem that an unknown vulnerability was present in previous versions of SecureCRT in order to decrypt the stored password. But in the latest version of SecureCRT, this vulnerability don’t seem to be present. So when “conime.exe” try to connect to the targeted servers the authentication fails due to a bad password.
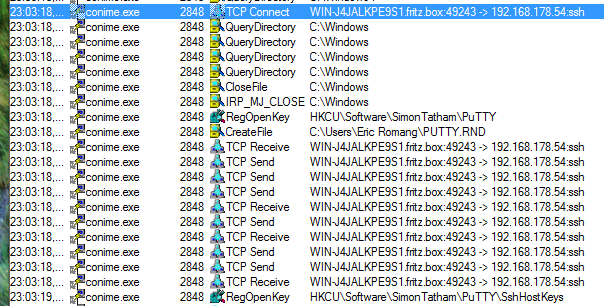
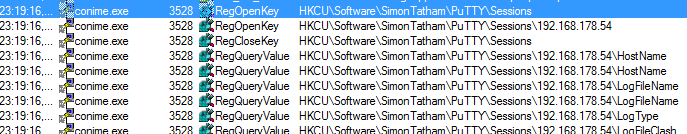
During my research on the potential SecureCRT vulnerability, I was intrigued by “conime.exe” by access tentatives to the registry keys of PuTTY software “HKCU\Software\SimonTatham\PuTTY\Sessions” and “HKCU\Software\SimonTatham\PuTTY\SshHostKeys“.
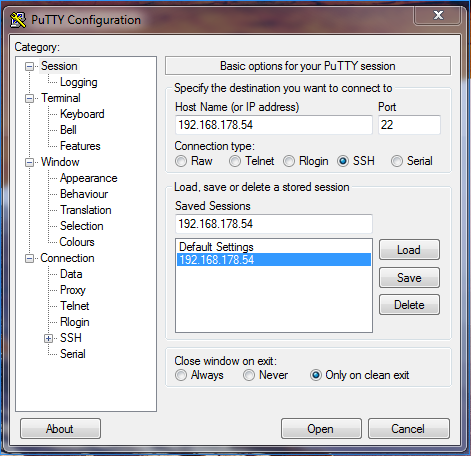
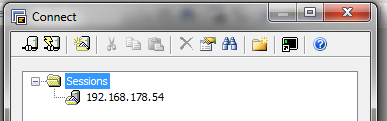
I decided to install PuTTY, like a majority of sysadmin’s, and create an entry corresponding to potential server also recorded in SecureCRT software.
Then I execute the dropper one more time and discovered that “conime.exe“, as expected, has access the PuTTY registry keys related to the targeted server “HKCU\Software\SimonTatham\PuTTY\Sessions\192.168.178.54“. The dropper authentication tentative was still unsuccessful, du to the wrong password.
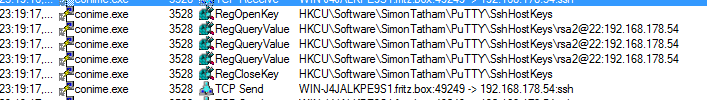
But I also observed that “conime.exe” was also trying to access another registry key of PuTTY “HKCU\Software\SimonTatham\PuTTY\SshHostKeys\rsa2@22:192.168.178.54“.
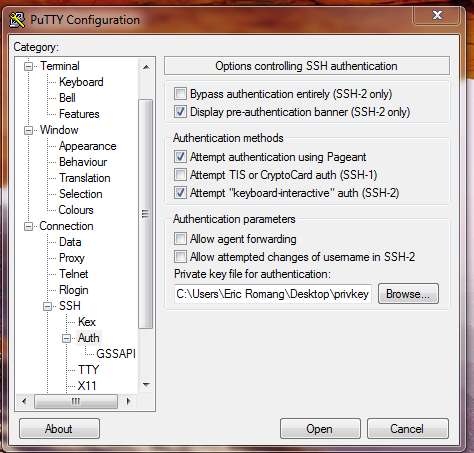
I decided then to create a private and public SSH key, and to configure my putty session to support this SSH private key authentication. The private key wasn’t protected by a passphrase.
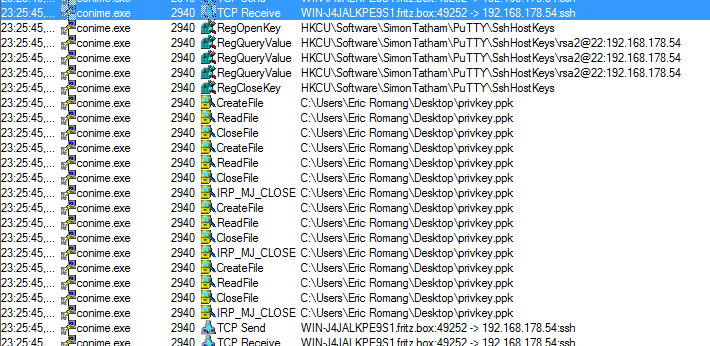
I execute the dropper one more time and observed a successfull authentication on the targeted server. “conime.exe” was using the private key path present in PuTTY registry key.
My final test was to remove the private key from the PuTTY configuration and use “pageant.exe“, an SSH authentication agent for PuTTY, PSCP, PSFTP, and Plink. I loaded my private key in “pageant.exe” and executed the dropper one more time. Same result as the previous one, a successfull authentication on the targeted server.
Conclusions
- By analyzing one of the Dark South Korea dropper, with associated vulnerabilities in mRemote and SecureCRT, we can observ that the “bad guys” have use old vulnerabilities in old softwares in order to infect *NIX servers. Why use these old vulnerabilities, if you can simply target PuTTY when it is used with private keys.
- Never generate a private key without a passphrase
- Don’t let PuTTY Pageant run with charged private keys.
Dark South Korea and Discovered PuTTY Tools Behaviours – http://t.co/Ejx20VOx0B
RT @eromang: Dark South Korea and Discovered PuTTY Tools Behaviours http://t.co/TPiODTQlC7
RT @virusbtn: In the cyber-attacks on South Korea, a harmless PuTTY install was used. @eromang explains how http://t.co/z0duL50rdy
RT @virusbtn: In the cyber-attacks on South Korea, a harmless PuTTY install was used. @eromang explains how http://t.co/z0duL50rdy
RT @virusbtn: In the cyber-attacks on South Korea, a harmless PuTTY install was used. @eromang explains how http://t.co/z0duL50rdy
RT @virusbtn: In the cyber-attacks on South Korea, a harmless PuTTY install was used. @eromang explains how http://t.co/z0duL50rdy
RT @virusbtn: In the cyber-attacks on South Korea, a harmless PuTTY install was used. @eromang explains how http://t.co/z0duL50rdy
RT @unpacker: [EricRomang] Dark South Korea and Discovered PuTTY Tools Behaviours http://t.co/3QjGB9gXXd
RT @virusbtn: In the cyber-attacks on South Korea, a harmless PuTTY install was used. @eromang explains how http://t.co/z0duL50rdy
In the cyber-attacks on South Korea, a harmless PuTTY install was used. @eromang explains how http://t.co/z0duL50rdy
RT @suffert: This => “Never generate a private key without a passphrase” http://t.co/tkayP3IBsa Dark South Korea and Discovered PuTT …
RT @matteoca: Dark South Korea and Discovered PuTTY Tools Behaviours http://t.co/rmZwQIXZzv
Dark South Korea and Discovered PuTTY Tools Behaviours http://t.co/rmZwQIXZzv
RT @suffert: This => “Never generate a private key without a passphrase” http://t.co/tkayP3IBsa Dark South Korea and Discovered PuTT …
RT @secnight: PuTTY binaries installed in “%TMP%” Windows folder..Dark South Korea and..http://t.co/a04RAWQBNH …@eromang amazing and cool 😉
Dark South Korea and Discovered PuTTY Tools Behaviours http://t.co/xnuMOXsQhE
This => “Never generate a private key without a passphrase” http://t.co/tkayP3IBsa Dark South Korea and Discovered PuTTY Tools Behaviours
PuTTY binaries installed in “%TMP%” Windows folder..Dark South Korea and..http://t.co/a04RAWQBNH …@eromang amazing and cool 😉
RT @Dinosn: Dark South Korea and Discovered PuTTY Tools Behaviours http://t.co/Fie7UctkfM
Dark South Korea and Discovered PuTTY Tools Behaviours http://t.co/Fie7UctkfM
Dark South Korea and Discovered PuTTY Tools Behaviours http://t.co/uUVoCn4fjl
RT @ubersec: Dark South Korea and Discovered PuTTY Tools Behaviours: http://t.co/D7ersS8Vff #infosec
RT @ubersec: Dark South Korea and Discovered PuTTY Tools Behaviours: http://t.co/D7ersS8Vff #infosec
Dark South Korea and Discovered PuTTY Tools Behaviours: http://t.co/D7ersS8Vff #infosec
RT @unpacker: [EricRomang] Dark South Korea and Discovered PuTTY Tools Behaviours http://t.co/3QjGB9gXXd
RT @MasafumiNegishi: “Dark South Korea and Discovered PuTTY Tools Behaviours” http://t.co/QOhj9tYwky
[EricRomang] Dark South Korea and Discovered PuTTY Tools Behaviours http://t.co/3QjGB9gXXd
RT @eromang: Dark South Korea and Discovered PuTTY Tools Behaviours http://t.co/TPiODTQlC7
RT @MasafumiNegishi: “Dark South Korea and Discovered PuTTY Tools Behaviours” http://t.co/QOhj9tYwky
“Dark South Korea and Discovered PuTTY Tools Behaviours” http://t.co/QOhj9tYwky
RT @eromang: Dark South Korea and Discovered PuTTY Tools Behaviours http://t.co/TPiODTQlC7
[Suggested Reading] – Dark South Korea and Discovered PuTTY Tools Behaviours http://t.co/3stVnnpMjC