The Metasploit Team has release a new plugin, a bridge between Metasploit and Nessus. This new plugin is a collaboration between HD Moore, James Lee, Zate Berg, darkoperator and the Nessus Team. If you follow the PaulDotCompodcast, you know that Paul is a employe of the Nessus team and that darkoperator (aka Carlos Perez) is an official developer of the Metasploit project. A good collaboration between the 2 teams how has uncorked on this new important step in Metasploit.
In the first par of the post serie, we have describe all the generic, user and policy command. In the second post we have describe the plugin and scan commands. In this post we will describe the report and “nessus_find_targets” command.
Reports Commands
- Getting a list of all available reports – nessus_report_list :
To get a list off all available Nessus reports, type the following command :

- Getting all detected hosts from a Nessus report – nessus_report_hosts :
To get all hosts detected by Nessus and present in a report, just run the following command :
nessus_report_hosts <report id>
Where “report id” is the unique ID of the report available with the “nessus_report_list” command.
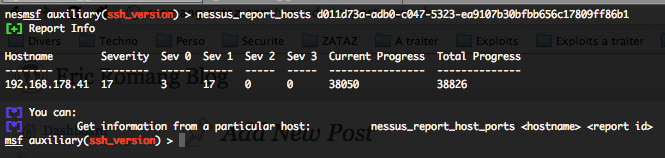
You will get all the detected hostnames, in the Nessus report, with the number of potential vulnerabilities detected, classified by severities.
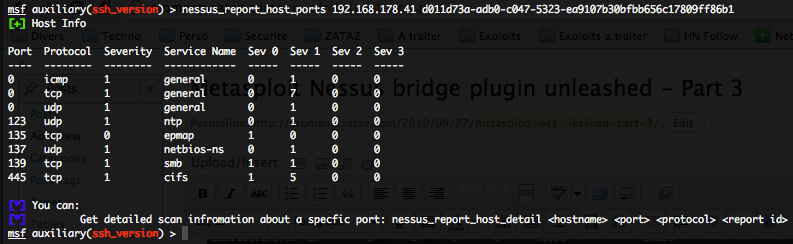
- Getting details on ports vulnerabilities by host – nessus_report_host_ports :
To get ports vulnerabilities details, classified by severities, on a particular host, just run the following command :
nessus_report_host_ports <hostname> <report id>
Where “hostname” is the unique hostname available previous “nessus_report_hosts” command, and “report_id” the unique ID of the report.
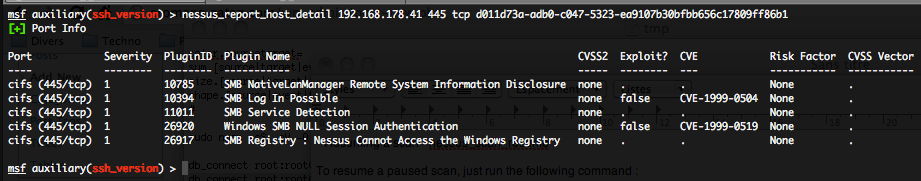
- Getting details on a particular port for a host present in a Nessus report – nessus_report_host_detail :
To get details on a particular port for a host present in a Nessus report, just run the following command :
nessus_report_host_detail <hostname> <port> <protocol> <report id>
Where “hostname” is the unique hostname available in the “nessus_report_hosts” command, “port” and “protocol” the unique port and protocol available with the previous “nessus_report_host_ports” command, and “report id” the unique ID of the report.
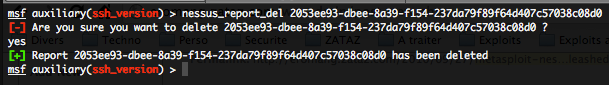
- Deleting a report – nessus_report_del :
To delete a report just type the following command :
nessus_report_del <reportname>
Where “reportname” is the unique ID for the report available with the “nessus_report_list” command.
- Importing a Nessus report into Metasploit – nessus_report_get :
To import a Nessus report, you will thirst need to create a ODBC connexion between Metasploit and your favorite database (for us MySQL).
The connexion, and the database creation is done by the following command, please don’t use these login and passwords 🙂
db_connect root:root@localhost/locallan
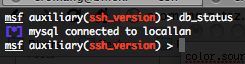
To verify that your ODBC connexion is active, use the following command :
Then execute the following command to import the Nessus report into Metasploit.
nessus_report_get <report id>
Where “report id” is the unique ID for the report available with the “nessus_report_list” command.

To check if every thing is imported, run the following commands :
db_hosts, will return you all imported hosts from the Nessus report
db_services, will return you all imported port, by protocols, by hosts from the Nessus report.
db_vulns, will return you all detected vulnerabilities by ports/protocols by hosts from the Nessus report.
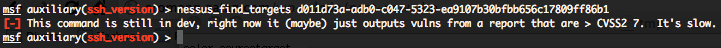
- Finding targets in a scan with CVSS2 > 7 and return scans info – nessus_find_targets :
To get a list of potential targets from the Nessus report, just run the following command.
nessus_find targets <report id>
Where “report id” is the unique ID for the report available with the “nessus_report_list” command.