Symantec, Kaspersky Labs, Trend Micro, Sophos and other security vendors continue to surf on the Java 0day targeted attack stuff.
The vendors have agreed, in communion, that Java 0day was potentially used by the Chinese Nitro gang, through spear-phishing campaign. Nitro gang is well-known since another targeted campaign in 2011, reported by Symantec, focusing on organizations in the United States, Bangladesh and U.K.
Nitro gang, potentially the source of the newly discovered Java 0day, is using IP addresses and other characteristics that were common from the 2011 targeted attack, like the same C&C (223.25.233.244 for example) and the same files (“Flash_update.exe” for example).
For Kaspersky Labs, “the attacks have been going on for more than a week“. For Symantec, “the attackers have been using this zero-day for several days since August 22“. For Trend Micro, “Nitro attackers were continuing to send out emails to their targets with direct links to Poison Ivy executables in early August 2012“.
As all the vendors agree on the time frame and the source of the attack, we will take a look on all information’s we can gather around this story.
First C&C server
The first known C&C was “223.25.233.244“, also used in the 2011 campaign. I reported in my previous blog post, that the IP address was well-known since many months. As you will see here under the C&c server is well-known, dropping lot of malwares, with various domain names.
All information’s gathered on this C&C server:
2012-04-18 – Malwr.com Analysis (2819365de89a5e07c2c20b2b462a3487): Analyzed file was “upgrade.exe“, with DNS request to “who.hzlo.net” aka “223.25.233.244“.
2012-04-20 – Malwr.com Analysis (156d00c795d6d2857fd49f570e894803): Analyzed file was “upgrade.exe“, with DNS request to “who.hzlo.net” aka “223.25.233.244“.
2012-04-24 – Malwr.com Analysis (af6d20abc953e18a84beac84ea87fce3): Analyzed file was “Flash_updata.exe” with DNS request to “who.hzlo.net” aka “223.25.233.244“.
2012-04-25 – Malwr.com Analysis (ac1066eeab14150e2ed20e88d8ca1acb): Analyzed file was “flash_updata.exe” with DNS request to “who.hzlo.net” aka “223.25.233.244“.
2012-06-21 – Malwr.com Analysis (d0d335fbc6d9fdbaf8a0af44ae2944c7): Analyzed file was “update.exe” with DNS request to “goodluck.betr.co” aka “223.25.233.244“.
2012-06-25 – URL Query Analysis (75475): Analyzed URL was “http://admin.fcph.org” aka “223.25.233.244“.
2012-06-26 – URL Query Analysis (75932): Analyzed URL was “http://admin.fcph.org” aka “223.25.233.244“.
2012-07-10 – URL Query Analysis (86487): Analyzed URL was “http://ok.icon.pk” aka “223.25.233.244“. Domain name used during the Java 0day discovery, coincidence ?
2012-07-11 – URL Query Analysis (87414): Analyzed URL was “http://domain.rm6.org” aka “223.25.233.244“.
2012-08-17 – Sophos Analysis (Troj/Agent-XNE): DNS request to “hello.icon.pk” and “admin.fcph.org” aka “223.25.233.244“.
2012-08-20 – Malwr.com Analysis (e2fc730981c1c9c55b961bbbd609c6d3): Analyzed file was “KB2690533.exe” with DNS request to “ok.icon.pk” aka “223.25.233.244“. Interesting “KB2690533.exe” binary name we will search later same occurrences.
2012-08-27 – Malwr.com Analysis (1360ac6d139f19d590bd3b05fa12c8c0): Analyzed file was “upgrade.exe” with DNS request to “admin.fcph.org” aka “223.25.233.244“.
2012-08-27 – URL Query Analysis (147268): Analyzed URL was “http://223.25.233.244“.
2012-08-27 – URL Query Analysis (147552): Analyzed URL was “http://wagoo.fcph.org” aka “223.25.233.244“.
2012-08-27 – Malwr.com Analysis (4a55bf1448262bf71707eef7fc168f7d): Analyzed file was “hi.exe“, the famous one, with DNS request to “ok.icon.pk” aka “223.25.233.244“.
2012-08-27 – Malwr.com Analysis (c0c81cf499136515e22f39e70ef78eec): Analyzed file was “antivirus.exe” with DNS request to “ok.icon.pk” aka “223.25.233.244“, and two HTTP requests to “http://ok.icon.pk/4213538n.txt” and “http://ok.icon.pk/4214189n.txt“.
First reported infected server
The first reported infected server was “ok.aa24.net” with “59.120.154.62” IP address. The related infection URL was “ok.XXXX.net/meeting/index.html” with malicious loaded “applet.jar“. The IP address is located in Singapore. I also reported, in my previous blog post, that the IP address was well known since many months.
Second reported infected server
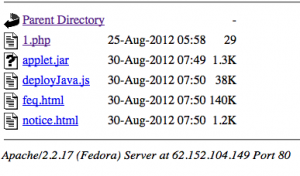
The second reported, by Symantec the 30 August, infected server was “62.152.104.149“. The related infection URL was “62.152.104.XXX/public/meeting/index.html” with malicious loaded “applet.jar“. The IP address is located in Italia.
Until the 30 August, “index.html” file, present on the second infected server, was an obfuscated JavaScript charging the malicious Java 0day “applet.jar” aka “cve2012xxxx.Gondvv.class” and the Poison Ivy backdoor “Flash_update.exe“. The “index.html” file was part of Gondad exploit kit, like as for the first infected server.
URL Query report that “62.152.104.149” is known since the 2012-08-24 with the same malicious URL. The date is corresponding on the “Last modified” date reported by the infected server. All the files have the 2012-08-24 date, except “1.php“.
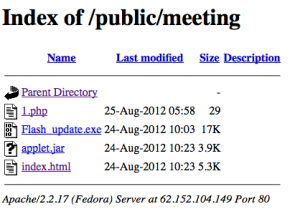
If you browse the server indexed directories, you can find a Rhino exploit “index.jar“, how is available since 2012-03-16.

I you continue to browse the directories, you can also find CVE-2010-3856 Linux exploit “glibc.sh“, used to backdoor the server. These files date are 2011-11-29.
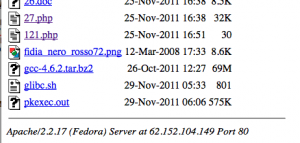
As you have seen, all the screenshots were taken the 29 August. I have monitor the server and the files present in the “/public/meeting” directory have change the 30 August, with a new variant of “applet.jar” and some new files like “feq.html” (VirusTotal analysis / Malwr.com analysis). Malwr.com analysis reported a new C&C server aka “12.163.32.15“, how is actually down.
KB2690533.exe C&C dropped binary
The 20 August “KB2690533.exe” file was dropped, from the C&C server, and we can find some additional information’s regarding the file name.
2012-08-16 – URL Query Analysis (133150): Analyzed URL was “http://erp.claridy.com.tw/rndy/download.war/KB2690533.exe” aka “211.72.230.236“.
2012-08-17 – Cisco Threat Outbreak Alert: “significant activity related to spam e-mail messages that claim to contain a Security Update for the recipient”. What mean significant ? The spam e-mail message text is looking similar to the spam e-mail message reported by Trend Micro the 30 August. Coincidence, we will see that it is not a coincidence.
Subject: Security Update
Message Body:
Dear,
Because of the office network interfaces changed.Please download the Security Update fot windows XP (KB2690533),and install it. Download address: hxxp://www.microsoft.com/en-us/download/KB2690533.exe
Also the following Chinese web site is reporting some URLs the 2012-08-21 and we can find “http://erp.claridy.com.tw/rndy/download.war/KB2690533.exe“, “http://erp.claridy.com.tw/rndy/download.war/Flash_update.exe” and “http://haitimissionschool.org/updateflashplayer.exe“.
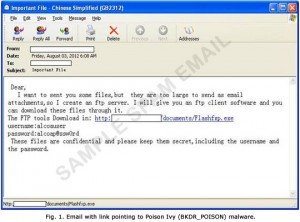
Spam e-email message reported by Trend Micro
In his blog post Trend Micro is reporting some typical spam e-mail message with direct links to Poison Ivy executable in early August 2012.
As you can see this email message is in the same style as the message detected by Cisco the 17 August.
If we search on the username string “alcoauser“, we can find some additional information’s:
2012-08-02 – Another Cisco Threat Outbreak Alert: “significant activity related to spam e-mail messages” with exactly the same content as the content provided by Trend Micro and we can find the “59.120.154.62” server where the 0day was discovered.
Other e-mail message spotted by a Chinese website
In his blog post Trend Micro is reporting another e-email how was spotted in April 2012.
Dear,
If you already have VPN installed on your computer, you’ll be asked to download and install update the next time you start VPN. Once the new update is installed, VPN should function normally.
Download and install the updated:http://www.cisco.com/vpn/upgrade.exe
You must have administrative privileges on your computer to install any VPN client. Please contact your desktop support staff if you need assistance. Morris Kristi
[email protected]
This e-mail message is in the same style as the previous e-mail messages. The malicious URL was “http://out.hzlo.net/update/upgrade.exe” with IP address “71.216.92.29“. This domain name and IP address were first spotted by ScumWare.orgthe 30 March. Another additional domain name was reported “http://adobe.flash-mail.tk/update/Flash_updata.exe” on the same server the 24 April.
“out.hzlo.net” domain name was spotted by 04 April by Clean MX realtime database, but if you take a look on the complete “*.hzlo.net” domain names, you can see that “http://jack.hzlo.net/download/antivirus.exe” was catched the 23 February !
More interesting, the characteristic of the Java 0day spreading was URL like “/public/meeting/index.html” or “/meeting/index.html“. Clean MX realtime database report this URL for the first time for “http://jack.hzlo.net/meeting/index.html” the 02 July.
Conclusion
If they’re was an active targeted Nitro campaign, this campaign has start during February 2012 with different infection vectors. The campaign has been catched many times by different security researchers and vendors, but nobody has raise the alert flag until end of August. I think that nobody has care on the pseudo earlier catched “targeted” campaign, and that the Java 0day was the alert flag.
Second opinion, I really think that the Java 0day was out for a minimum of 2 or 3 months before his public discovery.
And last but not least opinion, I still continue to believe that it was not so targeted as the vendors try to make us believe.