In my last blog post I reported you that the watering hole attack, involving an Internet Explorer 0day, was not limited to CFR.org, but also to energy manufacturer Capstone Turbine Corp. I also confirmed you that the attack has start minimum beginning December, and that some of these infected web sites were also previously infected with another Internet Explorer 0day discovered in September 2012.
After some additional researches I found two new web sites involved in the watering hole attack.
PHIL-AM Tour (http://www.philam.com.tw)
This web site, a Taiwanese travel agency, has been found infected through a Google dork and the “Helps.html” page is still in Google cache, but the web site has been cleaned. You can find the source code of the infected page on Pastebin. This web page was also analyzed trough jsunpack the 31 December.
Uygur Haber Ajansi (www.uygurunsesi.com)
This web site, a dissident Uygur web site, has been found infected through a Google dork and the “Helps.html” page is live. So take care if you visite this web site, you could be infected. Uygur are a Turkic ethnic group living in Eastern and Central Asia. Today, Uyghurs live primarily in the Xinjiang Uyghur Autonomous Region in the People’s Republic of China.
Same as for Capstone Turbine Corp. web site, this web site was also previously infected by CVE-2012-4969 I discovered in September. “Grumgog.swf” is in the house.
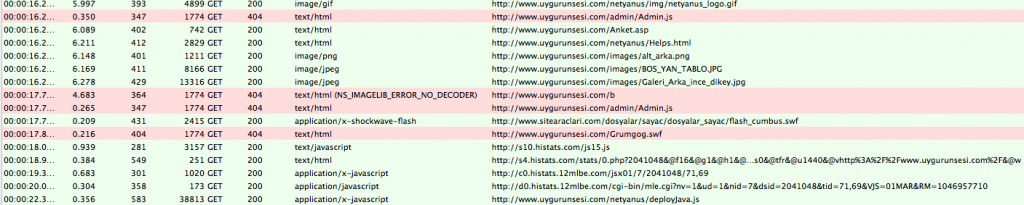
Samples collected on this web site:
- robots.txt (96b01d14892435ae031290cd58d85c2e)
- today.swf (4df26a39734992ff7a8d95cc44542b2b)
- xsainfo.jpg (7c713c44e34fa8e63745744e3b7221db)
- news.html (76d14311bae24a40816e3832b1421dee)
- Helps.html (a25c13d4edb207e6ce153469c1104223)
RT @eromang: Chinese Uygur Minority Also Targeted in the #CFR Watering Hole Attack And More http://t.co/jJ1jxGT4 #infosec #0day
RT @eromang: Chinese Uygur Minority Also Targeted in the #CFR Watering Hole Attack And More http://t.co/jJ1jxGT4 #infosec #0day
RT @eromang: Chinese Uygur Minority Also Targeted in the #CFR Watering Hole Attack And More http://t.co/jJ1jxGT4 #infosec #0day
RT @eromang: Chinese Uygur Minority Also Targeted in the #CFR Watering Hole Attack And More http://t.co/jJ1jxGT4 #infosec #0day