Every know the Cloud security problematic, and the associated issues how are more and more visible. In July 2008 Outblaze and Spamhaus blocked Amazon EC2 Public IP ranges due to distribution of spam and malware. In April 2009 Arbor Networks reported that a malicious Google AppEngine was used as botnet CnC. In April 2010, VoIP Tech Chat has reported some Amazon EC2 SIP brute force attacks, until abuse report to Amazon EC2 the attacks have still continue in May, etc.
In March 2009, our Honey Net reported us a malicious Remote File Inclusion code hosted on a Google Sites, how was invoked in few events. The Google Sites was called “nurhayati satu“, an Indonesian surname and first name. The invoked malicious script was “http://sites.google.com/site/nurhayatisatu/1.txt???“.
[TABLE=10]
Between March 2009 and May 2010, no more sign of life of this Google Sites. But since May the number of events have increase and we could distinguish the apparition of the “Cloud” phenomena. “nurhayati satu” Google Sites has now around 16 IP addresses associated as hosting server and all these IP addresses are owned by Google Inc. The involved CIDR’s are 209.85.128.0/17 and 74.125.0.0/16.
It is interesting to visualize the interactions of the attackers source IPs (in blue) with the Google Sites Cloud destination IPs (in green).
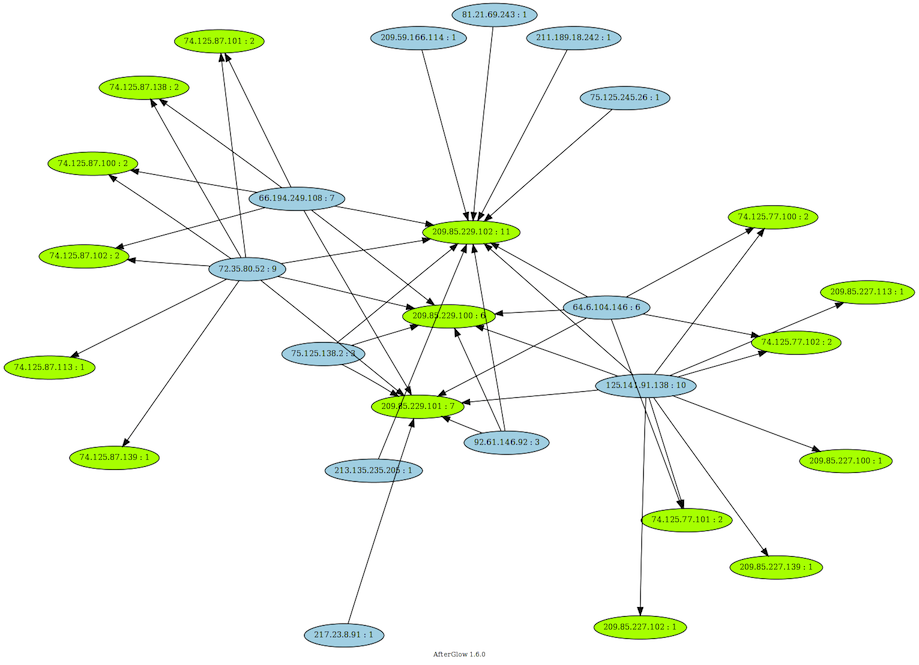
You can see that the attackers source IPs are not dedicated to one hosting server IP, but are also invoking the “Cloud” IPs.
Between the search engine of the “nurhayati satu” Google Sites you can find other hosted classical scripts, scanners, tcl, etc.
Every one of you know the Google results labelled ‘This site may harm your computer‘.
It will be funny if Google Sites themselves will be labelled, but more seriously should we declare Google Sites to Dshield, Abuse.ch or Emerging Threats ? Should we block Google, cause Google is delivering some malwares between his Cloud infrastructure, and no one care 🙂