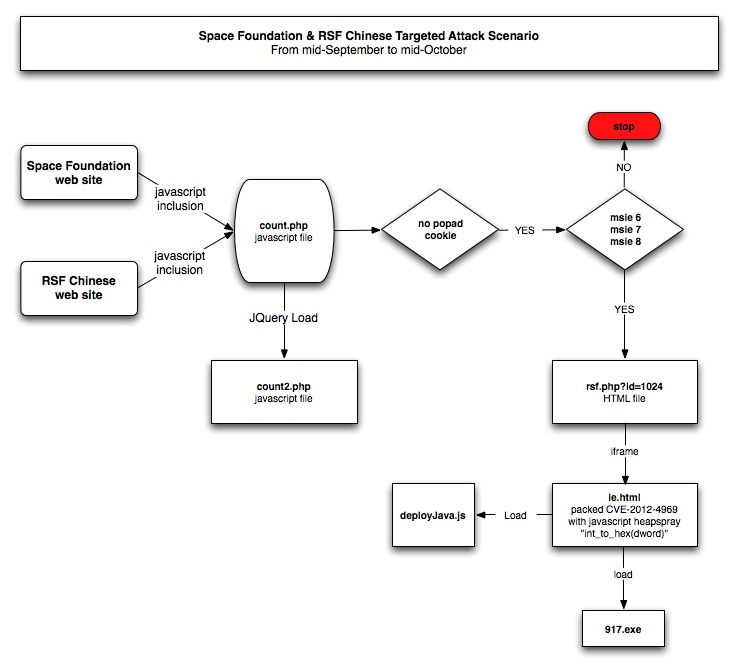
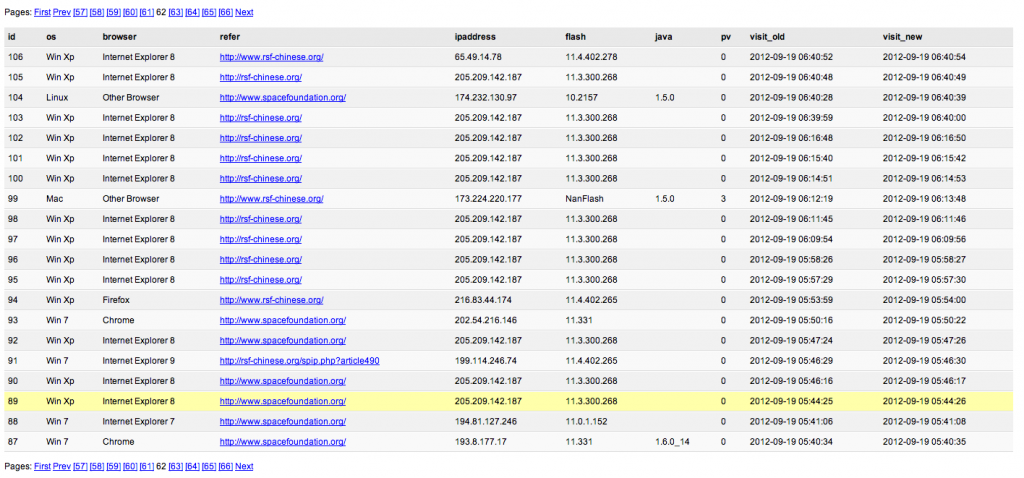
Microsoft has release, the 12 February 2013, during his February Patch Tuesday, one updated security advisory and twelve security bulletins. On the twelve security bulletins five of them have a Critical security rating.
Microsoft Security Advisory 2755801
MSA-2755801,released during September 2012, has been updated. The security advisory is regarding updates for vulnerabilities in Adobe Flash Player in Internet Explorer 10. Update KB2805940 has been released for supported editions of Windows 8, Windows Server 2012, and Windows RT. The update addresses the vulnerabilities described in Adobe Security bulletin APSB13-05.
MS13-009 – Cumulative Security Update for Internet Explorer
MS13-009 security update, classified as Critical, allowing remote code execution, is the fix for 13 reported vulnerabilities. CVE-2013-0015 (4.3 CVSS base score) was discovered and reported by Masato Kinugawa. CVE-2013-0018 (9.3 CVSS base score) and CVE-2013-0022 (9.3 CVSS base score) were discovered and privately reported by Omair. CVE-2013-0019 (9.3 CVSS base score) was discovered and privately reported by SkyLined, working with HP’s Zero Day Initiative. CVE-2013-0020 (9.3 CVSS base score) was discovered and privately reported by Arthur Gerkis, working with the Exodus Intelligence, and by Stephen Fewer of Harmony Security. CVE-2013-0021 (9.3 CVSS base score) was discovered and privately reported by Tencent PC Manager. CVE-2013-0023 (9.3 CVSS base score) was discovered and privately reported by Arthur Gerkis, working with HP’s Zero Day Initiative. CVE-2013-0024 (9.3 CVSS base score) was discovered and privately reported by an anonymous researcher, working with HP’s Zero Day Initiative. CVE-2013-0025 (9.3 CVSS base score) and CVE-2013-0028 (9.3 CVSS base score) were discovered and privately reported by Scott Bell of Security-Assessment.com. CVE-2013-0026 (9.3 CVSS base score) was discovered and privately reported by Jose A Vazquez of Yenteasy Security Research, working with the Exodus Intelligence. CVE-2013-0027 (9.3 CVSS base score) was discovered and privately reported by Mark Yason of IBM X-Force. CVE-2013-0029 (9.3 CVSS base score) was discovered and privately reported by Stephen Fewer of Harmony Security and [email protected], working with HP’s Zero Day Initiative.
MS13-010 – Vulnerability in Vector Markup Language Could Allow Remote Code Execution
MS13-010 security update, classified as Critical, allowing remote code execution, is the fix for one privately reported vulnerability. CVE-2013-0030 (9.3 CVSS base score) was discovered and privately reported by an unknown security researcher.
MS13-011 – Vulnerability in Media Decompression Could Allow Remote Code Execution
MS13-011 security update, classified as Critical, allowing remote code execution, is the fix for one publicly reported vulnerability. CVE-2013-0077 (9.3 CVSS base score) was discovered and reported by Tencent Security Team.
MS13-012 – Vulnerabilities in Microsoft Exchange Server Could Allow Remote Code Execution
MS13-012 security update, classified as Critical, allowing remote code execution, is the fix for two publicly reported vulnerability linked to Oracle Outside In vulnerabilities fixed during January 2013 Critical Patch Update. These vulnerabilities are CVE-2013-0418 (6.8 CVSS base score) and CVE-2013-0393 (6.8 CVSS base score).
MS13-020 – Vulnerability in OLE Automation Could Allow Remote Code Execution
MS13-020 security update, classified as Critical, allowing remote code execution, is the fix for one publicly reported vulnerability. CVE-2013-1313 (9.3 CVSS base score) was discovered and reported by an anonymous researcher, working with HP’s Zero Day Initiative.
MS13-013 – Vulnerabilities in FAST Search Server 2010 for SharePoint Parsing Could Allow Remote Code Execution
MS13-013 security update, classified as Important, allowing remote code execution, is the fix for two publicly reported vulnerability linked to Oracle Outside In vulnerabilities fixed during January 2013 Critical Patch Update. These vulnerabilities are CVE-2012-3214 (2.1 CVSS base score) and CVE-2012-3217 (2.1 CVSS base score).
MS13-014 – Vulnerabilities in FAST Search Server 2010 for SharePoint Parsing Could Allow Remote Code Execution
MS13-014 security update, classified as Important, allowing denial of service, is the fix for one privately reported vulnerability. CVE-2013-1281 (7.1 CVSS base score) was discovered and privately reported by an anonymous researcher.
MS13-015 – Vulnerability in .NET Framework Could Allow Elevation of Privilege
MS13-015 security update, classified as Important, allowing elevation of privileges, is the fix for one privately reported vulnerability. CVE-2013-0073 (10.0 CVSS base score) was discovered and privately reported by James Forshaw of Context Information Security.
MS13-016 – Vulnerabilities in Windows Kernel-Mode Driver Could Allow Elevation of Privilege
MS13-016 security update, classified as Important, allowing elevation of privileges, is the fix for 30 privately reported vulnerability. CVE-2013-1248 (4.9 CVSS base score) and CVE-2013-1249 (4.9 CVSS base score) were discovered and privately reported by Mateusz “j00ru” Jurczyk of Google Inc, and Tencent Security Team. CVE-2013-1251 (4.9 CVSS base score), CVE-2013-1252 (4.9 CVSS base score) and CVE-2013-1253 (4.9 CVSS base score) were discovered and privately reported by Gynvael Coldwind and Mateusz “j00ru” Jurczyk of Google Inc. CVE-2013-1250 (4.9 CVSS base score), CVE-2013-1254 (4.9 CVSS base score), CVE-2013-1255 (4.9 CVSS base score), CVE-2013-1256 (4.9 CVSS base score), CVE-2013-1257 (4.9 CVSS base score), CVE-2013-1258 (4.9 CVSS base score), CVE-2013-1259 (4.9 CVSS base score), CVE-2013-1260 (4.9 CVSS base score), CVE-2013-1261 (4.9 CVSS base score), CVE-2013-1262 (4.9 CVSS base score), CVE-2013-1263 (4.9 CVSS base score), CVE-2013-1264 (4.9 CVSS base score), CVE-2013-1265 (4.9 CVSS base score), CVE-2013-1266 (4.9 CVSS base score), CVE-2013-1267 (4.9 CVSS base score), CVE-2013-1268 (4.9 CVSS base score), CVE-2013-1269 (4.9 CVSS base score), CVE-2013-1270 (4.9 CVSS base score), CVE-2013-1271 (4.9 CVSS base score), CVE-2013-1272 (4.9 CVSS base score), CVE-2013-1273 (4.9 CVSS base score), CVE-2013-1274 (4.9 CVSS base score), CVE-2013-1275 (4.9 CVSS base score), CVE-2013-1276 (4.9 CVSS base score) and CVE-2013-1277 (4.9 CVSS base score) were discovered and privately reported by Mateusz “j00ru” Jurczyk of Google Inc.
MS13-017 – Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege
MS13-017 security update, classified as Important, allowing elevation of privileges, is the fix for three privately reported vulnerability. CVE-2013-1278 (7.2 CVSS base score) and CVE-2013-1279 (7.2 CVSS base score) were discovered and privately reported by Gynvael Coldwind and Mateusz “j00ru” Jurczyk of Google Inc. CVE-2013-1280 (7.2 CVSS base score) was discovered and privately reported by an unknown security researcher.
MS13-018 – Vulnerability in TCP/IP Could Allow Denial of Service
MS13-018 security update, classified as Important, allowing denial of service, is the fix for a privately reported vulnerability. CVE-2013-0075 (7.1 CVSS base score) was discovered and privately reported by an unknown security researcher.
MS13-019 – Vulnerability in Windows Client/Server Run-time Subsystem (CSRSS) Could Allow Elevation of Privilege
MS13-019 security update, classified as Important, allowing elevation of privileges, is the fix for a publicly reported vulnerability. CVE-2013-0076 (7.2 CVSS base score) was discovered and privately reported by Max DeLiso.