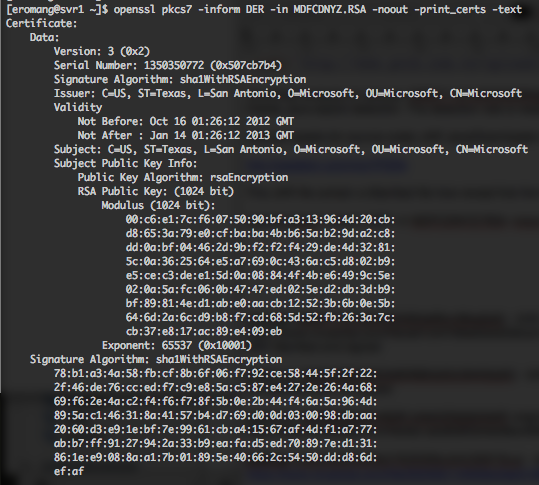
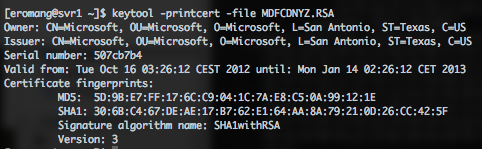
Oracle has provide his Critical Patch Update (CPU) for October 2012 how has been released on Tuesday, October 16. This CPU contains 109 security vulnerability fixes across 11 of Oracle products. On the 109 security vulnerabilities 32 of them may be remotely exploitable without authentication, this represent 29% of the vulnerabilities. The highest CVSS Base Score for vulnerabilities in this CPU is 10.0 and concern Oracle Database Server and Oracle Fusion Middleware. 6 vulnerabilities have a CVSS base score upper or equal to 7.0.
As you may know Oracle is using CVSS 2.0 (Common Vulnerability Scoring System) in order to score the reported vulnerabilities. But as you also may know security researchers disagree with the usage of CVSS by Oracle. Oracle play with CVSS score by creating a “Partial+” impact rating how don’t exist in CVSS 2.0, and by interpreting the “Complete” rating in a different way than defined in CVSS 2.0.
Oracle Database Server
5 vulnerabilities are reported for “Oracle Database Server” and 1 of them may be remotely exploitable without authentication. The highest CVSS score of these vulnerabilities is 10.0. Affected component is “Core RDBMS“.
CVE-2012-3132, with a CVSS base score of 6.5 is related to the security alert emitted during August 2012. CVE-2012-3137 has a Oracle CVSS base score of 10.0 but an NIST CVSS base score of 6.4. CVE-2012-1751 has a CVSS base score of 6.5, CVE-2012-3151 a CVSS base score of 3.3 and CVE-2012-3146 a CVSS base score of 2.1.
Oracle Fusion Middleware
26 vulnerabilities are reported for “Oracle Fusion Middleware” and 13 of them may be remotely exploitable without authentication. The highest CVSS score of this vulnerability is 10.0. Affected component is “Oracle JRockit“, “Oracle Reports Developer“, “Oracle Event Processing“, “Oracle WebLogic Server“, “Oracle Imaging and Process Management“, “Oracle WebCenter Sites“, “Oracle Application Server Single Sign-On“, “Oracle BI Publisher“, “Oracle Business Intelligence Enterprise Edition” and “Oracle Outside In Technology“.
CVE-2012-3202 has a CVSS base score of 10.0, CVE-2012-3152 and CVE-2012-3153 have a CVSS base score of 6.4. CVE-2011-1411 has a CVSS base score of 5.8. CVE-2012-0106, CVE-2012-3183, CVE-2012-3185 and CVE-2012-3186 have a CVSS base score of 4.9. CVE-2012-3175, CVE-2012-0518, CVE-2012-3194, CVE-2012-1686, CVE-2012-0071, CVE-2012-0093 and CVE-2012-3184 have a CVSS base score of 4.3. CVE-2012-3193, CVE-2012-0086, CVE-2012-0090, CVE-2012-0092 and CVE-2012-0108 have a CVSS base score of 3.5. CVE-2012-0095, CVE-2012-3214, CVE-2012-3217 and CVE-2012-5065 have a CVSS base score of 2.1.
Oracle E-Business Suite
9 vulnerabilities are reported for “Oracle E-Business Suite” and 6 of them may be remotely exploitable without authentication. The highest CVSS score of these vulnerabilities is 6.4. Affected components are “Oracle Human Resources“, “Oracle Applications Technology Stack“, “Oracle iRecruitment“, “Oracle Application Object Library“, “Oracle iStore“, “Oracle Field Service“, “Oracle Marketing” and “Oracle Applications Framework“.
CVE-2012-3196 has a CVSS base score of 6.4. CVE-2012-3171 and CVE-2012-3222 have a CVSS base score of 5.0. CVE-2012-3139, CVE-2012-3138 and CVE-2012-5058 have a CVSS base score of 4.3. CVE-2012-3148 and CVE-2012-3164 have a CVSS base score of 3.5. CVE-2012-3162 has a CVSS base score of 1.7.
Oracle Supply Chain Products Suite
9 vulnerabilities are reported for “Oracle Supply Chain Products Suite” and 4 of them may be remotely exploitable without authentication. The highest CVSS score of these vulnerabilities is 5.5. Affected components are “Oracle Agile PLM For Process“, “Oracle Agile PLM Framework” and “Oracle Agile Product Supplier Collaboration for Process“.
CVE-2012-3140 and CVE-2012-5092 have a CVSS base score of 5.5. CVE-2012-5094 has a CVSS base score of 5.0. CVE-2012-3161, CVE-2012-5093 and CVE-2012-5091 have a CVSS base score of 4.3. CVE-2012-3154, CVE-2012-3200 and CVE-2012-5090 have a CVSS base score of 4.0.
Oracle PeopleSoft Products
9 vulnerabilities are reported for “Oracle PeopleSoft Products” and 1 of them may be remotely exploitable without authentication. The CVSS score of this vulnerability is 4.3. Affected component are “PeopleSoft Enterprise PeopleTools” and “PeopleSoft Enterprise Campus Solutions“.
CVE-2012-3182 has a CVSS base score of 4.3. CVE-2012-3201, CVE-2012-3195, CVE-2012-3198 and CVE-2012-3181 have a CVSS base score of 4.0. CVE-2012-3188, CVE-2012-3176 and CVE-2012-3179 have a CVSS base score of 3.5. CVE-2012-3191 has a CVSS base score of 2.1.
Oracle Siebel CRM
2 vulnerabilities are reported for “Oracle Siebel CRM” and 1 of them may be remotely exploitable without authentication. The CVSS score of this vulnerability is 4.3. Affected component is “Siebel UI Framework“.
CVE-2012-3230 has a CVSS base score of 4.3. CVE-2012-3229 has a CVSS base score of 4.0.
Oracle Industry Applications
2 vulnerabilities are reported for “Oracle Industry Applications” and 1 of them may be remotely exploitable without authentication. The highest CVSS score of these vulnerabilities is 6.8. Affected components are “Oracle Central Designer” and “Oracle Clinical/Remote Data Capture“.
CVE-2012-5066 has a CVSS base score of 6.8. CVE-2012-1763 has a CVSS base score of 4.0.
Oracle Financial Services Software
13 vulnerabilities are reported for “Oracle Financial Services Software” and 1 of them may be remotely exploitable without authentication. The highest CVSS score of these vulnerabilities is 5.5. Affected components are “Oracle FLEXCUBE Universal Banking” and “Oracle FLEXCUBE Direct Banking“.
CVE-2012-3226 has a CVSS base score of 5.5. CVE-2012-5063 has a CVSS base score of 5.0. CVE-2012-3228 has a CVSS base score of 4.9. CVE-2012-3141 and CVE-2012-5061 have a CVSS base score of 4.0. CVE-2012-3225 has a CVSS base score of 3.6. CVE-2012-3142, CVE-2012-3157, CVE-2012-3224, CVE-2012-3227 and CVE-2012-5064 have a CVSS base score of 3.5. CVE-2012-3223 has a CVSS base score of 2.1. CVE-2012-3145 has a CVSS base score of 1.5.
Oracle Sun Products Suite
18 vulnerabilities are reported for “Oracle Sun Products Suite” and 1 of them may be remotely exploitable without authentication. The highest CVSS score of these vulnerabilities is 7.8. Affected components are “Solaris“, “Oracle GlassFish Server“, “Sun GlassFish Enterprise Server“, “Sun Java System Application Server“, “SPARC T3“, “Netra SPARC T3“, “SPARC T4” and “Netra SPARC T4“.
CVE-2012-3210 and CVE-2012-3189 have a CVSS base score of 7.8. CVE-2012-3199, CVE-2012-0217 and CVE-2012-3204 have a CVSS base score of 7.2. CVE-2012-3187 has a CVSS base score of 6.9. CVE-2012-3209 has a CVSS base score of 5.6. CVE-2012-3155 has a CVSS base score of 5.0. CVE-2012-3207 and CVE-2012-3208 have a CVSS base score of 4.9. CVE-2012-3212 has a CVSS base score of 4.7. CVE-2012-3211 has a CVSS base score of 4.6. CVE-2012-5095 has a CVSS base score of 4.4. CVE-2012-3165 has a CVSS base score of 3.6. CVE-2012-3206, CVE-2012-3203 and CVE-2012-3205 have a CVSS base score of 2.1. CVE-2012-3215 has a CVSS base score of 1.7.
Oracle Virtualization
2 vulnerabilities are reported for “Oracle Virtualization” and 1 of them may be remotely exploitable without authentication. The highest CVSS score of these vulnerabilities is 4.3. Affected components are “Secure Global Desktop” and “Oracle VM Virtual Box“.
CVE-2012-1685 has a CVSS base score of 4.3. CVE-2012-3221 has a CVSS base score of 2.1.
Oracle MySQL
14 vulnerabilities are reported for “Oracle MySQL” and 2 of them may be remotely exploitable without authentication. The highest CVSS score of these vulnerabilities is 9.0. Affected components are “MySQL Server“.
CVE-2012-3163 has a CVSS base score of 9.0. CVE-2012-3158 has a CVSS base score of 7.5. CVE-2012-3177 has a CVSS base score of 6.8. CVE-2012-3147 has a CVSS base score of 6.4. CVE-2012-3166, CVE-2012-3173, CVE-2012-3144, CVE-2012-3150 and CVE-2012-3180 have a CVSS base score of 4.0. CVE-2012-3149, CVE-2012-3156, CVE-2012-3167 and CVE-2012-3197 have a CVSS base score of 3.5. CVE-2012-3160 has a CVSS base score of 2.1.