You may have read my first blog post regarding the evolutions of Gong Da exploit kit, who has involve in a more complex EK by supporting most of the latest Oracle Java vulnerabilities like CVE-2011-3544 (Oracle Java Rhino exploit), CVE-2012-4681 (Oracle Java August 0day), CVE-2012-0507 (another Oracle Java exploit), CVE-2012-1723 (another Oracle Java exploit) and CVE-2012-1889 (Microsoft XML Core Services). Some previous versions of Gong Da EK had also support for CVE-2011-2140 (Adobe Flash Player) and CVE-2012-0003 (Windows Media), but it seem that the new version don’t use them anymore.
After Cool EK and BlackHole EK, Gong Da EK has integrate the exploitation of the Java vulnerability aka CVE-2012-5076 (Java Applet JAX-WS). This vulnerability, patched in version 7U9 of Oracle Java is affecting all version of Oracle Java from 7 to 7U7.
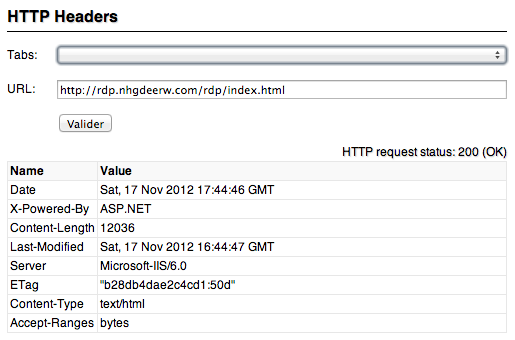
This new version was discovered on “hxxp://rdp.nhgdeerw.com/rdp/index.html” a web site how is actually still online.
“rdp.nhgdeerw.com” is hosted on 173.208.189.170, AS32097, in US and “wangmazz.com” domain name was created the 2012-11-17, through name.com registrar, for “tao we ([email protected])“.
The “index.html” file containing JavaScript code obfuscated by “JSXX VIP JS Obfuscator“ is recognized only by 8 on 44 anti-viruses on VirusTotal.com.
/*Encrypt By ndtw.wmdottw.com’s JSXX 0.44 VIP*/
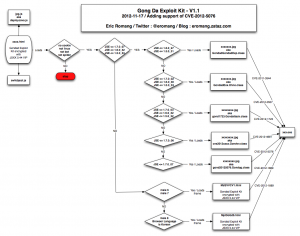
After de-obfuscation of the “index.html” file you can see that Gong Da Pack has involve to the following diagram.
Here under some information s regarding the different files:
- MWCxT0.jpg (aka CVE-2012-5076) : 2/44 on VirusTotal.com
- aWxsX0.jpg (aka CVE-2011-3544) : 7/44 on VirusTotal.com
- kCyrwe1.jpg (aka CVE-2012-0507) : 10/44 on VirusTotal.com
- RQnRD3.jpg (aka CVE-2012-1723) : 21/44 on VirusTotal.com
- pujF8.jpg (aka CVE-2012-4681) : 28/44 on VirusTotal.com
how do you deobfuscate this? cannot find the deobfuscator online anywhere
RT @eromang: Gong Da / Gondad Exploit Pack Add #Oracle #Java CVE-2012-5076 support http://t.co/DaLyMvjL #infosec