Metasploit team has release a John the Ripper password cracker integration into Metasploit. Now it is directly possible to crack weak passwords gathered in hashes files, or LANMAN/NTLM, hashdump in msfconsole.
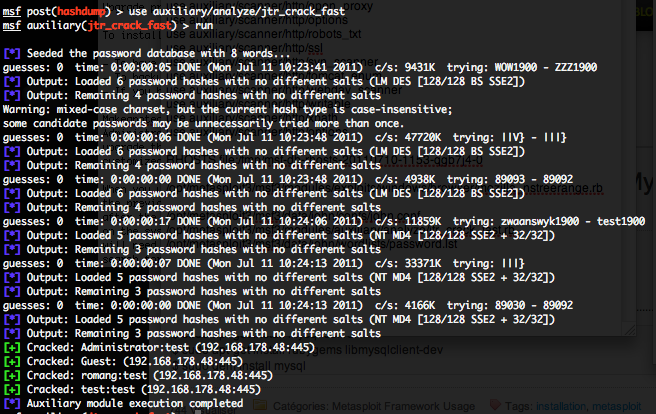
JtR is integrated as an “analyze” auxiliary module, called “jtr_crack_fast ” and can be used by typing this command :
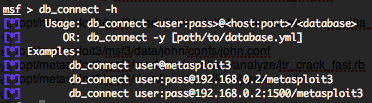
In order to use you this auxiliary module you first need to have Metasploit database support (postgres or mysql) and to be connected to this database. To create and/or connect you to a database, you only need to type theses commands :
If you don’t have an existing database, “db_connect” will create the database for you. Also you can use “db_status” command to verify your connexion.
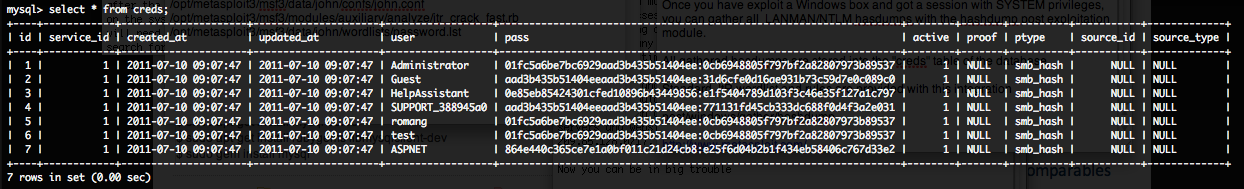
Once you have exploit a Windows box and got a session with SYSTEM privileges, you can gather all LANMAN/NTLM hasdumps with the “hashdump” post exploitation module.
All gathered hasdumps are stored into the “creds” table of the database.
Now, that you have hashdumps in the database you try to crack weak passwords with the integrated Metasploit John the Ripper.
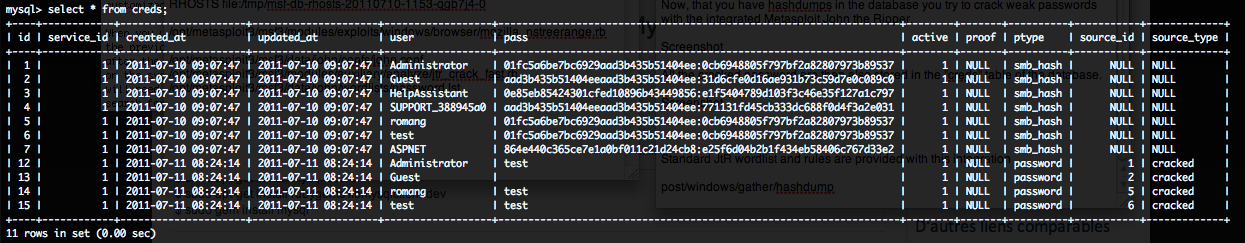
If password are cracked successfully, these cracked passwords are then also stored in the “creds” table of the database.
Metasploit build in JtR include standard wordlist and rules, but you can also provide to the module the directory path how is containing JtR (JOHN_BASE), and also the absolute path to the JtR executable (JOHN_PATH).
“john.conf” file is located by default in “/opt/metasploit3/msf3/data/john/confs/john.conf” and the wordlist into “/opt/metasploit3/msf3/data/john/wordlists/password.lst“.